Pwn2Own Contest Yields 13 Bugs, As Virtual Format Expands Talent Pool
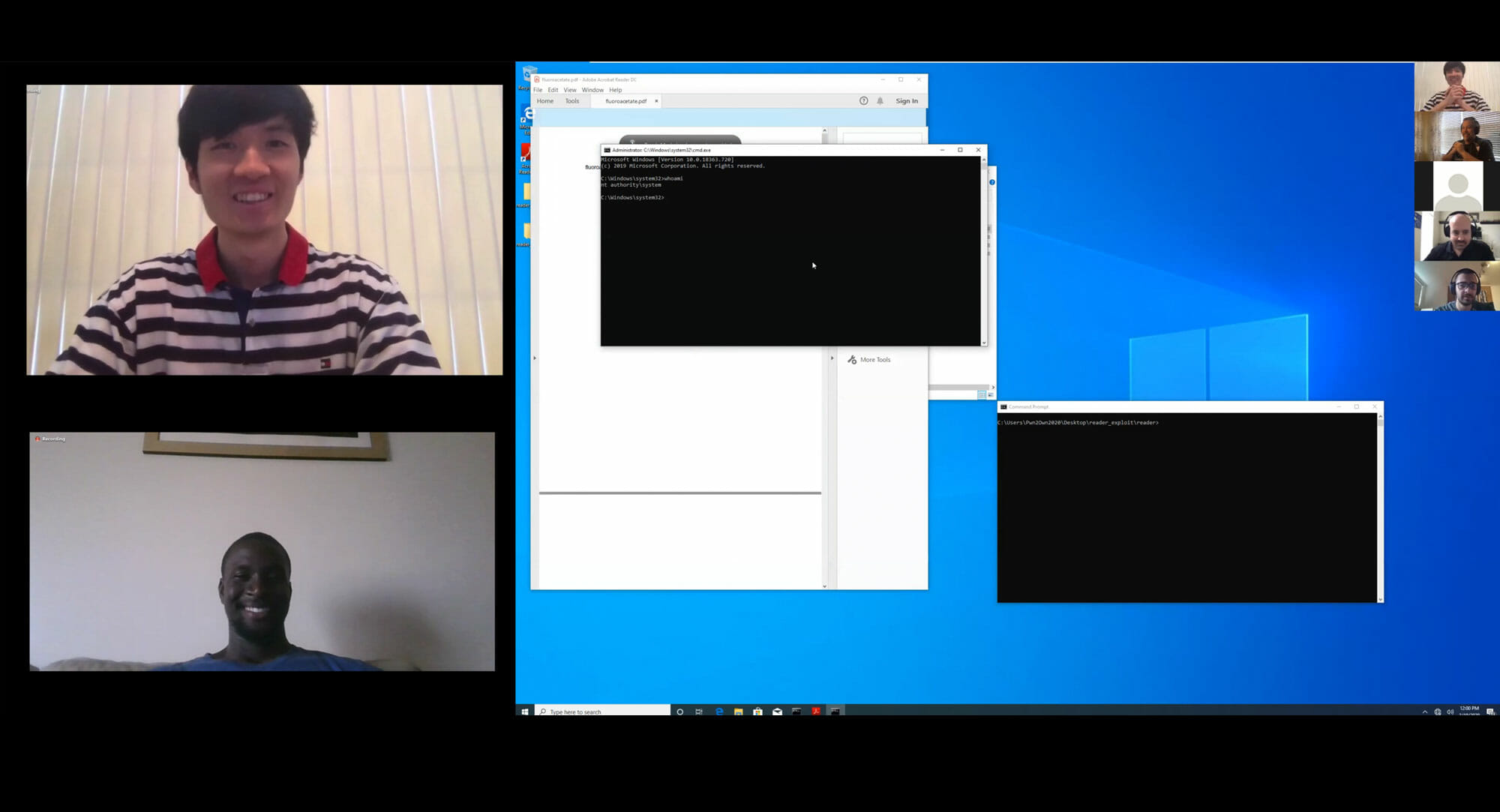
Research teams at the Pwn2Own 2020 competition successfully exploited 13 software vulnerabilities this past week, including bugs found in products from Adobe, Apple, Microsoft, Oracle and Ubuntu. Participants earned $270,000 over the two-day event — the first Pwn2Own ever to be held virtually, as a measure to combat the rapid spread of the novel coronavirus.
Richard Zhu and Amat Cama of Fluoroacetate repeated from last year and were once again crowned Masters of Pwn. On day one, the team demonstrated a use-after-free (UAF) bug in Microsoft Windows and exploited it to escalate privileges to SYSTEM. The next day, they paired UAF bugs in Windows and Adobe Reader to once again elevate to SYSTEM.
Other highlights included the chaining of six bugs to produce a macOS kernel escalation of privilege in Apple Safari, another Windows UAF flaw allowing the escalation of privileges to SYSTEM, a local privilege escalation in Ubuntu Desktop, and a two-bug combination in Oracle VirtualBox that enabled code execution on the host OS from the guest OS. Unofficially, the event also featured one additional flaw in VMware Workstation and another in Oracle VirtualBox, although they did not count toward the competition.
The decision to hold Pwn2Own virtually could have implications for future competitions, after organizers found that the move opened up the event to global participants who in previous years may not have been able to join.
Even though number of participants was slightly down from last year, a number of participants said they would not have been able to compete if the competition had been held in person, according to ZDI.
“Going virtual has certainly increased the playing field as far as who can participate,” Brian Gorenc, director of vulnerability research and head of the ZDI, told SC Media in an interview. “There are some researchers who would want to participate in the past, but travel restrictions or visa issues have prevented them from being at the contest in person. Going virtual allows us to accommodate those individuals. It’s something we’re going to consider in future competitions as well.”
The virtual format required some key rule and procedural changes. Competitors were asked to send out their exploits prior to the competition. Then ZDI researchers — based in Austin, Texas rather than at the CanSecWest security conference Vancouver, Canada as originally scheduled — ran the exploit code while the competitors watched remotely. “They had to trust that we wouldn’t alter or adversely impact their research, so it was a big leap of faith on their part,” said Gorenc.
“Probably the biggest challenge was making sure we run the contest fairly,” Gorenc added. “We pride ourselves on being impartial arbiters. Once we determined how we could adjudicate the contest in a manner that was equitable to researchers, vendors and ZDI alike, we knew we could actually make a virtual competition happen.”
READ MORE HERE
