Google Says Slap Some GUAC On Your Software Supply Chain
In brief Google has released a new open source software tool to help businesses better understand the risks to their software supply chains by aggregating security metadata into a queryable, standardized database.
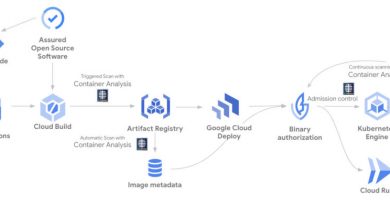
The Graph for Understanding Artifact Composition, or “GUAC” – pronounced like the avocado dip – “aggregates and synthesizes software security metadata at scale and makes it meaningful and actionable,” Google said in a blog post.
While modern upstream software supply chains have become rich with metadata and attestations, it’s “difficult or impossible” for most businesses to put that info into a unified view, Google claims.
“To understand something complex like the blast radius of a vulnerability, one needs to trace the relationship between a component and everything else in the portfolio – a task that could span thousands of metadata documents across hundreds of sources,” Google said.
Software supply chain attacks have been central to many major cybersecurity incidents in the past few years, like SolarWinds, Kaseya, and Log4j, and involve attackers injecting malicious code into software prior to its delivery to customers.
At RSA 2022, Microsoft’s Aanchal Gupta, head of the company’s Security Response Center, said supply chain attacks will continue to become more prevalent due to the tech world’s reliance on third-party and open source software, which he said is “not going to come down anytime soon.”
As an aggregator of metadata, GUAC is designed to collect data from a variety of sources, including software bill-of-materials platforms, vulnerability databases, and signed attestations, like Google’s own aptly named SLSA (pronounced “salsa”).
GUAC is able to collect data, ingest it from upstream sources, collate it into a single normalized source, and allows users to query it to get a software bill of materials, provenance, build chain, project security scorecard, a list of vulnerabilities and recent lifecycle events, Google claims.
Google says GUAC could help answer proactive security questions, like which components in a software ecosystem are most often used or which dependencies may be risky, as well as operational questions like whether new software meets security policies and reactive questions like how an organization is affected by a new vulnerability.
The GUAC project is open source and available on GitHub. Google said it’s still in the early development days and is only available as a proof of concept that can ingest data from SLSA, software bills of materials, and Scorecard documents. You can try it out – or inject some of your own helpful code – now.
FBI says Iranian hackers threatening Israel could come for US again
The FBI has released a private industry notification warning companies to beware of an Iranian hacking group known as Emennet Pasargad, which previously harassed US voters and launched disinformation campaigns during the 2020 presidential election.
Emennet is known for using hack-and-leak operations against victims, the FBI said, as well as using false-flag personas to shift blame elsewhere. The group appears to be opportunistic, and generally seems to have the goal of undermining public trust in private organizations and government institutions.
Most recently, the group was spotted targeting Israeli organizations using similar tactics, but the FBI said it was active within the US earlier this year, when it pulled off an attack against a US-based organization linked to an Iranian opposition group.
While opportunistic, Emennet does show some preference for its victims. Those at risk include any group linked to Iranian opposition groups, companies with websites running PHP or an externally accessible mysql database, as well as large companies with significant web traffic and a large customer base.
US officials have warned of increased cyber attack potential in the run up to the US midterms next month, but have also said they’re not concerned about foreign governments or their agents posing an actual threat to elections.
CISA wants to go SCuBA diving into your Microsoft 365 cloud
The Cybersecurity and Infrastructure Security Agency (CISA) has released an open source tool designed to audit Microsoft 365 deployments against the agency’s cloud security standards.
Available on GitHub as a PowerShell script, the software looks at Teams, SharePoint, Power Platform, Power BI, OneDrive, Exchange, Defender and Azure AD, and checks them against the Secure Cloud Business Applications (SCuBA) standards CISA announced in April.
SCuBA guidelines were developed for civilian executive branch agencies to “provide easily adoptable recommendations that complement each agency’s unique requirements and risk tolerance levels,” CISA said, and admits that the tools may not perform flawlessly for private organizations.
Still, “CISA recommends that all organizations utilizing cloud services review the baselines and implement practices therein where appropriate.” In testing, the agency ran the software on tenants with E3 or G3 and E5 or G5 Microsoft 365 licenses, and said it may still work in, but wasn’t tested for, deployments other than those.
While “ScubaGear” only supports Microsoft 365 for now, CISA said it plans to publish configuration baselines for Google Workspaces as well. “The publication of the GWS and M365 baselines will further CISA’s mission to secure the federal enterprise by addressing cybersecurity and visibility gaps within cloud-based business applications,” CISA said.
TSA shovels coal on railroad cybersecurity requirements
The Transportation Security Administration (TSA) has issued a directive to rail operators telling them its time to get serious about cybersecurity – and it’s not an option.
Citing “the ongoing cybersecurity threat to surface transportation systems” and attacks that could lead to “degradation, destruction, or malfunction” of such systems, the TSA is requiring [PDF] all designated freight railroad carriers and railroads to comply with four rules:
- A cybersecurity coordinator is required to be on call at all times
- All cybersecurity incidents have to be reported to CISA within 24 hours
- Operators must develop a cybersecurity incident response plan
- Operators must conduct vulnerability assessments and report them to the TSA within 90 days of the directive
To accomplish its objectives, the TSA is requiring rail operators to develop network segmentation policies, improve access controls, build continuous monitoring platforms, and develop a standard patching process to minimize risks of exploitation.
The US has more broadly required companies to submit cyber incident reports within 72 hours, but appears to be imposing stricter requirements on rail operators, which is unsurprising given rail is included in CISA’s list of critical infrastructure sectors.
The requirements shouldn’t be too difficult to implement, according to TSA administrator David Pekoske, because industry spokespeople helped develop the rules. “We are encouraged by the significant collaboration between TSA, [Federal Railroad Administration], CISA and the railroad industry in the development of this security directive.” ®
READ MORE HERE