Hackers Tried To Compromise Phones Of Tibetans
Hackers tried to break into the iPhones and Android devices of several Tibetans, some working for the office of the Dalai Lama, the Central Tibetan Administration, and the Tibetan parliament, according to a new report.
The hackers used exploits and spyware developed for the iOS and Android operating systems, and attempted to deliver them through carefully crafted phishing messages sent via WhatsApp, from people who pretended to be journalists, staffers of NGOs, and volunteers to Tibetan human rights groups, according to the report, published by the digital rights group Citizen Lab on Tuesday.
The researchers conclude that this hacking campaign was carried out by the same hacking group that targeted the Uyghur people living in China. At the end of last month, Google detailed a shocking campaign against the Muslim minority, where hackers used several exploits that at the time were unknown (these type of hacking tools are called zero-days, given that the company who makes the software targeted has had zero days to fix them.)
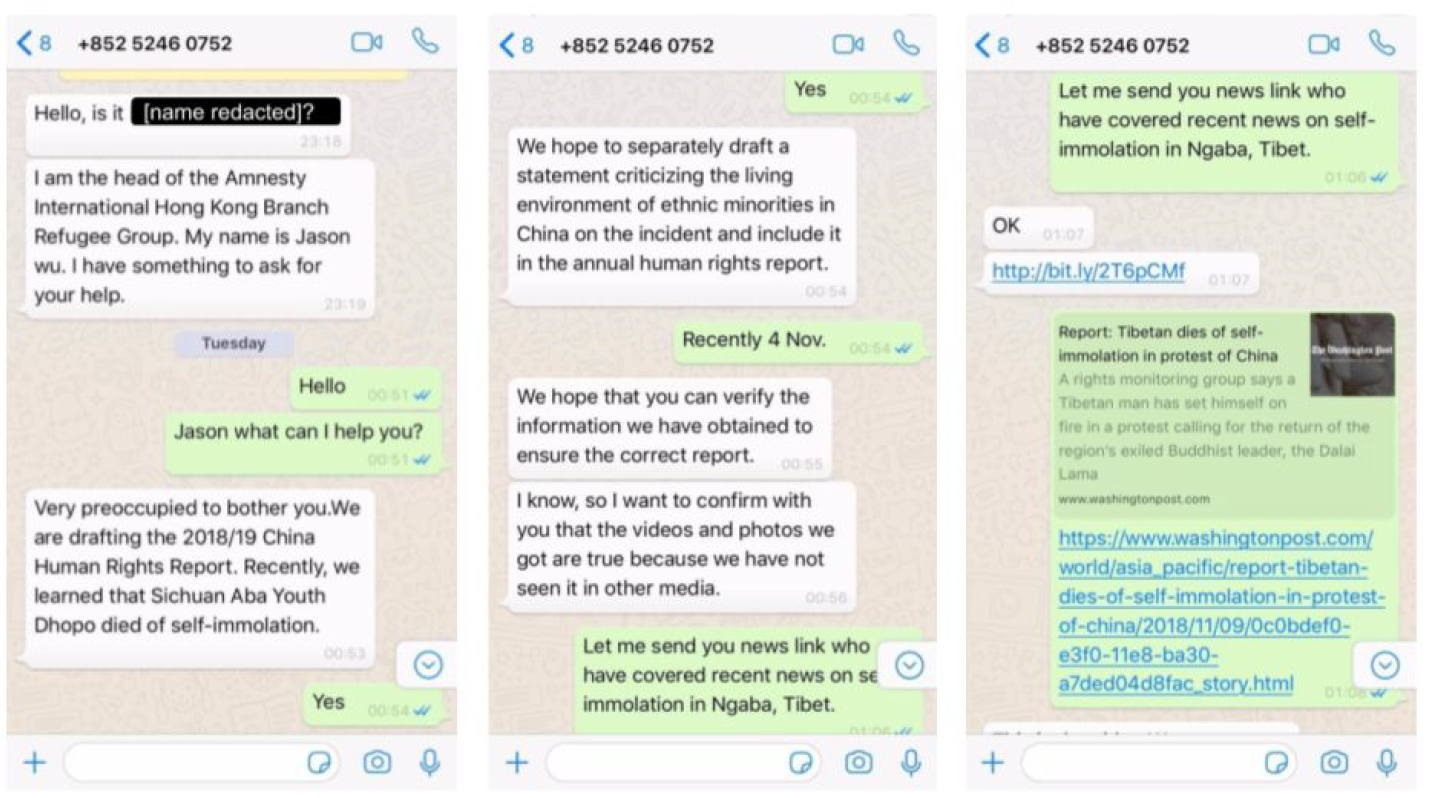
An example of a conversation between the hackers and a target. (Image: Citizen Lab.)
“One question about targeted attacks on civil society in general is: whose technology is helping the bad guys break into dissidents phones? For a long time, NSO Group and Pegasus seemed to be perhaps the only game in town, but now we see the emergence of a new player that appears to be linked to China,” Bill Marczak, the lead researcher who investigated the attacks, said in an interview. “They’re clearly a bit scrappier: using slightly out-of-date exploits to catch those who procrastinate with their updates, and they’re not necessarily going after ‘everything’ on the phone.”
Have a tip about a hack or a security incident? You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzofb@vice.com
Citizen Lab, which is based out of the Munk School at the University of Toronto, saw 15 hacking attempts. Despite the fact that some victims clicked on the malicious links, no one was hacked because they had up to date phones.
The campaign tracked by Citizen Lab appears to overlap with those revealed by Google Project Zero, which revealed the use of several iOS zero-days, and one detailed by security firm Volexity, which identified several websites used to spread Android malware.
“Based on the use of the same iOS exploits and similar iOS spyware implant between POISON CARP and the campaign described by Google Project Zero and server infrastructure connections with the Evil Eye campaign reported by Volexity, we determine that the three campaigns were likely conducted by the same operator or a closely coordinated group of operators who share resources,” Citizen Lab concluded in the report. “These incidents demonstrate a growing demand for exploitation of mobile devices. From an adversary perspective what drives this demand is clear. It is on mobile devices that we consolidate our online lives and that civil society organizes and mobilizes. A view inside a phone can give a view inside these movements.”
Google declined to comment. An Apple spokesperson sent the following statement: “Our customers’ data security is one of Apple’s highest priorities and we greatly value our collaboration with security researchers like Citizen Lab. The iOS issue detailed in the report had already been discovered and patched by the security team at Apple. We always encourage customers to download the latest version of iOS for the best and most current security enhancements.”
This story has been updated to mention the fact that Google declined to comment.
Subscribe to our new cybersecurity podcast, CYBER.
READ MORE HERE
