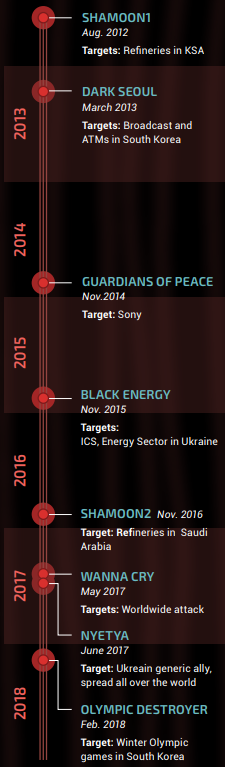
Main Considerations for Securing Enterprise 5G Networks


Securing the integration of 5G with other technologies
A myriad of technologies can work alongside enterprise 5G. Network slicing, open API, DevOps, automation, cloud native, core virtualization, microservices, and machine learning are just a few examples. But the very connections with these and other technologies can also inadvertently expose the network to more threats.
With the goal of securely integrating these technologies with 5G, enterprises should establish an onboarding process that identifies security demands as a response to their inherent characteristics, such as their service provider, vendor, configurations, security controls, and environment.
For example, through network slicing, enterprises can perform microsegmentation on the network level. It provides hybrid (private/public 5G) concepts of network isolation, or network separation by use cases such as healthcare, internet of things (IoT), and connected cars. At this point, it is necessary to consider the security measurements and controls, such as IT/OT clean pipes and application-based security, that are specific to a particular use case.
Security considerations for enterprise 5G networks
Of course, besides the technologies linked to 5G, it is also important to secure the elements within the network itself. Here are some of these components and their corresponding pressing security considerations.
Core services security
It can be said that the foundation of 5G core service security is virtualization infrastructure and technology innovation security. In addition to the underlying security mechanisms, enterprises must also look at the importance of day-to-day operations from a security perspective, as core services govern 5G control and management elements.
Security considerations for these include zoning for communication controls, integration with security operations centers (SOCs), and realizing the proof of concept of the security functions.
MEC security
Multiaccess edge computing (MEC) involves moving services and functions to the edge of the network. Virtual machines (VMs) help keep each MEC service operational. For these VM setups, baseline security is nonnegotiable. Further considerations for this include the implementation of strong security controls for the coordination and separation of each service, which results from a deep understanding of each business use case.
For example, the healthcare industry needs private 5G because hospital use cases require deep medical analytics, and it is necessary to automatically optimize the data scanned by medical machines and relay it to medical professionals’ computers. Here, personal health information, being the usual target of cybercriminal activity, is most in need of protection. This situation requires strict security implementation that is different from mere segmentation provided for other common services.
RAN security
A radio access network (RAN) provides radio connections that help link endpoints and devices to networks (such as 5G ones). The openness of open radio access network (O-RAN) architecture, which aims to establish interoperability standards for RAN, speeds up the transformation of the 5G radio access network industry toward open, intelligent, virtualized, and fully interoperable RANs.
But leveraging O-RAN solutions to construct RANs also brings cyber risks to enterprises. The decoupled radio unit (RU), distributed unit (DU), and centralized unit (CU) could be developed through open-source platforms, which have vulnerabilities that could be exploited by cybercriminals. Therefore, vulnerability management is vital in the use of open-source platforms and in overall RAN security.
Endpoint security
Endpoints include drones, cranes, and various sensors in factories. Related security considerations include preventing and fighting forms of abuse of endpoints. It is also necessary to consider countermeasures against the exploitation of radio-connected endpoint devices that use new identifiers.
An example of such abuse is SIM swapping, where an attacker installs the endpoint’s SIM card on their own device and uses it to infiltrate the enterprise network, locate and identify vulnerabilities, or attack other devices.
Securing 5G connections in actual applications
Implementing enterprise 5G security requires understanding not only its technical characteristics but also how the networks are used in enterprise systems. Venues where enterprise 5G is commonly used include smart factories and smart cars.
Cyber risks in smart factories
5G connections provide various benefits in smart factories. For example, the wireless connection afforded by 5G for production equipment can significantly reduce wiring work. This makes it possible to quickly and easily lay and reorganize lines, which improves equipment utilization.
In such an environment, it is necessary to protect intellectual property and other sensitive information as well as the operation of production equipment. However, the precarious connections between IT and OT make systems vulnerable to threats. These threats can have serious consequences, such as:
- Lateral infection from information systems that can seep from IT to OT.
- Malware intrusion from PCs or removable drives in supervisory control and data acquisition (SCADA) systems.
- Lateral infection from other devices that could affect various components of the smart factory system.
- Unauthorized access and vulnerability attacks in the cloud.
Cyber risks in connected cars
For connected cars, 5G networks bring a host of benefits as they foster faster connections between a vehicle and other vehicles, devices, and networks. But they also introduce certain security considerations:
- Direct attacks on endpoints through short-range access or malicious networks
- Attacks on legitimate networks
- Attacks from mobile devices
- Attacks from back-end components, such as over-the-air (OTA) servers, telematics servers, and app stores
- Attacks from third-party vendor systems, such as intelligent transport systems (ITSs), vehicle-to-everything (V2X) systems, map servers, and web servers
Recommendations for securing enterprise 5G networks
At first glance, the security considerations for enterprise 5G security might not look like a lot, or might not even be apparent at all. But upon closer examination, there are actually a lot of elements to take into account.
When 5G is introduced to an enterprise, even when it is set up in an air-gapped environment, the adoption of this technology brings new challenges. An enterprise’s infosec team must perform a holistic review to check whether existing IT/OT security solutions can cover the new risks. While adopting powerful technologies such as 5G, staying stuck in the old mindset that calls for vigilance only against known threats is a critical mistake.
Indeed, with great power comes great responsibility. In the case of securing enterprise 5G, this responsibility is shared: The enterprises themselves, telecom service providers, and cybersecurity experts must discuss the networks’ security to ensure comprehensive protection for all layers and components of their 5G systems.
Security solutions for enterprise 5G are also vital. One example is Trend Micro™ Mobile Network Security (TMMNS), which provides comprehensive visibility, exhaustive detection, and quick response to ensure end-to-end security for enterprise 5G and its applications.
Read More HERE