How US Military Hackers Prepared To Hack The Islamic State
Image: AHMAD AL-RUBAYE/AFP/Getty Images.
In 2016, US Cyber Command (CYBERCOM), a part of the military tasked with conducting offensive cyber operations, hacked internet infrastructure used by the so-called Islamic State. Now, redacted versions of formerly Top Secret and other classified documents obtained by Motherboard lay out the contours of how CYBERCOM planned that operation, taking into account political fallout, the chance of the attack being attributed back to the US government, and other potential consequences.
The documents provide a snapshot of what goes into an official US military hacking operation, the bureaucratic machinations and analysis that comes with it, and how CYBERCOM tries to account for a number of different situations springing from its own hacking campaigns.
“In my time at US Cyber Command, I never saw an [operation] be planned that didn’t go through an intense amount of rigor with the entire government and sometimes even foreign partners weighing in with their equities,” Ryan Duff, a former cyber operations tactician at CYBERCOM, and now director of cyber solutions at Point3, told Motherboard in an online chat.

Caption: One of the slides Motherboard obtained, mentioning a probability of attribution assessment. Image: Motherboard.
The Washington Post first revealed Operation Glowing Symphony in May last year. The campaign was focused on disrupting the Islamic State’s ability to distribute its propaganda. CYBERCOM hackers obtained the passwords to multiple Islamic State administrator accounts, deleted battlefield footage, and changed the passwords, locking the administrators out, the report says.
“Develop,” “Distribute,” “Disseminate,” and “Defend,” one CYBERCOM slide Motherboard obtained via the Freedom of Information Act reads, referring to how CYBERCOM views the Islamic State’s strategy. One memo says the group employs people with varying levels of expertise to setup both public and private internet infrastructure, and that these people are responsible for maintaining the Islamic State’s websites and mobile phone applications.
But it’s the documents detailing the run-up to the operation that stand out. One slide suggests CYBERCOM laid out specific tactics and techniques it intended to use as part of the hacking campaign. Another indicated CYBERCOM assessed that the Islamic State likely wouldn’t strike back against the Department of Defense’s Information Network (DODIN), as the group “has no demonstrated capability.” One slide also touches on a legal review of the operation, saying that “there is no legal objection to conducting the activities proposed.”
Caption: One of the slides Motherboard obtained, showing the outlines of an assessment into potential political fallout from the CYBERCOM hacking operation. Image: Motherboard.
Another slide, a so-called “Intelligence Gain/Loss” assessment, includes sections on the probability that the military hackers will be detected. Another predicts the likelihood of the cyberattack being attributed back to CYBERCOM, including on “perceived” and “technical” levels. Although the results of both assessments are redacted, “technical” attribution refers to the probability that the adversary could use reverse engineering or other technical analysis to link the attack back to the US government. Typically, perceived attribution is medium to high risk, depending on the sophistication of the attack, and technical attribution is low, unless the hackers want to deliberately make it easier for the enemy to successfully connect an operation to the US government. In cases like those, perhaps the US wanted to send a message to an adversary, or purposefully demonstrate their capability.
“This seems to show that CYBERCOM systematically and regularly assesses the risks of getting caught red-handed,” Thomas Rid, professor of strategic studies at Johns Hopkins University, told Motherboard in an online chat. “A sober, no-nonsense risk assessment is exactly what you would expect from professional and disciplined operators.”
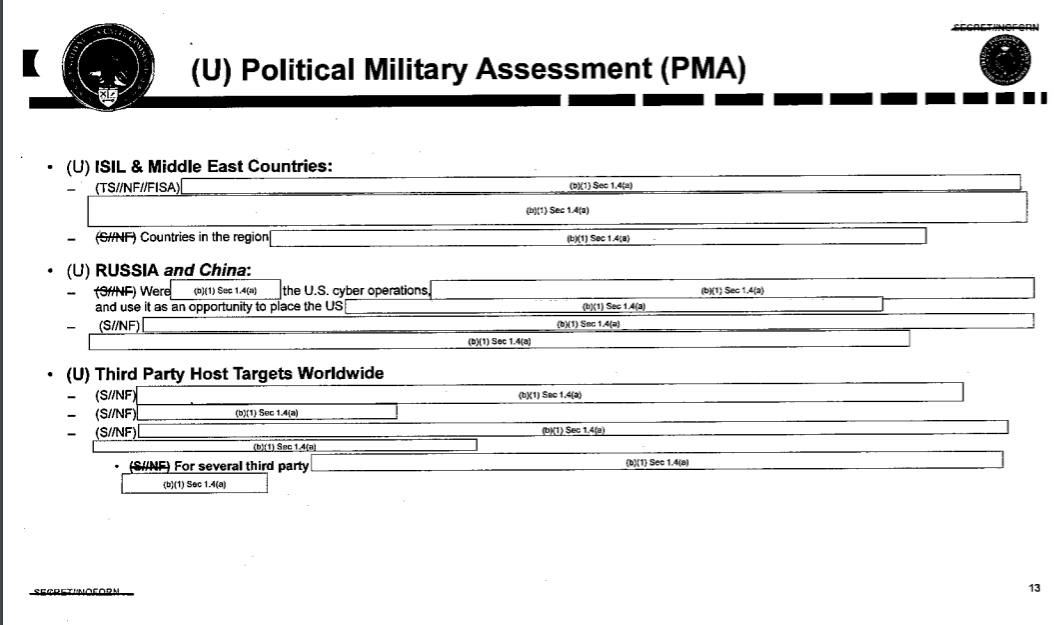
A subsequent slide is a “Political Military Assessment,” which summarises the potential geo-political fallout of such an operation. Although the substance of each assessment is redacted, the document specifically points to the Islamic State and Middle East countries in one section, followed by Russia and China in another, and “Third Party Host Targets Worldwide” in a third, likely referring to web hosts that the Islamic State was using.
Got a tip? You can contact this reporter securely on Signal on +44 20 8133 5190, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Indeed, as The Washington Post noted in its original report, the operation involved hacking into infrastructure hosted within the borders of allied countries. Officials at the CIA, State Department and the FBI raised concerns about carrying out such a campaign without informing those allies; the US ultimately did inform a number of them, the report adds.
One memo obtained by Motherboard says CYBERCOM requested assistance from the UK’s signals intelligence agency GCHQ, as well as the FBI. (In April during a speech, the director of GCHQ Jeremy Fleming said that the agency had conducted a cyber campaign against the Islamic State, and added that “These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield.”)
The full cache of documents obtained by Motherboard can be found here.
Update: This piece has been updated to clarify comments saying that the slides are in reference to planning an operation, not a mission.
READ MORE HERE
