Four Ways Layered Security Will Improve Your Detection and Response

It’s widely understood by cybersecurity professionals today that it’s no longer a case of if your organization gets attacked online but when. Trend Micro blocked more than 20.4 billion threats in the first half of 2018 alone, and the ready availability of “as-a-service” toolkits will continue to make cybercrime a hugely attractive and profitable venture. If attacks are inevitable, it’s more important than ever to improve your detection and response to help minimize their impact. Most analysts agree: claiming organizations must move away from an unrealistic prevention only mind-set.
Under attack
There’s no doubt that modern IT organizations are under more pressure than they’ve ever been from malicious outsiders. Trend Micro’s own stats from our latest midyear report reveal a 16% rise in reported US breaches from the second half of 2017 to the first six months of this year. Breaches which exposed over one million records saw an even bigger jump over the period, of 67%. That’s not to mention the growing threat from cryptocurrency mining malware, where we saw detections rise 141%. Even ransomware, although slowing down in terms of volume growth (3%), was still detected by our tools over 380,000 times in the first half of 2018.
When faced with these threats, organizations must of course do their best to block them outright. But when that’s not possible there should be tools in place to minimize the length of time key systems and data are exposed for. Current estimates suggest the “dwell time” during which attackers go undetected inside systems stands today at just over 100 days. That’s clearly unacceptable given what’s at stake: major financial losses, reputational damage and possible customer attrition.
The fantastic four
So, what’s the answer? Despite what you might hear, there’s no such thing as a silver bullet. Instead, what’s needed is a blend of threat detection techniques, optimized so the right technique is used at the right time to deal with a particular threat.
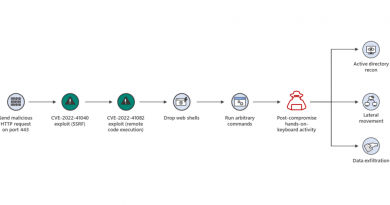
Here are four specific ways that layered security can improve detection and response:
|
|
Modern organizations threaten to be overwhelmed by the complexity of today’s threat landscape, and can struggle to drive value from multiple point solutions. Trend Micro’s answer is connected threat defense, a layered security approach that gives you a better way to quickly protect, detect, and respond to new threats while simultaneously improving visibility and streamlining investigation across your organization.
Read More HERE