Overview: OWASP Top 10 2021
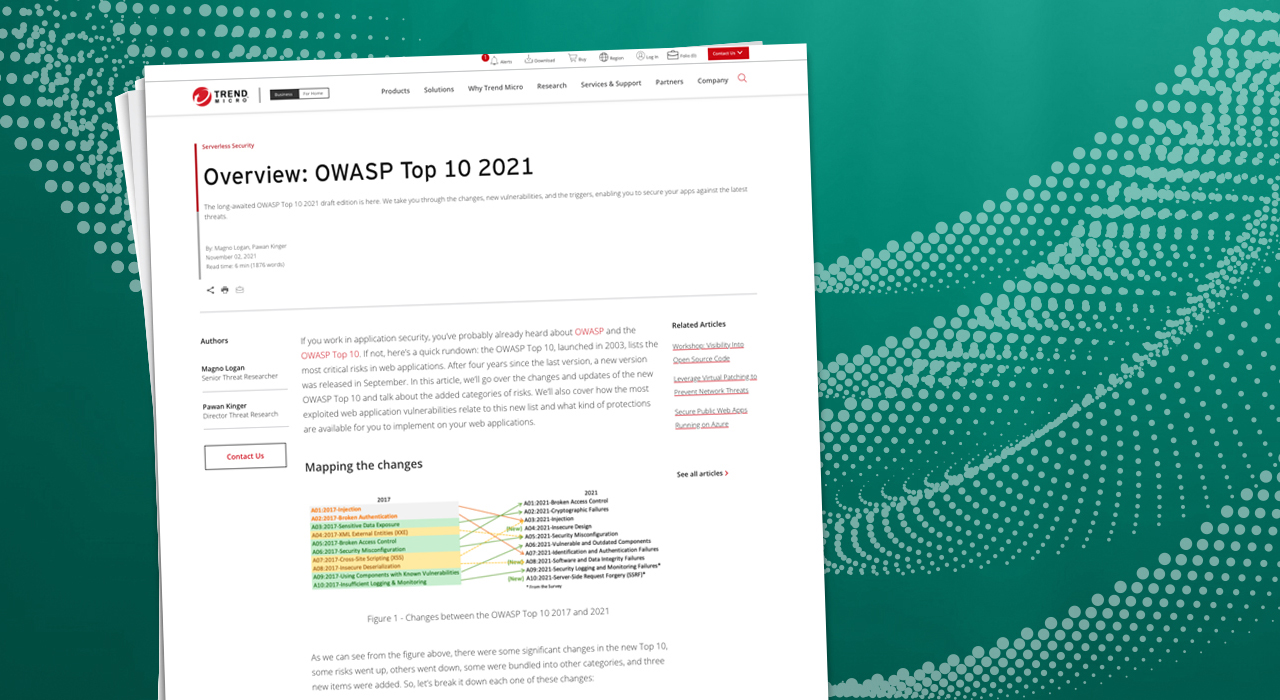

Table 1 – The top 15 vulnerabilities with known exploits or proofs of concept and related Top 10 risks
How to secure code via application security and testing
Now, let’s focus on how to secure your apps from these vulnerabilities. This can be tricky given you can have tens, hundreds, or maybe thousands of developers writing and deploying code every day in your production environment.
First, organizations must ensure that all communications are being made using TLS encryption. This should be applied even among internal services like load balancers, application servers, and databases.
Organizations can significantly reduce the attack surface of their systems just by limiting and monitoring exposed services, ports, and API endpoints. Here, it is essential to think about container base images and the systems on which its clusters are running.
There are various code security verifications to add to your pipeline to ensure that one’s code is secured:
Static application security analysis (SAST) – This is also called “security code review” or “code auditing” and is still one of the best and quickest ways to detect security issues in one’s code. Enterprises should have at least one static analysis tool embedded into the pipeline regardless of the language being used. This tool will check for unsafe coding practices every time developers commit new code into the application. In addition, the OWASP Foundation has a list of open-source and commercial tools designed to analyze source code or compiled code to detect security flaws.
Dynamic application security analysis (DAST) – Although dynamic analysis can only be done when there is a running application to test against, it is also a good idea to perform automated scans and checks to test for common application attacks such as SQL injection, XSS attacks, and cross-site request forgery (CSRF) attacks. These tools will also test your application, container, and cluster resilience when faced with a series of unexpected load and malformed requests. In addition, OWASP has a dynamic analysis tool that can also be automated and embedded into the pipeline called OWASP Zed Attack Proxy (ZAP).
Software composition analysis (SCA) – Between 70% and 90% of all cloud-native applications are made of libraries or third-party dependencies. These codes are generally not checked during the static analysis phase. However, tools like the OWASP Dependency-Check can be used to check for outdated or vulnerable libraries in one’s code. Trend Micro Cloud One™ – Open Source Security by Snyk provides cloud-native application security via continuous monitoring and identifying open-source code vulnerabilities and license risks in application components.
Runtime Application Self-Protection (RASP) – RASP is a robust application security tool that kicks in when an application starts, providing real-time or immediate protection against threats and attacks, such as zero-day exploits, XSS attacks, and email and messaging app attacks. RASP not only detects attacks but also analyzes the attacks’ behavior and the context of the behavior. This means that it can correctly pinpoint legitimate requests from attacks, minimizing false positives and gray alerts. Trend Micro Cloud OneTM – Application Security offers RASP, allowing developers to design and deploy secure applications and protect against sophisticated attacks quickly and efficiently.
Patching and ensuring that proper configurations are set are separate tracking items. The responsibility for these rests with the application owners and their application security teams. DAST and penetration testing are usually helpful in identifying vulnerabilities and configuration issues. In addition, enterprises can deploy systems that can prevent such from happening or perform virtual patching, such as a web application firewall (WAF) or an IPS.
Conclusion
Securing your modern apps against today’s most dangerous vulnerabilities doesn’t have to be complicated, but it does require some care. Learn more about how a platform approach can automate and streamline security from build time to runtime by checking out the robust Trend Micro Cloud One documentation site. If you’re ready to try it for yourself, get started with a free, 30-day trial.
Read More HERE



