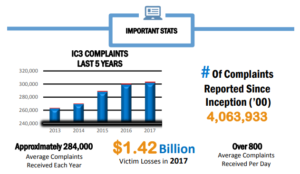
Free Speech Advocates Blast Amazon Over Threats Against Signal

On Tuesday, Moxie Marlinspike, founder of the secure messaging app Signal, posted a letter sent to him from Amazon threatening to suspend the company’s AWS account for using a technique called domain-fronting on its network. The technique is used to protect messages sent via the Signal’s messaging app from being tracked or censored in countries such as Egypt, Oman, Qatar and UAE, where the service is banned.
The move was admonished by anti-censorship and free speech advocates at the American Civil Liberties Union and the Electronic Frontier Foundation.
“Amazon is acquiescing to their business interests by banning the ability to do domain-fronting on their infrastructure,” said Daniel Kahn Gillmor, senior staff technologist at the ACLU. “What Amazon is effectively doing, by barring domain-fronting, is sending a message that nobody can rely on Amazon to help them enjoy freedom of speech. That’s a sad outcome. Amazon had the opportunity to stand up for the right thing here and they don’t appear to be taking it.”
The action by Amazon follows a similar move by Google, who earlier this year also threatened to push Signal off its platform if it continued to use the domain-fronting technique on its servers.
Domain-fronting, akin to hiding in plain sight, is used to obscure the true endpoint of a connection. The networking technique, first detailed in a paper (.PDF) by academics at the University of California Berkeley in 2015, uses HTTPS to communicate with a censored host while appearing, on the outside, to be communicating with a completely different, permitted host — in this case, Amazon and Google.
According to the Amazon letter sent to Signal and posted by Marlinspike, Amazon chastised him for using the Souq.com domain as part of Signal’s domain-fronting routine.
“You do not have permission from Amazon to use Souq.com for any purpose. Any use of Souq.com or any other domain to masquerade as another entity without express permission of the domain owner is in clear violation of the AWS Service Terms,” the letter read. “We will immediately suspend your use of CloudFront if you use third-party domains without their permission to masquerade as that third party.”
Marlinspike wrote, “With Google Cloud and AWS out of the picture, it seems that domain-fronting as a censorship circumvention technique is now largely non-viable in the countries where Signal had enabled this feature. The idea behind domain-fronting was that to block a single site, you’d have to block the rest of the internet as well. In the end, the rest of the internet didn’t like that plan.”
Domain-fronting first began to figure into the way the Android version of the secure messenger Signal works in some countries in 2016. Marlinspike, also Open Whisper Systems’ founder, explained the “blocking the rest of the internet” idea at the time: When a user sends messages through the service, it appears as if they’re normal HTTPS requests to Google.com. Thus, if a country wanted to block Signal messages, it would have to block significant portions of Google’s infrastructure.
That’s precisely what happened last month in Russia when the government cracked down on the use of the Telegram messaging app, which also used the domain-fronting technique on Google servers.
When Telegram disregarded an order by Russia’s Federal Security Service to hand over its messaging encryption keys to authorities, the Russian government blocked 18 million Google IP addresses in order to block the app. Doing so caused a major disruption of many Russia-based services and businesses.
Amazon and Google also have both cited concerns that domain-fronting is a technique that can also be used for nefarious purposes. There’s evidence for that: Last year, the cybercriminal gang APT29 used domain-fronting in order to secure backdoor access to targets for nearly two years before being caught by Matthew Dunwoody, principal consultant at FireEye. In that incident, APT29 used The Onion Router (TOR) and a TOR domain-fronting plugin called Meek to create a hidden, encrypted network tunnel, which appeared to connect to Google services over TLS.
“This tunnel provided the attacker remote access to the host system using the Terminal Services, NetBIOS and Server Message Block services, while appearing to be traffic to legitimate websites,” according to FireEye.
Researchers at CyberArk also identified domain-fronting as a tool that enables attackers to abuse content delivery networks to mask malware C2 traffic.
Nonetheless, “Amazon has no strong reason to disallow domain-fronting,” said Jeremy Gillula, a tech policy director at EFF, noting that there are many good things on the internet that could be used for nefarious reasons, but which should never be banned.
“I suspect AWS took a look at what happened in Russia and said it didn’t want to risk having its customers end up being collateral damage in a fight with government censors,” Gillula said. “I understand Amazon’s calculation, but disagree with the decision they came to.”
Both Amazon and Google did not return requests for an interview ahead of publication of this article. However, last week, Amazon outlined its position in a blog post announcing a new “domain protection tool” called Amazon CloudFront, which makes makes it easier for the company to crack down on domain-fronting.
In April, Google released a statement regarding the technique: “Domain-fronting has never been a supported feature at Google, but until recently it worked because of a quirk of our software stack. We’re constantly evolving our network, and as part of a planned software update, domain-fronting no longer works. We don’t have any plans to offer it as a feature.”
“It’s unfortunate that Amazon is doing this. Amazon and Google both have an opportunity to explain to their customers why they are taking a principled stance against censorship. Instead, they are letting the censors win and free speech takes the hit,” Gillula said.
Gillula and Gillmor’s positions on domain-fronting echo similar concerns by other free-speech advocates. In April, Peter Micek, general counsel at Access Now, wrote, “Google knows this block will levy immediate, adverse effects on human rights defenders, journalists and others struggling to reach the open internet.”
In his blog post, Marlinspike said the Signal team was considering other “more robust” system alternatives to domain-fronting. “[T]hese ecosystem changes have happened very suddenly. Our team is only a few people, and developing new techniques will take time,” he wrote. “Moreover, if recent changes by large cloud providers indicate a commitment to providing network-level visibility into the final destination of encrypted traffic flows, then the range of potential solutions becomes severely limited.”
(Image Credit: Signal.org)
Read More HERE