Learn how Microsoft strengthens IoT and OT security with Zero Trust
As cyber threats grow more sophisticated and relentless, the need for Cybersecurity Awareness Month becomes more urgent every year. As part of our year-round commitment to security for all, Microsoft continues to track numerous incidents targeting both digital and physical operations for many organizations. Beyond the usual espionage and data-theft attacks aimed at IT systems, threat actors have increasingly turned their attention toward IoT devices and operational technology (OT) equipment—everything from oil pipelines1 to medical devices.2 Malicious actors have also had success in targeting supply chains, as seen in the insidious Solorigate3 and Kaseya4 attacks.
Earlier this month, we published the 2021 Microsoft Digital Defense Report to help organizations better understand this evolving threat landscape, as well as provide guidance on securing your supply chain and IoT and OT assets. In the spirit of security for all, some highlights of these chapters are presented here for easy reference.
Securing supply chains
The practice of adopting multiple tools to monitor different tiers of suppliers increases complexity, which in turn increases the odds that a cyberattack can produce a significant return for your adversary. Siloes can create additional problems—different teams have different priorities, which may lead to different risk priorities and practices. This inconsistency can create a duplication of efforts and gaps in risk analysis. Suppliers’ personnel also are a top concern. Organizations want to know who has access to their data; so they can protect themselves from human liability, shadow IT, and other insider threats.
For supplier risk management, an always-on, automated, integrated approach is needed, but current processes aren’t well-suited to the task. To secure your supply chain, it’s important to have a repeatable process that will scale as your organization innovates. At Microsoft, we group our investments into nine secure supply chain (SSC) workstreams to methodically evaluate and mitigate risk in each area:

Figure 1: Nine areas of investment for a secure end-to-end supply chain.
For supply chain risk management, having integrated solutions and greater visibility into who ultimately has access to an organization’s data are top priorities. While there are many places to begin a Zero Trust journey, instituting multifactor authentication (MFA) should be your first step.
From the White House
On May 12, 2021, the White House issued Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity outlining steps for federal agencies and their technology providers to enhance supply chain security. For software providers, the EO calls for requirements to enhance resistance to attack, including secure software development practices, software verification and vulnerability checks, a software bill of materials (SBOM), a vulnerability disclosure program, and other secure practices.
For federal agency users of software with privileged access, EO 14028 calls for implementing security measures published by the National Institute of Standards and Technology (NIST). Microsoft has long been invested in developing best practices for secure software development, and we’ve contributed to efforts to define industry-wide practices and consensus standards, including through SAFECode, ISO/IEC, and NIST’s National Cybersecurity Center of Excellence (NCCoE) on the Implementing a Zero Trust Architecture project.
IoT and OT security
With the prevalence of cloud connectivity, IoT and OT have become another part of your network. And because IoT and OT devices are typically deployed in diverse environments—from inside factories or office buildings to remote worksites or critical infrastructure—they’re exposed in ways that can make them easy targets. When you add in privacy concerns and regulatory compliance, it’s clear that a holistic approach is needed for enabling seamless security and governance across all your devices.
Securing IoT solutions with a Zero Trust security model is built upon five requirements:
- Implement strong identity to authenticate devices: Register devices, issue renewable credentials, employ passwordless authentication, and use a hardware root of trust to ensure identity before making decisions.
- Maintain least privilege access to mitigate blast radius: Implement device and workload access controls to limit any potential damage from identities that may have been compromised, or those running unapproved workloads.
- Monitor device health to gate access or flag for remediation: Check security configurations, assess for vulnerabilities and insecure passwords, and monitor for active threats and anomalous behavioral alerts to build risk profiles.
- Deploy continual updates to keep devices healthy: Utilize a centralized configuration and compliance management solution, as well as a robust update mechanism, to ensure devices are up to date and healthy.
- Maintain security monitoring and response: Employ proactive monitoring to rapidly identify unauthorized or compromised devices.

Figure 2: How an attacker can get into an enterprise through IoT.
“Attackers will choose the ‘soft targets’ as a point of ingress. Spear phishing or similar attacks allow access to IT systems that can then provide a pathway for attackers to reach OT systems, and the reverse is also possible. In one example, attackers used an aquarium system to access a casino’s high-roller databases, demonstrating that any device with connectivity can present a motivated attacker with an opening.”—2021 Microsoft Digital Defense Report
Default passwords cause problems
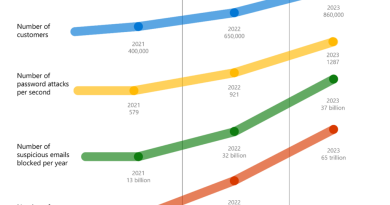
Microsoft’s sensor network provides us with raw data on more than 280,000 attacks, including password data. Unsurprisingly, we saw that 96 percent of attacks used a password with fewer than 10 characters. Within these password attempts, only 2 percent included a special character and 72 percent didn’t even contain a number. The word “admin” was found more than 20 million times in IoT passwords over a 45 day period.

Figure 3: Prevalence of common passwords in IoT and OT settings.
Maintain your IoT just like IT
It’s essential for organizations to assess the security of their IoT and OT systems with the same rigor applied to IT systems. While PCs are routinely required to have updated certificates, IoT devices are often deployed with factory-default passwords. Attackers are also focusing on how IoT and OT interact, which brings real dangers. Industrial control systems (ICS) are often retrofitted with remote capabilities—meaning, virtual attacks can cause physical harm.
Microsoft supported a research study conducted by the Global Cyber Alliance (GCA) to demonstrate the effectiveness of commonly recommended controls in preventing attacks. GCA’s analysis of real attack data shows that default passwords factory-set by device manufacturers, or weak passwords set by users, represent the most exploited security vulnerability for IoT devices. Their findings can be boiled down to four simple takeaways for IoT and OT security:
- No default passwords.
- Implement a vulnerability disclosure policy.
- Keep software updated.
- Continuously monitor IoT communication for unauthorized communications and attacks.
Learn more
Learn how Microsoft Defender for IoT can secure your IoT and OT devices.
To find out more about protecting your organization against supply chain and IoT/OT attacks, including the seven properties of highly secured devices, download the 2021 Microsoft Digital Defense Report. Also, see our past blog posts providing information for each themed week of Cybersecurity Awareness Month 2021:
Be sure to visit our Cybersecurity Awareness Month page for more resources and information on protecting your organization year-round. Do your part. #BeCyberSmart
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
1Hackers Breached Colonial Pipeline Using Compromised Password, William Turton, Kartikay Mehrotra, Bloomberg. 4 June 2021.
2Microsoft Warns of 25 Critical Vulnerabilities in IoT, Industrial Devices, Elizabeth Montalbano, Threatpost. 30 April 2021.
3Deep dive into the Solorigate second-stage activation: From SUNBURST to TEARDROP and Raindrop, Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center (MSTIC), Microsoft Cyber Defense Operations Center (CDOC), Microsoft Security. 20 January 2021.
4Kaseya ransomware attack sets off race to hack service providers -researchers, Joseph Menn, Reuters. 3 August 2021.
READ MORE HERE