Malware in the age of IoT

Now that technology providers are bringing connectivity to a whole host of different items and appliances, the full force of the Internet of Things is beginning to be felt by businesses and consumers alike. From simple items like home routers to more complex, machine-to-machine systems, the IoT is a powerful, revolutionary tech concept.
As connected systems and devices continue to bring benefits to the enterprise and consumer sectors, everyone has taken notice, including hackers. Similar to every other intelligent solution that’s made an impact in the marketplace, connected IoT devices are attractive to hackers, as well as white hat users.
Malware that impacts IoT systems, however, operates a bit differently than traditional malware. What’s more, because IoT platforms and appliances don’t have the same computing power or security – and because these types of threats have seen a considerable uptick recently – it’s worth taking a closer look at the infections that can impact connectivity-enabled devices.
How far is the reach of the IoT?
Significant statistics have surrounded the IoT since its inception, demonstrating the potential impact that a system of connected items could have. Consider these up-to-date numbers from Statista:
- Researchers forecasted more than $284 billion in pending on IoT services in 2017, and predict that consumer spending will reach $1,494 billion by 2020.
- The overall IoT retail market will surpass a value of $5 billion over the next two years.
- The number of installed consumer IoT sensors and devices will reach 12.86 billion by 2020.
- The global market for RFID tags will reach a value of $24.5 billion by 2020.
- More than 37 million IoT-enabled road traffic management systems will be installed in the next two years.
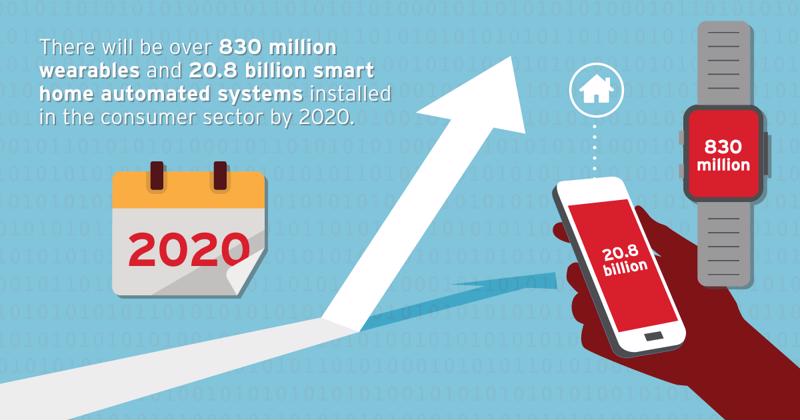
- There will be over 830 million wearables and 20.8 billion smart home automated systems installed in the consumer sector by 2020.
With such an expansive reach in the consumer, retail and civil sectors, it’s no wonder why malicious actors are beginning to take advantage of connected sensors and devices for black hat purposes.
 The IoT is set to grow steadily over the next few years.
The IoT is set to grow steadily over the next few years.How does IoT malware work?
IoT endpoints are considerably different than the traditional PCs and computing systems many users – and hackers – are used to. While these devices are equipped with wireless connectivity, some don’t have the type of classic user interface or computing power.
However, some of the factors that set IoT devices apart from other technological platforms are just the types of things that hackers seek out.
“The overall IoT retail market will surpass a value of $5 billion over the next two years.”
“While IoT devices have far less power than even the most basic PC, they come with the benefit – for the attackers at least – that they often lack proper cyber security controls and that users frequently install the device and more or less forget about it,” ZDNet contributor Danny Palmer wrote.
The use of default passwords and users not treating IoT endpoints in the same way that they would treat a traditional endpoint creates protection weaknesses that open the door for infection.
That being said, there are some similarities between recent malware strains infecting PCs and servers and the attacks launched on IoT systems. As Palmer explains, many IoT malware samples look to leverage devices for cryptocurrency mining, creating a botnet capable of generating a profit of untraceable, digital currency. Although some tech and security experts are unconvinced that hackers could create any kind of sizeable income from IoT cryptocurrency mining schemes, these instances should be considered a threat.
“While profit from infected IoT devices might be small – for not at least – it still represents a worry for users because ultimately the device is infected with malware,” Palmer noted. “While cryptojacking arguably isn’t as damaging as the likes of ransomware or trojans, the devices has still been compromised.”
IoT malware: Mirai variant targets IoT devices
One instance of an infection that specifically targets IoT endpoints is a variant of the Mirai malware sample, named OMG and identified as ELF_MIRAI.AUSX by Trend Micro researchers. This variant leverages the same distributed denial-of-service style attack capabilities as the original Mirai sample. The OMG variant also comes with certain code additions and omissions in an effort to infect IoT endpoints, including home routers, in particular.
“The main point of a Mirai attack is to allow cybercriminals authors to use privately-owned routers in their malicious activities without the knowledge of the owner,” Trend Micro researchers explained. “Such attacks can have dire consequence for its victims, which could also include enterprises. Businesses could deal with business disruptions, monetary loss, and even damaged brand reputations.”
Reaper: Building on the capabilities of Mirai
The OMG Mirai variant was one of the first notable IoT-targeting infections, but it surely wasn’t the last. In late 2017, WIRED contributor Andy Greenberg reported on the Reaper IoT Botnet, which at the time of that writing, had already infected a total of one million networks.
 Default passwords and weak security are opening the door for malicious IoT-targeted activity.
Default passwords and weak security are opening the door for malicious IoT-targeted activity.While Mirai and the OMG variant exploited weak security credentials or un-updated default passwords, the Reaper botnet – also known IoT Troop – uses a more focused approach. This threat uses more active hacking techniques to pinpoint and infect IoT endpoints, establish a far-reaching botnet with considerable computing power.
“It’s the difference between checking for open doors and actively picking locks,” Greenberg explained, comparing Mirai to Reaper. “Instead of merely guessing the passwords of the devices it infects, [Reaper] uses known security flaws in the code of these insecure machines hacking in with an array of compromise tools and then spreading itself further.”
Safeguarding IoT endpoints: Enterprise best practices
The Reaper botnet threat shows that malicious actors are becoming increasingly savvy with their IoT-targeted infections, and chances are good that attacks on connected devices will only become more complex. As enterprises continue to take advantage of all that the IoT can offer, it’s also important to ensure that these sensors and endpoints are properly protected:
- Select reliable IoT products: It’s important to deploy only routers and IoT appliances that include robust security protections. For instance, Trend Micro researchers recommend avoiding routers that include internet service packages, and to never use used routers, as these can have incorrect and insecure configurations.
- Use strong authentication credentials: Most IoT devices come with pre-installed, default passwords. These represent an open door to hackers, making a breach and an infection a simple process for malicious actors. For this reason, it’s imperative to change default passwords to something stronger and not easily guessed upon device deployment.
- Ensure devices are updated: Businesses and consumers should also make sure that the firmware supporting router operations is up-to-date, including the OS, drivers, management programs and configurations.
To find out more about the latest news involving the IoT, connect with the security experts at Trend Micro today.
Read More HERE



