Malicious App Infects 60,000 Android Devices – But Still Saves Their Batteries
A battery-saving app that also allows attackers to snatch text messages and read sensitive log data has been downloaded by more than 60,000 Android devices so far.
But what’s unique about the attack, according to the researchers at RiskIQ who discovered it, is that it holds true to its advertising: It actually does monitor devices’ battery status, even killing unwanted background processes.
“Although the app these scam pages send users to does its advertised function, it also has a nasty secret—it infects victims’ devices and comes with a side of information-stealing and ad-clicking,” Yonathan Klijnsma, threat researcher at RiskIQ, said in a post on Thursday.
Klijnsma told Threatpost that although a complaint has been filed for take-down, the app can still be found on Google Play. Google did not respond to a request for comment from Threatpost.
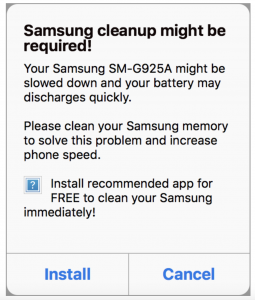
The attack starts off with a false warning message that appears on Android users’ devices while they browse the web.
Klijnsma said that the pop-up’s text is customized around the victim’s device by parsing the user-agent server-side and embedding the processed brand and model information in the script behind the pop-up (in this example given below, for instance, the pop-up identifies the user device as a Samsung SM-G925A).
 While most scams lead victims to other web pages, researchers were surprised to find that this particular message led them to Google Play, where they were then served a malicious app.
While most scams lead victims to other web pages, researchers were surprised to find that this particular message led them to Google Play, where they were then served a malicious app.
The pop-up heavily pushes victims to do its bidding; even if they click “cancel” instead of “install,” it will take them to the Google Play Store app; and, if they hit the back button on the page, another pop-up warning message appears telling them that their desktop will remain slow.
Once the victim goes to the app store and downloads the battery-saving app, it requests access to an array of privacy permissions, such as reading sensitive log data, receiving text messages, receiving data from the internet, pairing with Bluetooth devices and full network access.
The mobile app also comes with a small ad-clicking backdoor that steals information from the phone like International Mobile Equipment Identity (IMEI), phone numbers and location.
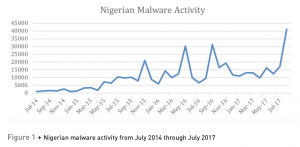
Researchers were able to analyze command-and-control traffic, and observed that the C2 server assigned incremental ID numbers to bots; “Based on those ID numbers, we can say with high certainty that the bot has had at least 60,000 android devices under its control,” they said.
Interestingly, the app does actually perform the legitimate functions mentioned, including reducing battery strain to lengthen the battery life, monitoring the battery status and killing off processes that use battery resources when the battery is low.
“[Sometimes], popular apps are bought out and then modified,” Klijnsma explained to Threatpost. “I feel like that might have been the case here: [Criminals] buy the source code for an app or get a freelancer to build it, and [then] add your own malicious code.”
Google Play lists details about the developers, so Klijnsma was able to track down clues about the app developer, using their email address listed. The email used to have another app on the Google Play store, which was has been taken down, he said.
There also may be more than one attacker at play.
“It appears that most of the effort here went into making the mobile app, while the page that redirects to it seems to be relatively low-effort,” said Klijnsma. “The lack of attention to detail on the redirector pages could signify that the group is less concerned with them than they are with the app itself, or that one group is creating the redirector pages while another is responsible for the mobile part of the campaign.”
READ MORE HERE