North Korean threat actor targets small and midsize businesses with H0lyGh0st ransomware
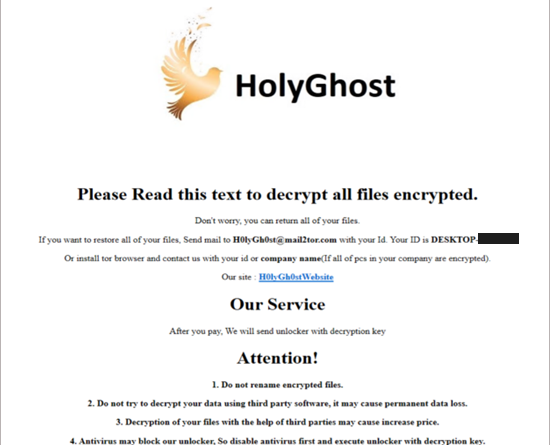
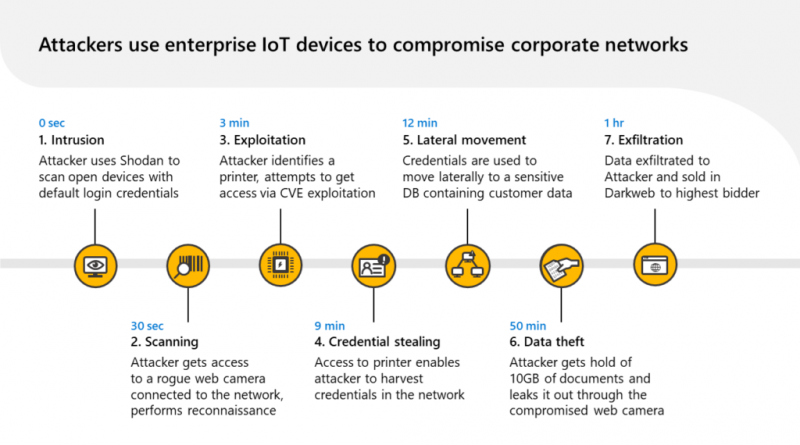
A group of actors originating from North Korea that MSTIC tracks as DEV-0530 has been developing and using ransomware in attacks since June 2021. This group, which calls itself H0lyGh0st, utilizes a ransomware payload with the same name.
The post North Korean threat actor targets small and midsize businesses with H0lyGh0st ransomware appeared first on Microsoft Security Blog. READ MORE HERE…