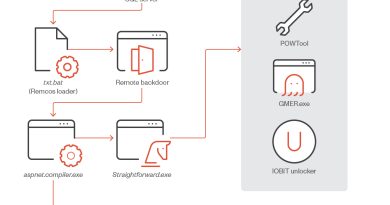
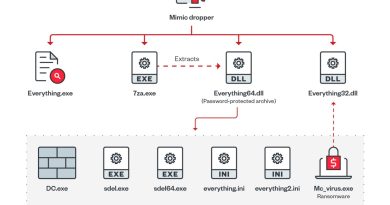
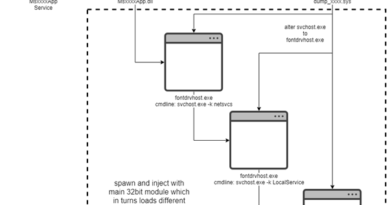
CVE-2024-21412: DarkGate Operators Exploit Microsoft Windows SmartScreen Bypass in Zero-Day Campaign

The decrypted request content is as follows:
1000|87|283|Yes|6.1.7|||”
Conclusion
In this research, a follow-up to our Water Hydra APT Zero Day campaign analysis, we explored how the DarkGate operators were able to exploit CVE-2024-21412 as a zero-day attack to deploy the complex and evolving DarkGate malware. We also explored how security bypass vulnerabilities can be used in conjunction with open redirects in technologies such as the Google Ads ecosystem to proliferate malware and abuse the inherent trust that organizations have in basic web technologies.
To make software more secure and protect customers from zero-day attacks, the Trend Zero Day Initiative works with security researchers and vendors to patch and responsibly disclose software vulnerabilities before APT groups can deploy them in attacks. The ZDI Threat Hunting team also proactively hunts for zero-day attacks in the wild to safeguard the industry.
Organizations can protect themselves from these kinds of attacks with Trend Vision One, which enables security teams to continuously identify attack surfaces, including known, unknown, managed, and unmanaged cyber assets. Vision One helps organizations prioritize and address potential risks, including vulnerabilities. It considers critical factors such as the likelihood and impact of potential attacks and offers a range of prevention, detection, and response capabilities. This is all backed by advanced threat research, intelligence, and AI, which helps reduce the time taken to detect, respond, and remediate issues. Ultimately, Trend Vision One can help improve the overall security posture and effectiveness of an organization, including against zero-day attacks.
When faced with uncertain intrusions, behaviors, and routines, organizations should assume that their system is already compromised or breached and work to immediately isolate affected data or toolchains. With a broader perspective and rapid response, organizations can address breaches and protect their remaining systems, especially with technologies such as Trend Micro™ Endpoint Security™ and Trend Micro Network Security, as well as comprehensive security solutions such as Trend Micro™ XDR, which can detect, scan, and block malicious content across the modern threat landscape.
Trend Protections
The following protections exist to detect and protect Trend customers against the zero-day CVE-2024-21412 (ZDI-CAN-23100).
Trend Vision One Model
- Potential Exploitation of Microsoft SmartScreen Detected (ZDI-CAN-23100)
- Exploitation of Microsoft SmartScreen Detected (CVE-2024-21412)
- Suspicious Activities Over WebDav
Trend Micro Cloud One – Network Security & TippingPoint Filters
- 43700 – HTTP: Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability
- 43701 – ZDI-CAN-23100: Zero Day Initiative Vulnerability (Microsoft Windows SmartScreen)
Trend Vision One Network Sensor and Trend Micro Deep Discovery Inspector (DDI) Rule
- 4983 – CVE-2024-21412: Microsoft Windows SmartScreen Exploit – HTTP(Response)
Trend Vision One Endpoint Security, Trend Cloud One – Workload and Endpoint Security, Deep Security and Vulnerability Protection IPS Rules
- 1011949 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability (CVE-2024-21412)
- 1011950 – Microsoft Windows Internet Shortcut SmartScreen Bypass Vulnerability Over SMB (CVE-2024-21412)
- 1011119 – Disallow Download Of Restricted File Formats (ATT&CK T1105)
- 1004294 – Identified Microsoft Windows Shortcut File Over WebDav
- 1005269 – Identified Download Of DLL File Over WebDav (ATT&CK T1574.002)
- 1006014 – Identified Microsoft BAT And CMD Files Over WebDav
Indicators of Compromise (IOCs)
Download the IOC list here.
Read More HERE