Exposing Infection Techniques Across Supply Chains and Codebases

The Enduring Security Framework (ESF) Software Supply Chain Working Panel, a collaboration between the public and private sector, has provided industry best practices and principles which vendors, developers, and consumers may reference for their own security and protection against supply chain attacks. These references are divided across distinct responsibilities as they relate to all parties involved in the supply chain, as each one plays an important role in ensuring supply chain security. Organizations are strongly encouraged to adopt a robust Supply Chain Risk Management (SCRM) program to enhance operational security against supply chain threats and minimize organizational risks.
This document provides guidance for vendor best practices which vendors are strongly encouraged to reference and follow. The document offers guidance on industry standards to assist vendors with:
- Acting as a liaison between developer and consumer
- Ensuring the integrity and security of software via contracts
- Handling software releases and updates
- Being responsible for the notification and mitigation of vulnerabilities
Additionally, in order to mitigate the risks of supply chain compromise, vendors are encouraged to develop a comprehensive SCRM program. This template can serve as a baseline to implement a vendor specific SCRM program which enhances supply chain security and fosters trust between vendors and consumers.
This document provides guidance on industry best practices and principles that developers are strongly encouraged to reference follow. The document provided offers guidance on industry standards to assist developers with:
- Planning security requirements
- Designing secure software
- Implementing Security Features
- Maintaining the security of software and their underlying infrastructure
This document provides guidance on industry best practices and principles consumers are strongly encouraged to reference and allow. The document provided offers guidance on industry standards to assist consumers with the acquisition, deployment, and operational phases of software supply chains. Furthermore, small and medium-sized businesses can use this handbook from the Cybersecurity and Infrastructure Security Agency (CISA) as a resource for securing supply chains.
Additionally, we’ve provided some further commonsense recommendations:
- Vet before you get: Before integrating an open-source tool or library, research its reputation. Look for reviews, testimonials, and any known security issues. Understand the risks associated with utilizing third party frameworks.
- Code review: Always review the code you’re about to run, especially if it’s from an untrusted source. Look out for suspicious functions calls and their sequence like exec(requests.get(…)), as well as process creation utilizing methods such as subprocess.popen.
- Check the maintainers: Ensure the project is maintained by reputable individuals or organizations. A well-known and active maintainer is less likely to let malicious code slip through.
- Network monitoring: Monitor outgoing network requests from your applications. Unexpected requests to unknown domains can be a red flag.
- Use a reputable security solution: Modern security solutions can detect malicious behaviors and block the malicious payload from being downloaded or executed.
- Restrict Execution: If possible, run scripts in environments where they don’t have full access to the system or network.
- Use dependency scanners: Tools like Snyk, or Guarddog can automatically scan your project’s dependencies for known vulnerabilities and potential malicious activities.
- Limit permissions: Run open-source applications with the least privilege necessary. This way, even if there’s malicious code, its potential impact is limited.
- Isolate environments: Use virtual environments or containers to isolate the open-source application and, if applicable, isolate components from your main system. This can prevent potential malicious activities from affecting your primary environment.
- Engage with the community: Join forums or mailing lists related to the open-source project you’re using. Active communities often discuss vulnerabilities and best practices.
- Backup regularly: Always have backups of your critical data and configurations. If something goes awry due to a malicious component, you will be able to restore it to a safe state.
In this post we explored a case study using a combination of techniques such as exec smuggling, employing platforms such GitHub and repositories such as PyPi packages to infect individuals and organizations. Additionally, we’ve provided individuals, developers, vendors, as well as organizations resources, they can use to enhance their defensive posture against supply chain attacks.
Supply chain attacks continue to increase in frequency with third-party incidents accounting for 17% of intrusions in 2021 compared to less than 1% in 2020. Codebases continues to be a high value target for threat actors which, according to the European Union Agency for Cybersecurity (ENISA), accounts for an estimated 66% of supply chain attacks.
Given the stealth, potency, and risk of supply chain attacks, it’s clear that organizations must prioritize comprehensive security measures, including rigorous assessments of all third-party components and continuous monitoring of integrated systems.
To protect against various supply chain threats, we recommend Trend Vision One™️ which enables security teams to continuously identify the attack surface, including known, unknown, managed, and unmanaged cyber assets. Trend Vision One™️ automatically prioritizes risks, including vulnerabilities, for remediation, considering critical factors such as the likelihood and impact of potential attacks. Trend Vision One™️ offers comprehensive prevention, detection, and response capabilities backed by AI, advanced threat research, and intelligence. This leads to faster mean time to detect, respond, and remediate, improving the overall security posture and effectiveness.
When uncertain of intrusions, behaviors, and routines, assume compromise or breach immediately to isolate affected artifacts or tool chains. With a broader perspective and rapid response, an organization can address these and keep the rest of its systems protected. Organizations should consider a cutting-edge multilayered defensive strategy and comprehensive security solutions such as Trend Micro™ XDR that can detect, scan, and block malicious content across the modern threat landscape.
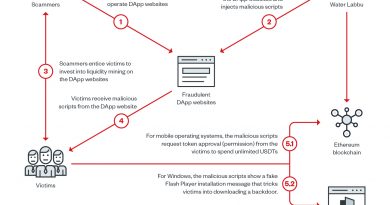
Often these attacks are multistage in nature, with the the first stage starting with a download that uses a Python networking module to download additional stages. The most common techniques to obfuscate the URL are base64 and byte-sequences.
To help protect supply-chains and codebases we’ve compiled a list of malicious techniques we commonly see through threat hunting this type of behavior.
The following threat hunting query table lists potentially useful queries for threat hunting as well as dangerous method combinations within packages which could be used to create potential semgrep rules:
Read More HERE