Fake PoC On GitHub Lures Researchers To Download Malware
Threat actors have crafted a novel ploy designed to bait cybersecurity researchers into a trap by posting a fake proof-of-concept (PoC) to GitHub that is actually a backdoor.
Researchers at Uptycs outlined the scam on Wednesday in a blog breaking down the discovery of the bogus PoC. They said the PoC contained a malicious downloader, or dropper, hidden inside the code. Once downloaded, the dropper delivers the malware payload that eventually executes a Linux Bash script that is disguised as a kernel-level process. A Bash scrip is a simple text files that automates commands.
“As their primary users, security researchers rely on PoCs to understand potential vulnerabilities by way of innocuous test,” co-authors of the blog Nischay Hegde and Siddartha Malladi wrote. They said the malware “leverages the make command to create a kworker file and adds its file path to the bashrc file, thus enabling the malware to continually operated within a victim’s system” in order to gain persistence.
The malicious PoC operates as a downloader, with the malware payload capable of data theft via exfiltration. Targeted is the system’s hostname and username and the malware’s ability to scrape a computer’s home directory, Hegde and Malladi said. An attacker can also gain full access to a target system by adding their SSH Key to the targeted system’s authorized_keys file.
“SSH (Secure Shell) keys are an access credential that is used in the SSH protocol and they are foundational to modern Infrastructure-as-a-Service platforms such as AWS, Google Cloud, and Azure,” according to a breakdownoftheterm by vendor JumpCloud.
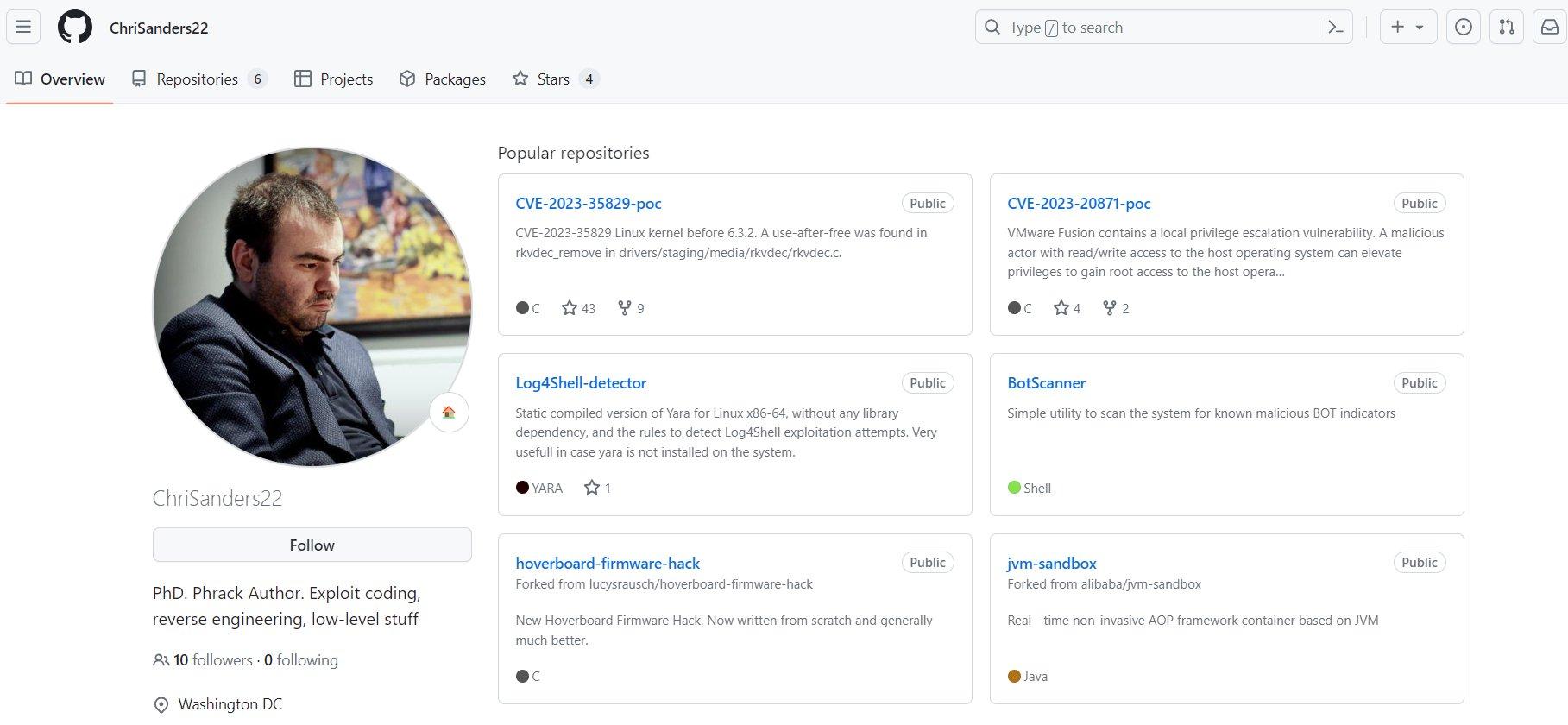
The fake PoC exploits the critical vulnerability (CVE-2023-35829). The malware-laced PoC was shared widely before the malicious contents were discovered and removed from GitHub, researchers said.
Uptycs researchers said they encountered unusual activity while testing PoCs of various CVEs. They said they noticed suspicious activity such as unexpected network connects, unusual data transfers and unauthorized system access attempts.
It’s not the first time GitHub has been used for nefarious purposes. In June, Vulncheck researchers reported finding malicious GitHub repositories under the guise of a fake company.
Security researchers contacted by SC Media said the method uncovered by Uptycs was interesting, but Mike Parkin, senior technical engineer at Vulcan Cyber, said the target audience was uniquely positioned to quickly discover and eliminate the attack.
“If they are experimenting with a PoC someone else developed, they are likely to do so in a virtual machine, which can be quickly reset if something goes wrong,” said Parkin.
“I would be shocked, and a bit disappointed, if any experienced malware researchers were caught by this,” he said.
READ MORE HERE


