Microsoft: 58% of Nation-State Cyberattacks Come From Russia
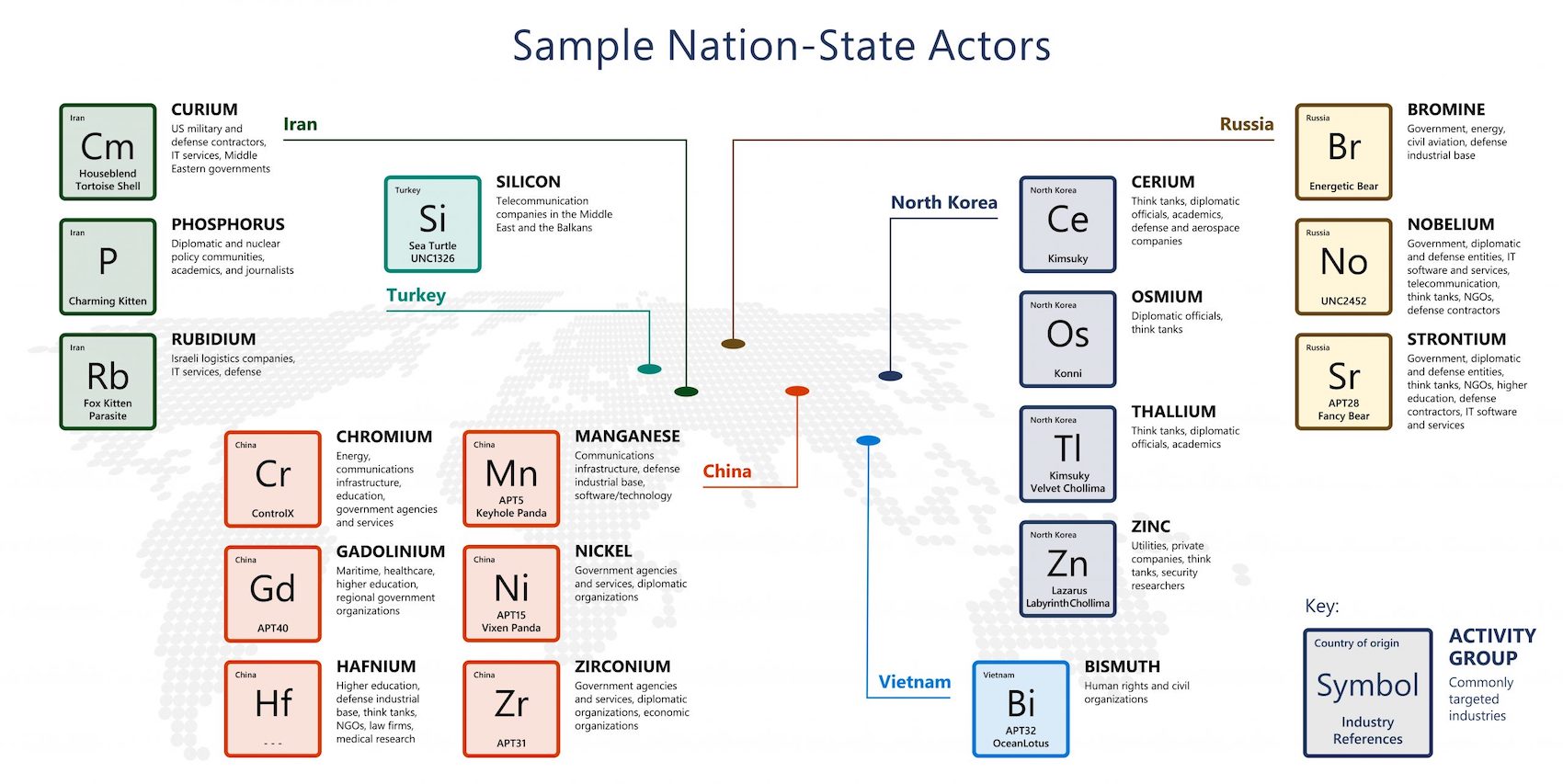
Russia is the source of the lion’s share of nation-state cyberattacks Microsoft has observed in the past year (58%), followed by North Korea (23%), Iran (11%), China (8%), and South Korea, Vietnam, and Turkey all with less than 1% representation, a new pool of data reveals.
This year’s Microsoft Digital Defense Report pulls from a wealth of data to highlight trends in nation-state threats, cybercriminal activity, hybrid workforce security, disinformation and Internet of Things (IoT), operational technology (OT), and supply chain security.
The data shows Russian nation-state attacks are “increasingly effective,” climbing from a 21% successful compromise rate last year to a 32% rate this year. They are also targeting more government agencies for intelligence gathering, a target that jumped from 3% of their victims last year to 53% in 2021. Russian nation-state actors primarily target the United States, Ukraine, and the United Kingdom, Microsoft data shows.
It also reveals Russia isn’t the only nation-state actor changing its approaches. Espionage is the most common goal among nation-state groups; however, attacker activity reveals different motivations in Iran, which quadrupled its targeting of Israel in the past year and launched destructive attacks, and North Korea, which targeted cryptocurrency companies for profit.
Nearly 80% of nation-state activity targeted enterprises; 21% targeted consumers. The most targeted sectors were government (48%), NGOs and think tanks (31%), education (3%), intergovernmental organizations (3%), IT (2%), energy (1%), and media (1%). Microsoft has alerted customers of nation-state attack attempts 20,500 times in the past three years.
The tools nation-state attackers use are often the same other criminals use to breach target networks. Nation-states may “create or leverage bespoke malware, construct novel password spray infrastructure, or craft unique phishing or social engineering campaigns,” Microsoft wrote in its report. Some, like China-linked Gadolinium, increasingly turn to open source tools or commonly used malware to target supply chains or launch man-in-the-middle or distributed denial-of-service (DDoS) attacks.
Cybercrime
On the cybercriminal front, data highlights how the growth of criminal activity is driven in large part by a supply chain that makes it easier for attackers. Stolen username and password pairs run for $0.97 per 1,000 (on average) or $150 for 400 million. Spear-phishing-for-hire can cost $100 to $1,000 per successful account takeover, and DDoS attacks are cheap for unprotected sites: roughly $300 USD per month.
Ransomware kits cost as little as $66 upfront, or 30% of the profit, and ransomware is striking everywhere. Microsoft reports the top five industries targeted in the past year, based on ransomware engagements with its Detection and Rapid Response Team, are consumer retail (13%), financial services (12%), manufacturing (12%), government (11%), and healthcare (9%).
Microsoft has seen two positive trends: First, companies and governments are more forthcoming in the aftermath of an attack, which has emphasized the threat to governments around the world. Second, as more governments around the world recognize cybercrime as a threat to national security, they have made fighting it a priority. More governments are passing new laws that focus on reporting, collaborating, and sharing resources to fight attacks.
Hybrid Workforce: Security Data and Challenges
All of these attack trends are unfolding as businesses navigate the future of hybrid and remote work after a rapid shift to work-from-home, which created new attack surfaces for criminals, and a year of major security incidents, including attacks on SolarWinds
and Colonial Pipeline, as well as those targeting on-premises Exchange Server vulnerabilities.
Internally, Microsoft is seeing a 50/50 split between people who want to work more from the office or more remotely, said CISO Bret Arsenault in an interview with Dark Reading. “That’s reflective of globally … different cultures, different home environments, different settings,” adding that “for digital transformation and zero-trust, this accelerates both of those in a really big way.”
And while progress has been made, businesses have a long way to go: Azure Active Directory sees 50 million password attacks daily, Microsoft reports, but only 20% of users and 30% of global admins use strong authentication such as multifactor authentication (MFA). Password-based attacks remain the main source of identity compromise, the data shows.
“We need people to be adopting it at a faster clip,” said Arsenault of strong authentication methods. While there is some good news — global admins are a higher-risk group and should be prioritized — he thinks there is too strong a focus on legacy processes and emphasizes the importance of “progress over perfection.”
“I do sometimes worry that people think until they can get to 100%, they don’t move on each different segment,” he explained. “We can do more as an industry to continue to help people see — start with 2FA, start with the high-risk users relative to your business. There are different starting points for different businesses and different models. Pick the ones that are most important for your business.”
Another focus for security teams looking toward a hybrid future is network access control, he continues. Azure Firewall signals reveal 2 trillion flows blocked in the past year, including malicious flows detected by threat intelligence engines and unwanted traffic blocked by firewall rules. Web application firewalls (WAFs) in the past year have had more than 25 billion rules triggered on a weekly basis, with 4% to 5% of incoming traffic on average deemed malicious.
Arsenault says the shift to remote work also drove an increase in Remote Desktop Protocol (RDP) attacks compared with what Microsoft had seen in the past.
“We continue to see a fair amount of people going after legacy protocols; particularly for authentication we see that continue to happen,” he told Dark Reading.
Many of these attacks can be mitigated with the security basics: patching, keeping systems up-to-date, principle of least privilege, and MFA, he added.
“It feels like the pedestrian part of the jobs, but they largely either alleviate you from being susceptible to those or mitigate the impact, or blast radius, of those things when they happen,” he says. “It’s boring, but the reality is … still doing the basics are actually pretty effective relative to the attack patterns we see.”
Read More HERE
