Chip flinger TSMC warns ‘WannaCry’ outbreak will sting biz for $250m
Chipmaker TSMC has warned that a previously disclosed virus infection of its Taiwanese plant may cost it up to $250m.
The malware struck on Friday, and affected a number of computer systems and fab tools over two days.
“The degree of infection varied by fab,” the firm said in an update on Sunday. “TSMC contained the problem and found a solution. As of 14:00 Taiwan time, about 80 per cent of the company’s impacted tools have been recovered, and the company expects full recovery on August 6.”
Although unnamed in its statement, TSMC execs reportedly blamed a variant of WannaCry, aka WannaCrypt, for the infection during the course of follow-up conference calls.
TSMC warned that the incident is likely to “cause shipment delays and additional costs”.
“We estimate the impact to third quarter revenue to be about 3 per cent, and impact to gross margin to be about one percentage point,” it said. “The company is confident shipments delayed in third quarter will be recovered in the fourth quarter 2018, and maintains its forecast of high single-digit revenue growth for 2018.”
Sales hit
The chipmaker had previously forecast revenues of $8.45bn to $8.55bn in its September quarter. A 3 per cent loss would shave this by up to $250m, though actually losses may come out lower, and execs have already revised down revenue losses to no more than 2 per cent, Bloomberg reported.
TSMC added that it was working with its customers to develop revised shipment schedules. TSMC – which supplies components to Apple iPhones, AMD, Nvidia, Qualcomm, Broadcom and others – said malware spread across its systems after an infected sub-component of an unspecified tool was connected to its network.
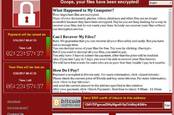
74 countries hit by NSA-powered WannaCrypt ransomware backdoor: Emergency fixes emitted by Microsoft for WinXP+
British malware reverse-engineer Marcus Hutchins famously halted the spread of WannaCry across NHS networks and elsewhere after registering a domain that turned out to act as a kill switch, preventing further spread of the malware in cases where infected hosts could pin the domain. Even so, the software nasty is still capable of causing a problem in closed systems such as factories, UK infosec guru Kevin Beaumont told El Reg.
“Factory networks sometimes don’t have internet access so can’t reach a kill switch,” Beaumont said. “WannaCry is still one of the biggest infections seen in AV detections.”
This sort of thing is not unprecedented. Last March, around eight months after the original May 2017 malware outbreak, WannaCry crash landed on the factory systems of US aerospace giant Boeing.
TSMC pointed to a silver lining in its malware-occulted short-term outlook – the security breach could have been a lot worse. “Data integrity and confidential information was not compromised,” it said. “TSMC has taken actions to close this security gap and further strengthen security measures.” ®
Sponsored: Following Bottomline’s journey to the Hybrid Cloud
READ MORE HERE
