Meet critical infrastructure security compliance requirements with Microsoft 365
Critical infrastructure operators face a hostile cyber threat environment and a complex compliance landscape. Every operator of an industrial control system also operates an IT network to service its productivity needs. A supervisory control and data acquisition (SCADA) system operator of a power grid or chemical plant needs email, databases, and business applications to support it, much like any enterprise.
IT environments, with their large attack surface, can be the entryway to attack critical infrastructure even where those IT systems are not critical infrastructure themselves. Security and compliance failures may include life safety, environmental, or national security consequences—a different risk management challenge from other enterprise IT systems.
Ransomware, thought more of as an IT problem as opposed to an industrial control system (ICS) one, has been used to attack critical infrastructure operators Norsk Hydro, Brazilian utilities Electrobras and Copel, as well as Reading Municipal Light Department and Lansing Board of Water and Light among other US utilities. Dragos and IBM X-Force identified 194 ransomware attacks against industrial entities between 2018 and 2020, including ICS-specific strains like EKANS.
The range of threats to our increasingly converged IT and ICS environments highlights the need for a combined approach to IT and ICS security.
Azure Defender for IoT is the cornerstone of security for on-premises, cloud, and hybrid ICS. In addition to the anti-malware features of Microsoft 365, the integration of Advanced Threat Protection (ATP) and Microsoft Compliance Manager to manage, visualize, and report on standards-based compliance are also foundational.
Complex compliance landscape
As the cyber threat landscape to ICS has grown more hostile and publicized, the compliance responsibilities of critical infrastructure operators have increased as well. In the US and Canada, Bulk Electric System (BES) participants need to comply with the North American Electric Reliability Corporation Critical Infrastructure Protection Standards (NERC CIP), as well as using NIST 800-53 as the basis for their organizational security policies and benchmarking to the National Institute of Standards and Technology (NIST) Cybersecurity Framework. They may also be architecting their ICS to IEC62443/ISA 99. Many forward-looking utilities are increasing their use of the cloud through infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) like Microsoft 365 with Zero Trust architecture.
While NERC CIP standards were written around on-premises systems, NERC has become more open to Registered Entities’ use of the cloud for Bulk Electric System Cyber System Information (BCSI). This includes NERC’s Order on Virtualization and Cloud Computing Services and their Technical Rationale for Reliability Standard CIP-011-3, where they discuss risk assessment of a cloud services provider. This risk assessment will include the ongoing standards-based assessment of the cloud service provider.
Comprehensive and efficient compliance
As an organization moves workloads to the cloud, they move responsibility for a portion of the security controls to the cloud service provider.

The organization can thus focus its resources on the remaining security controls and on vetting how the cloud service provider manages the security controls for which it is responsible.

When customers use Office 365, Microsoft helps them manage 79 percent of the 1,021 NIST 800-53 controls, so customers need only focus on implementing and maintaining the remaining 21 percent of the controls. By using the shared responsibility model, these customer resources are made available to further secure their systems. Customers that are using on-premises infrastructure to provide those functions need to implement and maintain all 1,021 controls.
Tools for comprehensive and efficient compliance
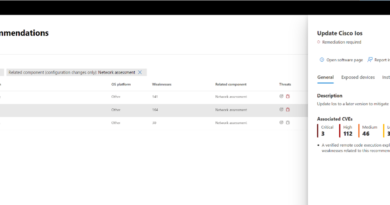
Microsoft Compliance Manager is a feature in Microsoft 365 compliance center. It uses signals from the customer’s Microsoft 365 tenant, Microsoft’s compliance program, and workflows completed by the customer to manage and report compliance against regulatory and industry-standard templates. These templates include NERC CIP, NIST Cybersecurity Framework (CSF), NIST 800-53, and the US Protecting and Securing Chemical Facilities from Terrorist Attacks Act (H.R. 4007), as well as more than 330 standards-based assessments globally. You can also create custom templates based on other standards or mapped to your own policies and control set.
With each Compliance Manager assessment template, you get simplified guidance on “what to do” to meet the regulatory requirements. In this regard, you get to understand what controls are Microsoft’s responsibility as your cloud service provider and what controls are your responsibility. Furthermore, for each of the controls that are your responsibility, we break down actions that you need to take to meet these control requirements. These actions can be procedural, documentation, or technical.
For technical actions, you get step-by-step guidance on how to use Microsoft security, compliance, identity, or management solutions to implement and test technical actions. With this detailed information, you can efficiently implement, test, and demonstrate your compliance against regulations as per your industry and region. This information also helps you to draw maximum benefits from your Microsoft 365 security and compliance solutions. Once you create assessments within Compliance Manager, we make it very easy for you to understand what solutions you can use to implement and test technical actions on Compliance Manager.

You can use the custom assessment feature to “extend” Compliance Manager assessment templates to track compliance against any non-Microsoft 365 assets as well. With this functionality, Compliance Manager helps you to track and manage compliance across all your assets.
There are different template sets available for the different license levels.
Microsoft updates the assessment templates when the standards change, relieving the customer of this responsibility. The changes are called out to the customer and the option to update the assessment is provided.
Compliance Manager tracks, reports, and provides visualizations for:
- Microsoft-managed controls: these are controls for Microsoft cloud services, for which Microsoft is responsible for implementing.
- Your controls: these are controls implemented and managed by your organization, sometimes referred to as “customer-managed controls.”
- Shared controls: these are controls that both your organization and Microsoft share responsibility for implementing.
The assessments are provided with visualizations that allow the user to drill down into the individual control status and view evidence. High impact improvement actions are suggested.


Compliance Manager covers both the Microsoft and customer-managed controls as part of the shared cloud security and compliance responsibility model. Automated workflows and evidence repositories are provided for customer-managed and shared controls.

You can assign a stakeholder and an automated message with instructions and upload link is provided on a schedule to remind them of the compliance activity required, report status, and upload evidence. This provides an efficient and defensible system to respond to auditors and benchmark compliance programs.
Many of the controls that enable compliance for critical infrastructure operators are common across the standards, so implementing a control once enables compliance across multiple standards.
Mapping controls across standards such as:
| NIST CSF Category | NIST CSF Subcategory | NIST 800-53 Rev. 4 Control | ISO 27001 Control | NERC CIP Control |
| Access Control (PR.AC): Access to assets and associated facilities is limited to authorized users, processes, or devices, and to authorized activities and transactions. | PR.AC-1: Identities and credentials are managed for authorized devices and users. | NIST SP 800-53 Rev. 4 AC-2, IA Family | ISO/IEC 27001:2013 A.9.2.1, A.9.2.2, A.9.2.4, A.9.3.1, A.9.4.2, A.9.4.3 | CIP-004-6 – Access Management Program, parts 4 and 5 |
This crosswalk across standards is part of the Compliance Manager and populated automatically across a customer’s assessments.

The level of effort to benchmark and report compliance with a new standards regime is dramatically reduced.
IT and ICS convergence is a continuing trend for critical infrastructure operators. Attack methodologies, surfaces, and threat actors are crossing over to put our most critical resources at risk. Compliance regimes must be efficiently met in an auditable way to protect the availability of our systems. Microsoft provides the range of tools described above to help you manage across the IT and ICS environments.
Learn more
Learn more about Microsoft Compliance Manager and how it helps simplify compliance and reduce risk.
To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE