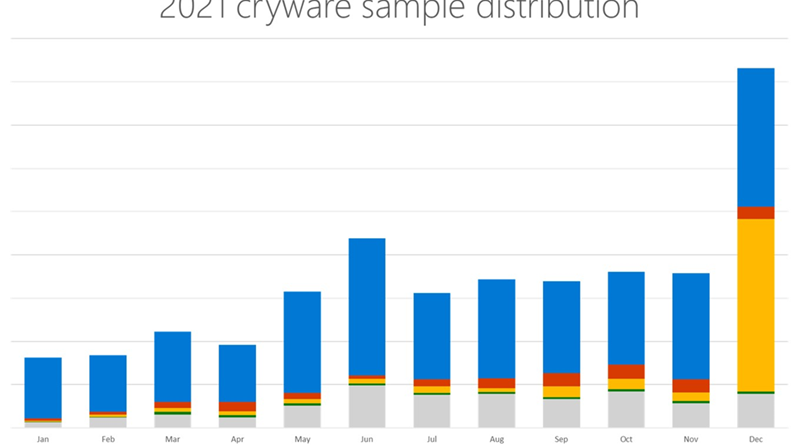
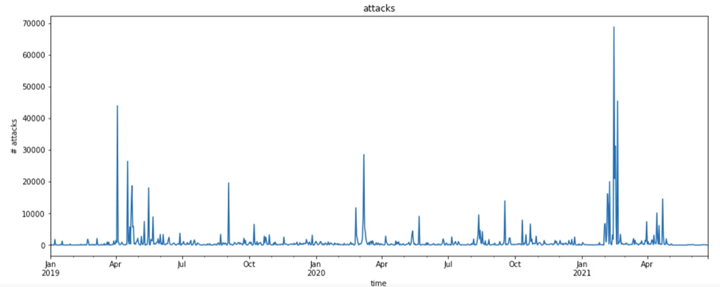
How to improve risk management using Zero Trust architecture
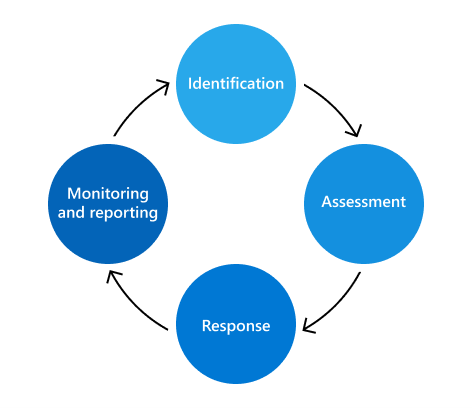
Risk management plays a critical role in helping organizations with their security posture enhancement. Taking insider incidents as an example, they are not only costly to organizations but also time-consuming to be contained. As such, the ROI is maximized in effectively protecting the organizations’ assets as well as ensuring their business operations. Risk management is an ongoing activity. Are the long-established risk management programs in the enterprises staying on top of the evolving digital and threat landscapes?
The post How to improve risk management using Zero Trust architecture appeared first on Microsoft Security Blog. READ MORE HERE…