IT Management Platform Kaseya Hit With Sodinokibi/REvil Ransomware Attack Trend Micro


Update as of July 23, 1:48 a.m. EDT: Kaseya, with the help of a third party, has obtained a decryptor tool for the victims of the ransomware attack.
Update as of July 13, 1:34 a.m. EDT: Kaseya released its patch on July 11, 4:30 p.m. EDT. As of July 12, 7:30 a.m. EDT, its SaaS is now 100% online.
Update as of July 6, 10:37 p.m. EDT: Trend Micro released a free assessment service that checks environments for the presence of Kaseya vulnerabilities that are related to this attack.
Update as of July 6, 12:02 a.m. EDT: Kaseya has confirmed that a patch will be available after its SaaS servers go online.
Update as of July 5, 1:48 a.m. EDT: The Dutch Security Hotline (DIVD CSIRT) has identified CVE-2021-30116 as one of the zero-day vulnerabilities used in the ransomware attacks. The Kaseya vulnerability was found as part of research conducted into system administration tools; Kaseya and DIVD-CSIRT were working on a coordinated disclosure release before this incident. In addition, reports of REvil pushing for a deal for a universal decryptor have also surfaced.
Kaseya, a company that provides IT management software to managed service providers (MSPs) and IT companies, has been hit with a REvil (aka Sodinokibi) ransomware attack at the dawn of the Fourth of July weekend, as reported in the company’s own announcement.
The company describes it as a “sophisticated cyberattack” that was geared toward its on-premises VSA product. The company advised all its customers to shut down their on-premises VSA servers until further notice.
Kaseya has decided to also immediately shut down its software-as-a-service (SaaS) servers as a conservative security measure while investigations are ongoing.
At It Again: REvil Ransomware Actors
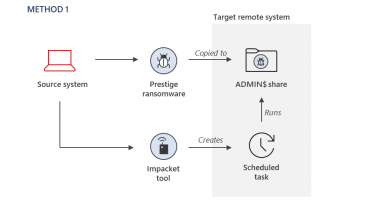
Though technical information about the attack has yet to be released by Kaseya as of this writing, the Cybersecurity and Infrastructure Security Agency (CISA) shared that Kaseya’s VSA software was used to push a malicious script.
The VSA software, which is typically used to distribute software updates to customers, was weaponized to push a malicious PowerShell script, which then loaded the REvil ransomware payload onto customer systems. It’s also important to note that non-Kaseya customers could also be affected via their service providers.
The Sodinokibi/REvil ransomware (detected as Ransom.Win32.SODINOKIBI.YABGC) that affected Kaseya VSA disables certain services and terminates processes related to legitimate software such as browsers and productivity applications. Specifically, it terminates the following processes:
- agntsvc
- dbeng50
- dbsnmp
- encsvc
- excel
- firefox
- infopath
- isqlplussvc
- msaccess
- mspub
- mydesktopqos
- mydesktopservice
- ocautoupds
- ocomm
- ocssd
- onenote
- oracle
- outlook
- powerpnt
- sqbcoreservice
- sql
- steam
- synctime
- tbirdconfig
- thebat
- thunderbird
- visio
- winword
- wordpad
- xfssvccon
Sodinokibi terminates itself if it detects the operating system language to be any of the following:
- Arabic – Syria
- Armenian Eastern
- Azeri Cyrillic
- Azeri Latin
- Belarusian
- Georgian
- Kazakh
- Kyrgyz Cyrillic
- Romanian – Moldova
- Russian
- Russian – Moldova
- Syriac
- Tajik
- Tatar
- Turkmen
- Ukranian
- Uzbek Cyrillic
- Uzbek Latin
Read More HERE