McDonald’s email blunder broadcasts database creds to comedy competition winners
McDonald’s customers who won a prize draw competition got more than they hoped for after the burger chain emailed them login credentials for development and production databases used to power the campaign.
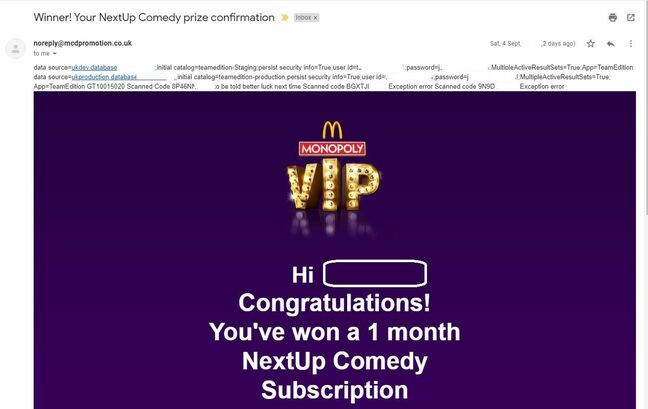
The first person to report the blunder to McDonald’s, startup founder Connor Greig, told The Register: “It’s a bit weird,” adding that code strings containing the credentials looked as if they had “been formatted into the email by accident.”
Like scores of Britons around the country, Greig, founder of web platform toolkit Creatorsphere, enjoys munching McDonald’s meaty produce. One of the chain’s most recent promotions was a Monopoly-themed giveaway; diners collected tokens with their burgers and typed promotional codes printed on them into McDonald’s website. Maccy D’s would then email them saying whether they’d won something or not.
Lucky winners could pick up a range of goods and services, including a six-month free subscription to NextUp Comedy, an upstart video streaming site. Greig was rather surprised, therefore, to find a string of familiar-looking code included in a McDonald’s email telling him about his free subscription.
Talking it through with El Reg on a video call, the one-time Hewlett-Packard engineer said he recognised the code above the email body text as a Windows Azure database connection string.
“This category is telling me what the database name is,” he explained as he highlighted the first line, “and this ‘persists security info true’ is where the issue is, this should be false. Where you mark that as true, it actually outputs the credentials. And right here, this user ID and password is the same user ID and password for production.”
Alarmed by the implications, Greig tried to get in contact with McDonald’s. He ran into immediate problems: the US megacorp’s UK tentacle doesn’t have a security.txt file on its website. Similar to robots.txt’s instructions for search engine crawlers, security.txt contains contact details so people finding security vulnerabilities can directly contact a company’s infosec department.
Next he tried phoning McDonald’s corporate HQ, only, he said, to get through to a recorded message telling him everyone was working from home. Next he emailed just under a dozen McDonald’s UK email addresses he was able to find. Nobody responded.
In frustration, he posted a video on TikTok begging McDonald’s to respond.
A human eventually replied to his emails – by accidentally copying Greig into an email that described his attempts to report the breach, under the email subject line “responsible security disclosure”, as “suspicious”, and copying in an EU-based MSP. After some to-ing and fro-ing, Greig was able to speak to an infosec person who understood what was going on and was able to get the problem fixed.
Troy Hunt of the Have I Been Pwned breach website also highlighted the blunder on Twitter after the emails were sent earlier this week, and highlighted it directly to El Reg.
McDonald’s insisted in a statement that the credentials it emailed to an unknown number of customers were only for a “staging” database. The burger chain failed to respond when we asked what the “ukproduction” username and password pair were for. It also asserted that no customer data was exposed, which seems a bold assertion to make when the database was clearly linked with an email marketing campaign.
“Those affected will be contacted to reassure them that this was a human error and that their information remains safe. We take data privacy very seriously and apologise for any undue concern this error has caused,” concluded the fast food outlet.
Greig noted that when viewed in the web app version of Microsoft Outlook, the email didn’t display the code string. He speculated that Outlook Web Access was parsing the code as part of the message headers, though Gmail (as pictured above) and other mail clients rendered it as part of the body text of the message.
It appears that someone at McDonald’s may have committed an accidental copy-and-paste error when setting up autoreplies for the marketing campaign; versions of the email sent to different people and seen by The Register show identical text and unique strings in the code snippet.
Whatever the root cause, it seems unlikely that their bosses are loving it. ®
READ MORE HERE