Only 6 ransomware attacks on the UK’s NHS since WannaCry worm hit in 2017 – report
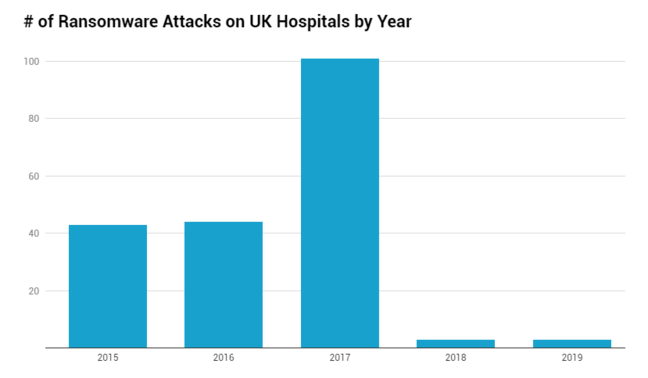
The NHS has suffered 209 successful ransomware attacks since 2014, according to new figures based on Freedom of Information requests, but with a dramatic improvement since 2017, the year WannaCry ransomware hit the health service.
The figures, posted in a report from research company Comparitech, show the following since 2014:
- 209 or more successful attacks, ranging from one computer to an entire system
- No ransoms reported to have been paid
- Estimated downtime of 206 days
- Only six attacks reported after 2017, the year of WannaCry, albeit with the caveat that
- 20 per cent of hospitals refused or failed to respond to the survey
The researchers surveyed 254 NHS Trusts, with 184 responding, 20 not responding and 50 refusing to hand over the information requested.
The WannaCry attack in 2017 – famously thwarted by Brit white hat hacker Marcus Hutchins – caused a spike to 101 incidents and we know many of these were severe. A September 2018 government report (PDF) estimates the cost of lost output and IT support caused by WannaCry, aka WannaCrypt, to be £92m – most of it in the aftermath rather than during the attack, for restoring data and systems.
What did the NHS do to improve its security? Following WannaCry, there was a “Lessons learned” review (PDF). The WannaCry incident was in May 2017, and the review noted: “None of the 80 NHS organisations affected by WannaCry had applied the Microsoft update patch21 advised by NHS Digital’s CareCERT bulletin on 25 April 2017 following the receipt of intelligence of a specific threat from BT on 24 April 2017.”
Some PCs running the unsupported and ancient Windows XP were compromised, but “the majority of NHS devices infected were running the supported, but unpatched, Microsoft Windows 7”. Since then, Windows 7 too has largely gone out of support. The review made numerous common-sense recommendations.
The September 2018 report states that NHS trusts have been asked to meet the Cyber Essentials Plus government standard. In addition, IBM was contracted to deliver a Cyber Security Operations Centre for monitoring and responding to threats, and a new Microsoft agreement included licences for Windows 10 and for Microsoft’s Advanced Threat Protection.
There are 22 recommendations including mandatory “cyber awareness training” for staff and a suggestion that “all organisations should consider whether access to IT systems and services should be removed from members of staff who have not successfully completed this mandatory training”.
Based on these figures, WannaCry was an effective wake-up call. That said, Comparitech’s statistics are less valuable than they might be because the incidents are not weighted by their severity and scope. Ransomware is not going away, though. Last year Symantec reported (PDF) that while overall ransomware was down by 20 per cent, enterprise ransomware was up by 12 per cent. A recent Coveware report states that average ransomware payments increased by 104 per cent year on year for the fourth quarter of 2019. Ransomware is getting smarter and more expensive and remains a high risk. ®
Sponsored: Detecting cyber attacks as a small to medium business
READ MORE HERE