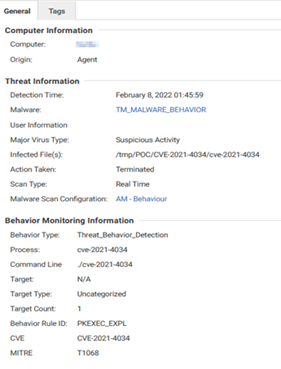
Recent Cyberattacks Target Open-source Web Servers
Malicious actors take advantage of people’s reliance on web servers to perform attacks like remote code execution, access control bypass, denial of service, or even cyberjacking the victim servers to mine cryptocurrencies. Read More HERE…