IoT Botnet Infects 100,000 Routers To Send Spam

A new botnet made up of roughly 100,000 home routers has silently grown over the past two months. According to current evidence, the botnet’s operators appear to use the infected routers to connect to webmail services and are most likely sending out massive email spam campaigns.
First spotted this September by the Netlab team at Qihoo 360, the botnet has been exploiting a well-known five-year-old vulnerability to spread.
The vulnerability was discovered in 2013 by security researchers from DefenseCode and resides in the Broadcom UPnP SDK, a piece of software that was embedded in thousands of router models from multiple vendors.
The vulnerability allows an attacker to execute malicious code on a remote vulnerable router without needing to authenticate, and it’s the worse kind of vulnerability that exists in the world of Internet-connected devices.
Several botnets have abused this flaw in the past, but Netlab has nicknamed this latest botnet BCMUPnP_Hunter. The name comes from the botnet’s constant scans for routers with exposed UPnP interfaces (port 5431).
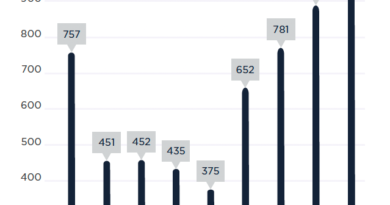
Over the last two months, the Chinese researchers say they’ve seen BCMUPnP_Hunter scans originating from over 3.37 million IPs, but the number of daily active devices has been usually at around 100,000. Victims are spread out pretty evenly across the globe, but the biggest concentration of infected routers are in India, China, and the US.

Image: Qihoo 360 Netlab
But setting aside its considerable size, this new botnet is also different from the vast majority of IoT botnets that are currently active today. Most of today’s botnets rely on source code that has been leaked online, but in regards to this, BCMUPnP_Hunter is a totally new beast.
“We did not find similar code using search engines,” said Hui Wang, one of the two Netlab researchers who analyzed the botnet’s source.
“It seems that the author has profound skills and is not a typical script kid,” Hui added. In a technical report published today, the researcher also goes on to highlight the botnet’s complex multi-stage infection mechanism, which is something unique compared to existing threats.
According to Hui, once BCMUPnP_Hunter finishes this multi-stage infection process and gains a foothold on a vulnerable device, it uses it to hunt for other vulnerable routers. But he says the botnet also hides a secondary function. This secondary function allows the botnet to use infected the routers as proxy nodes and relay connections from the botnet’s operators to remote IPs.
At the time of writing, Hui said that all the IPs Netlab has observed BCMUPnP_Hunter connecting to are IP addresses owned by webmail services such as Yahoo, Outlook, and Hotmail.

Image: Qihoo 360 Netlab
Because all connections were made via TCP port 25 (assigned to the Simple Mail Transfer Protocol [SMTP]), researchers are confident the botnet herders are secretly sending spam waves from behind the botnet’s cloak of ever-shifting proxies (infected routers).
For what it’s worth, BCMUPnP_Hunter is not the first IoT botnet to operate as a proxy network (botnets based on the UPnProxy technique are known to do the same) nor as a spam-sending service (see ProxyM botnet).
Related stories:
READ MORE HERE