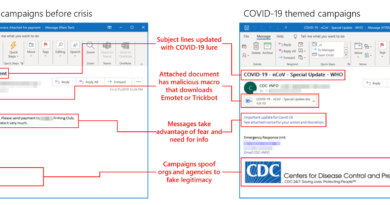
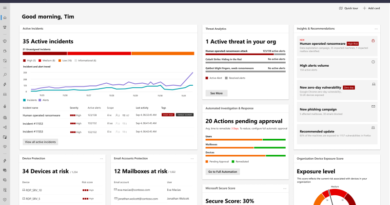
Modernizing the security operations center to better secure a remote workforce

The response to COVID-19 has required many security operations centers (SOCs) to rethink how they protect their organizations. With so many employees working remotely, IT groups are routing more traffic directly to cloud apps, rather than through the network. In this model, traditional network security controls aren’t enough. Endpoint signals and identity-based security matter more than ever.
Even under the best circumstances, managing and working in an SOC is stressful—and these aren’t normal times! We know you’re under a lot of pressure, with less visibility and concerns over balancing user productivity without compromising security. But we also know many of the changes companies have made to support remote work during this crisis will remain in place once the virus is gone—some have already announced more flexible and permanent remote work policies. In light of this new reality, the SOC will also need to adjust. In this blog, we’ve outlined some principles of the modern SOC which can guide that transition. You can also hear us discuss these concepts by viewing a replay of the 2020 Microsoft Virtual Security and Compliance Summit.
It’s a multi-cloud world
Odds are good your organization doesn’t use just one cloud. You may manage much of your infrastructure on Microsoft Azure, but you also probably use Amazon Web Services (AWS) or Google Cloud Platform (GCP) too. And when we say cloud, we don’t just mean infrastructure as a service (IaaS). We also mean development work on a platform as a service (PaaS) and software-as-a-service (SaaS) apps hosted in a cloud—although it’s not always clear which cloud it’s hosted on. Without visibility across all platforms where business information is stored and transacted, you don’t have a full view of your corporate security program and risk profile.
Although the major cloud service providers offer tools that let you monitor their environment extensively, you need a holistic view to correlate threats and assess how one threat may impact another resource. Solutions like Microsoft Cloud App Security give you tools to detect cloud apps and monitor and protect them, while Azure Sentinel collects and analyzes data across on-premises and in multiple clouds.
Visibility into all connected devices
As more employees use cloud apps and mobile devices for work, the traditional network security perimeter has lost relevance. This puts greater emphasis on endpoint monitoring and protection. But it goes beyond employee devices. There has been an explosion of the internet of things (IoT) across industries. The industrial internet of things (IIoT) and industrial control systems (ICS) provide yet another opportunity for bad actors to infiltrate your environment. Security platforms like Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) can help you prevent, detect, investigate, and respond to threats across all your endpoints. And Microsoft Defender ATP integrates with Microsoft Threat Protection to give you visibility across devices, identity, cloud apps, data, and infrastructure.
Humans and machine learning working together
Part of what makes this job so challenging is the sheer number of endpoints and environments that need to be monitored. Each of those entities produces thousands of alerts—not all of which are legitimate threats. If you are using several security tools that aren’t well integrated, correlating signals across your entire environment is tough. To find the real threats, you may spend hours combing through false positives. Alert fatigue is inevitable, making it easy to miss true issues.
In the modern SOC, artificial intelligence (AI) and machine learning (ML) will be deployed to help people focus on the right problems. If you’re worried that AI and ML will automate you out of a job, “help people” was the most important part of the previous sentence. We believe people are (and will continue to be) a necessary part of cyber defense work. AI and ML are simply not equipped to do the complex problem solving that people do. What AI and ML can do is reduce the noise, so that people can focus on responding to more complex threats and trying to uncover what the humans behind attacks are planning next.
In solutions like Azure Sentinel, AI and ML reason over massive amounts of data to better detect behavior that indicates compromise. Using probabilistic models, such as Markov Chain Monte Carlo simulations, Azure Sentinel takes low fidelity alerts and combines them into fewer actionable high-fidelity alerts, increasing the true positive rate to reduce analyst alert fatigue.
Gamification of security training
The core mission of the SOC is to identify compromise rapidly and respond to incidents. In the middle of an attack, minutes matter, so it’s critical that you respond quickly and intelligently. But these are also the moments when adrenaline runs high, and people panic. You may not make the best decisions in a state of high alert. To provide structure during an incident, it helps to have a plan.
A playbook includes a set of processes and steps for various triggers. Written playbooks provide you a reference in the heat of the moment. You can also automate playbooks using the security orchestration, automation, and response (SOAR) capabilities in solutions like Azure Sentinel.
Practicing your plan can help build muscle memory. In tabletop exercises, teams talk though how they would respond to specific scenarios in a low stress environment. When an actual attack occurs, they draw on these exercises to inform decision making.
To better engage participants, many SOCs are gamifying their training sessions. Capture the flag contests divide groups into a red team (the attackers) and a blue team (the defenders) and challenges them to defend (or capture) a computer system. Microsoft’s OneHunt brings together security professionals across the Microsoft organization to conduct a weeklong red team vs. blue team simulation. At the Ignite World Tour, Into the Breach was one of the most popular events. In this game, participants defended a system from an AI-generated attack using Azure Sentinel and Microsoft Threat Protection solutions. Activities like these let teams practice in a fast-moving situation that replicates the experience of a real attack, without the high stakes.
Learn more
It’s been a tough few months for technology teams supporting a rapid migration to remote work. As you begin to modernize your SOC for our new reality, the following resources may help:
For more information about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity. Or reach out to Diana on LinkedIn or Twitter.
READ MORE HERE