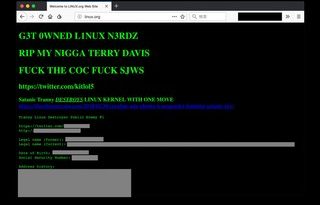
Hackers Have Been Quietly Targeting Linux Servers

Hacking campaigns linked to China have been exploiting vulnerabilities in Linux servers in an operation which successfully stayed under the radar for almost a decade.
Detailed by researchers at BlackBerry, the operation, linked to the interests of the Chinese government, is conducting hacking and cyber espionage against a wide array of industries for the purposes of intellectual property theft and data collection.
While the overall campaign is multi-platform, a newly uncovered part of it has been exploiting vulnerabilities in Linux since at least 2012 – and without the attackers having to update their offensive capabilities in that time.
“It’s newly discovered, but it’s nowhere near new. A lot of these tool-sets go back to 2012 and 2013 which is a ridiculous amount of time for an adversary to be able to use the same set of tools,” Eric Cornelius, chief product architect at Blackberry told ZDNet.
Linux is not typically a user-facing technology, so security companies tend to focus on it less, he explained. As a result, these hacking groups have zeroed in on that gap in security and leveraged it for their strategic advantage to steal intellectual property from targeted sectors for years without anyone noticing, he said.
“It’s critical for these servers to be up all the time; so what better place to put a root kit or a pervasive active tool than on a machine that’s going to be turned on all time?,” said Cornelius.
The attackers scan for Red Hat Enterprise, CentOS, and Ubuntu Linux environments across a wide range of industries, attempting to identify unpatched servers. From there it’s simply a case of establishing persistence on the network with malware.
Not only can this provide the attackers the access they need to sensitive information and data, but with the infection on the servers themselves, they can create a persistent back door into the network which provides them with a way back in whenever they like – so long as the compromise isn’t uncovered.
SEE: Cybersecurity: Let’s get tactical (ZDNet/TechRepublic special feature) | Download the free PDF version (TechRepublic)
And by compromising the servers, it’s much easier to exfiltrate data, as transfers of data out to command-and-control servers can be disguised as web traffic.
The attackers are careful to do as little damage as possible to the networks so as to avoid detection – and therefore keep campaigns up and running for as long as possible, which might be years.
“If they’d been encrypting or ransoming these machines, there would have been some response; but because they did no damage, there’s no reason for anyone to suspect anything was going on. It shows a high level of sophistication on behalf of the adversaries,” Cornelius explained.
However, over the course of the campaigns, the attackers managed to leave some evidence behind which allowed researchers to attribute the campaign to hackers working out of China with links to the Chinese government.
Part of the reason this was possible according to BlackBerry because this team is made up of sub-contractors. While they were highly efficient, they sometimes lacked operational security.
“Every time you deploy these tools, you betray some information and the teams behind this betrayed too much, they got a bit sloppy,” said Cornelius.
“We were able to do a good amount of correlation between the toolset, naming conventions and technical artefacts and start to see the picture”.
That’s led to BlackBerry linking this campaign to Winnti, a Chinese hacking operation across multiple groups which uses civilian contractors to aid the work of nation-state backed operations.
It’s highly likely that the campaign is still ongoing, still attempting to target unpatched or forgotten about Linux systems in addition to attacks against Windows. However, the simple way to avoid falling victim is to ensure that servers and operating systems are patched and up to date so hackers can’t exploit old vulnerabilities.
“These types of compromises are only prevented by good cyber hygiene, there’s no magic that can be done, there’s no silver bullet that an organisation can use to suddenly not be compromised,” said Cornelius.
“What this shows that in order to be secure against these adversaries, you have to be secure across all fronts; Windows, mobile, Linux and Macs,” he said.
READ MORE ON CYBERSECURITY
READ MORE HERE