Hacktivism Activity And Chatter Has Markedly Dropped Since 2016

After peaking in 2016, the number of active hacktivist groups have since dipped precipitously, as has overall online chatter regarding hacktivism, according to a new report from researchers at Recorded Future. Furthermore, the researchers found a marked reduction in the frequency of large-scale international hacktivism campaigns.
Members of the company’s Insikt Group team theorize that this overall downward trend can be attributed in part to improved defensive postures thwarting hacktivist operations.
“The number of large enterprises susceptible to SQL injection attacks or DDoS floods have decreased, likely due to more mature website structures and the use of DDoS protection services…” the report states. “Although some hacktivist actors are highly skilled, more often than not many members of a hacktivist organization are not skilled and are forced to rely upon simple and outdated tools and techniques that are easily defeated by competent network defenders.”
Moreover, several prominent prosecutions have served as effective deterrents for individuals who were not deeply committed to their causes, the report continues. Consequently, hacktivist groups have shrunk in size or fractured into smaller groups. “As the number of casual participants declines, the percentage of highly motivated actors remaining in the groups increases and may result in more aggressive, but less broadly supported, activity,” Recorded Future concludes in its report.
Insikt Group also noted a notable decline in references to hacktivism among underground forums, technical blogs, social media platforms, government bodies, mainstream news outlets, and analysts, among other possible sources. “Recorded Future data shows that mentions of hacktivism-related cyberattacks have declined steeply across multiple media sources, including social media, over the last four years,” the report states. “Insikt Group assesses with medium confidence that this is in part due to a decline in amplifying discussions (e.g., news articles and social media shares) around hacktivism-related cyberattacks.”
Despite changes in hacktivism frequency levels, the types of attacks hacktivists engage in have generally remained the same over the last decade, including denial of service, defacements, doxxings and account takeovers, the report states. Of these attack categories, defacements have defied recent trends and actually increased over the last three years, perhaps aided by the advent of automated web defacement tools, the report states. However, the researchers are unclear as to whether these more recent attacks are primarily the work of hacktivists or cybercriminals.
Recorded Future’s report somewhat echoed findings that had been previously published in a May 2019 threat intelligence report by IBM Security’s X-Force team, which determined that publicly disclosed hacktivist attacks decreased by nearly 95 percent since 2015.
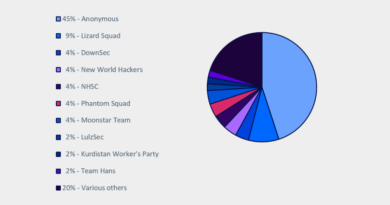
“… Analysis shows that few hacktivist groups aside from Anonymous have notably dominated the attack landscape over the past four years, with most groups carrying out only one or two attacks and then disappearing for a time,” the IBM report states.
Even Anonymous actors conducted significantly fewer attacks in recent years, that report continues, although Recorded Future apparently disagrees with this assessment. Insikt Group found that Anonymous-affiliated actors has actually held steady in the last few years, while reaching peak online mentions in 2017. (In some years, Anonymous was referenced online over a hundred times more than other hacktivist groups, the new report notes.)
“We assess that hacktivism as a technique will persist and will be conducted by more motivated and often more capable actors,” Recorded Future concludes in its report. “Nonstate-sponsored volunteer hacktivist groups in the future may also consist of more dedicated and skilled members. With an increase in operations from nation-states involving coordinated campaigns with hacktivists of like mind or government operators acting as hacktivists, the use of advanced techniques and more persistent activity may be expected from purported hacktivists.”
Late last week, Recorded Future also released another report looking at efforts by the Chinese state media to use English-language social media to influence perceptions of the ongoing protests in Hong Kong, where citizens are rallying against oppression by the Chinese government.
The Insikt Group team found that state-run social media accounts mostly ignored the tumult until June 9, at which point they began to post content that both condemned the protests and expressed support for the current government of Hong Kong.
Volume of posts increased at various critical points, including when protesters made their way into the chambers of the Hong Kong Legislative Council on July 1 and when protesters started demonstrating at Hong Kong’s international airport on Aug. 9.
“State-run influence accounts referenced the People’s Liberation Army (PLA) in posts about Hong Kong more than any other entity, person, or organization aside from [Hong Kong] Chief Executive Carrie Lam,” Recorded Future states in a blog post summarizing the main report. “We believe this was probably an attempt to seed the social media environment with reasons to justify a possible future mainland intervention in Hong Kong, but it is not an indicator or warning for PLA action.”
READ MORE HERE