Hackers Turned Virginia Government Sites Into eBook Scam
Hackers hijacked and took over control of two subdomains on the official website of the Virginia state government. For some reason, they then turned the two sites into some sort of eBook scam.
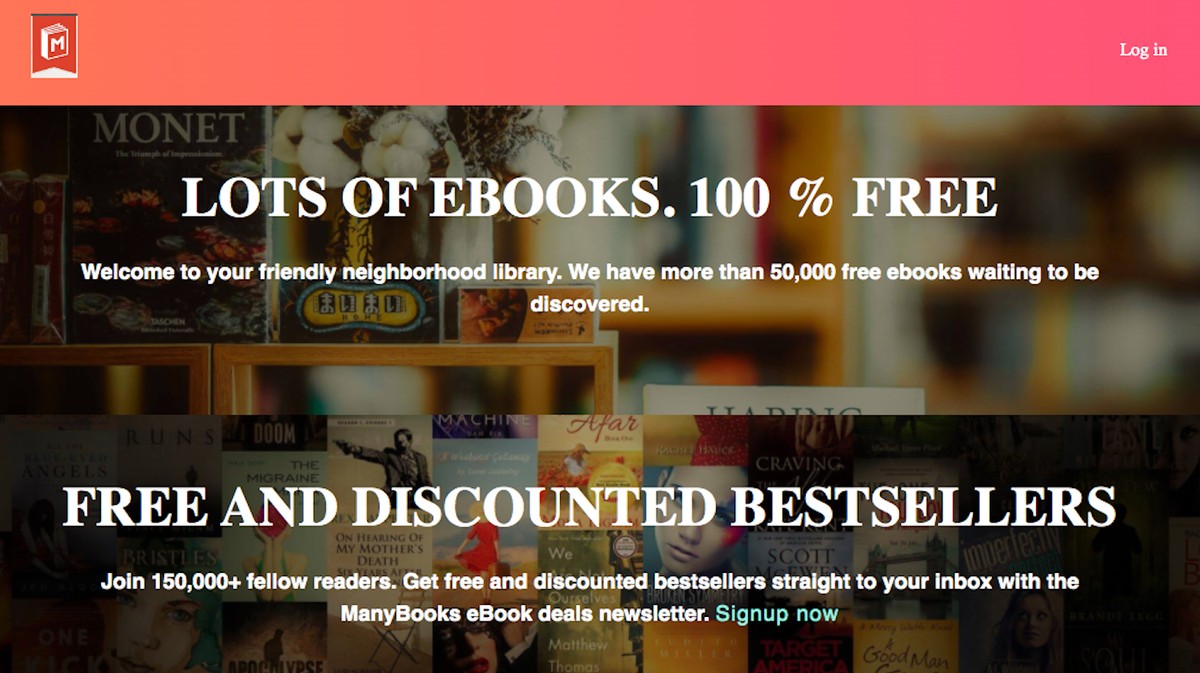
The two subdomains, vwn.virginia.gov and crc.virginia.gov had the same content, a list of eBook titles and genres, which redirect to a messy page filled with links to download PDFs. After we contacted the state of Virginia for this article, it took down the pages entirely. It’s unclear what hackers are doing with these domains, but it’s possible that these pages just have placeholder content while they’re used to host malicious content on the server. A security researcher who reviewed the pages said that perhaps the hackers were running some sort of SEO-scam scheme.
The scheme was likely designed to charge people for ebooks that are otherwise free, or just steal money without ever sending the ebooks, according to Jerome Segura, a security researcher at Malwarebytes.
The websites were spotted by Electronic Frontier Foundation senior researcher Dave Maass, who alerted Motherboard.
“A link with a .gov top-level domain lends an element of legitimacy to a hyperlink. In this case, someone could mistake these sites as a program sponsored by the state of Virginia,” Maass said. “If a spammer used a link like this in a phishing email, it could certainly trick a recipient.”
Segura said that these sites are “part of an automated campaign to hack outdated servers,” that run on an outdated version of Nginx server software.
“This is blackhat SEO exploiting vulnerable sites with the goal of promoting a scam,” Segura said, explaining that “the goal of this campaign is blackhat SEO to inject ‘free ebooks’ content. The attackers stole the template from another site, manybooks.net.”
Do you know of a hack or a security issue we should know about? You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzofb@vice.com
After Motherboard reached out to the Virginia government, a spokesperson said that the sites were created in 2007 and 2009, and that they were being taken down. As of this writing, the hijacked pages are not reachable anymore.
Both domains used to be legitimate Virginia government pages, one was used to promote a certificate for government employees, the other was an online career center. It’s unclear how long these malicious pages have been up.
“We found two of these sites on virginia.gov, but it’s possible there could be more,” Maass said. “This discovery should trigger a top-to-bottom audit of its websites to determine whether the damage is widespread and whether there are other obsolete subdomains that ought to be archived and closed down.”
The Virginia government spokesperson said that’s exactly what they will do.
“The [Virginia Information Technology Agency] will undertake a full audit of the Virginia.gov domain to verify the hosting and content responsibilities across the platform,” the spokesperson said in an email.
This story was updated to clarify that Dave Maass alerted Motherboard, not the government of Virginia, about the sites.
Subscribe to our new cybersecurity podcast, CYBER.
READ MORE HERE