From the ground up to the cloud: Microsoft’s Intelligent Security supporting CISOs’ cloud transformation

It’s no secret that Microsoft has embraced the cloud in a big way—from enterprise solutions like Microsoft Azure to Office 365 and Windows. But a recent research report by Forrester focuses on an equally important shift in our approach to security—integrating workforce and cloud security in ways that make them much easier for enterprise IT leaders to purchase and manage.
As Dark Reading’s Kelly Sheridan points out, Microsoft is focusing on “bringing protections to where people are moving their work: into the cloud.” Microsoft, like other cloud providers, is “stomping into the security market, ready to shake things up and address the weaknesses they see in today’s tools,” she adds.
Sheridan cites the Forrester research that includes a focus on Microsoft’s “plan to build security into each part of Azure, Office 365, and Windows”——a strategy, which, the researchers say, will be as disruptive to the security space as the cloud has been for the enterprise.
A shifting security challenge
Our emphasis on integration through and into the cloud, mirrors the shifts CISOs have made as their own enterprises have embraced the cloud, requiring them to coordinate cloud and on-premise security solutions.
As summarized succinctly in Sheridan’s Dark Reading post, Forrester’s research highlights Microsoft’s strengths in telemetry and artificial intelligence, which yield unparalleled insights into how attackers interact with not only our products, but also other applications that run on Windows and other Microsoft platforms.
The report also cites Microsoft’s efforts to target the enterprise market by “making security easy to buy and use,” Sheridan writes. Microsoft, she adds, “bundles technologies and simplifies deployment for security teams, which can use preconfigured security policies for new servers and containers.” From C-level execs to Sec-Ops, our customers tell us they are overwhelmed by the rapid pace at which new cyber threats are released in the wild. Microsoft believes there is a need for the industry to shift to this next generation of security defense.
Scale and integration
The Forrester report also notes that embedded solutions address one of the biggest challenges cloud-focused CISOs face: scalability.
“Scalability isn’t an issue,” Sheridan writes. “As infrastructure and applications grow, so do cloud platforms. Teams don’t need to worry about whether hardware can handle bandwidth upgrades or whether management servers can handle new endpoints.”
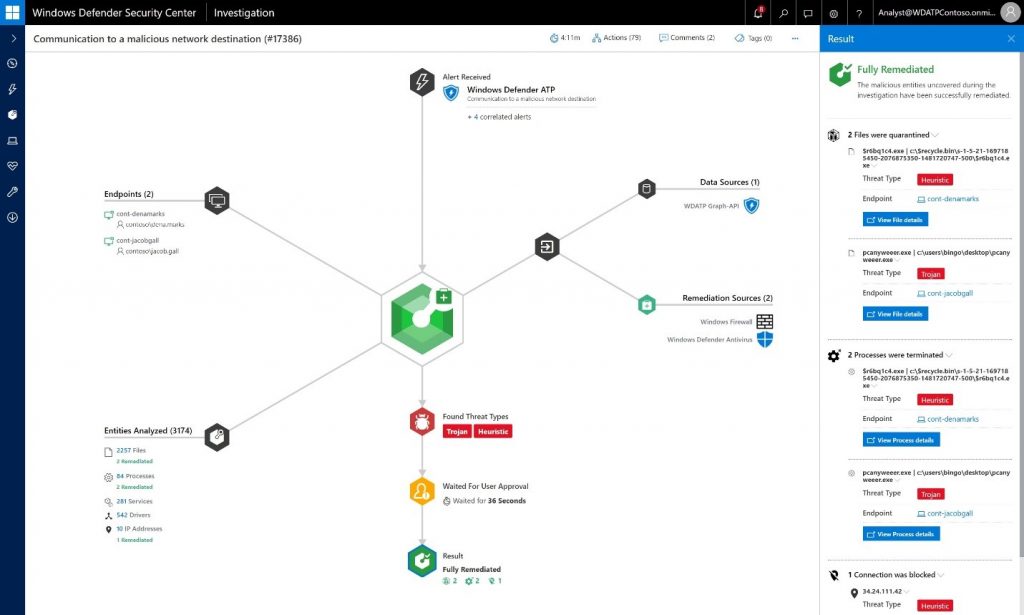
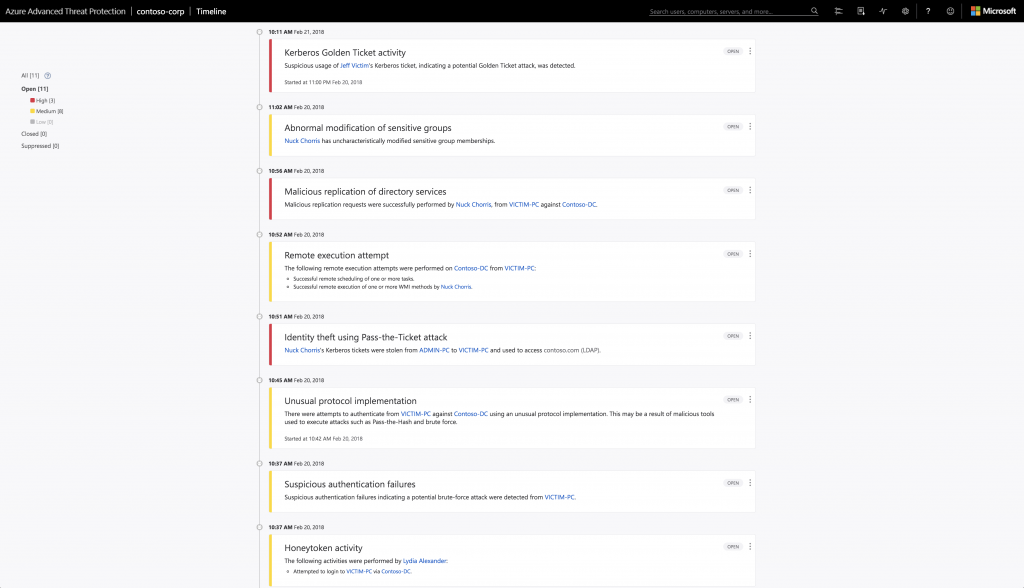
And we continue to expand the scope of our security offerings. At April’s RSA Conference 2018, Microsoft made a series of announcements that deepen our commitment to end-to-end security. Azure Sphere brings our security efforts to the connected microcontroller units (MCUs) that make up the Internet of Things (IoT), while a broad suite of technologies that together we call “Microsoft 365 Intelligent Security” emphasizes our commitment to integration. Intelligent Security offerings announced at RSA include a new API for Microsoft Graph that provides integrated data and alert reporting across security products, our Secure Score and Attack Simulator to help companies assess their security profiles, and additional support for strong authentication and threat prevention capabilities.
Disruption and drive
These shifts, according to Forrester, represent a significant disruption in the security marketplace. For CISOs, they also provide a strong argument for new thinking about security products in the enterprise and significant cost savings for moving to the cloud having security built in from the ground up. “Gone are the days when security leaders opted for separate antivirus tools in lieu of Windows Defender,” Sheridan writes. “Now many question the business’ choice to buy an endpoint suite when Microsoft’s services have security built in.”
At the same time, Forrester’s researchers caution against “going all in” with any single vendor, and we agree. Cybersecurity is a broad and complex space, and no one vendor can do it all. That’s why we’re working with microcontroller unit manufacturers on our IoT solutions, participating in a cybersecurity technology agreement with nearly 35 companies across the industry, and acquiring best-of-breed technology from innovative companies like Adallom and Aorato to bolster our capabilities in such areas as cloud security and malware detection. And along with the millions of threat indicators identified by the Intelligent Security Graph API, we work with a wide range of organizations to gather and share intelligence on threat attacks in real time. Together, these moves represent our commitment to work with all partners to secure the enterprise—a simple but powerful idea that, in the security space, may ultimately become the most disruptive force of all.
READ MORE HERE