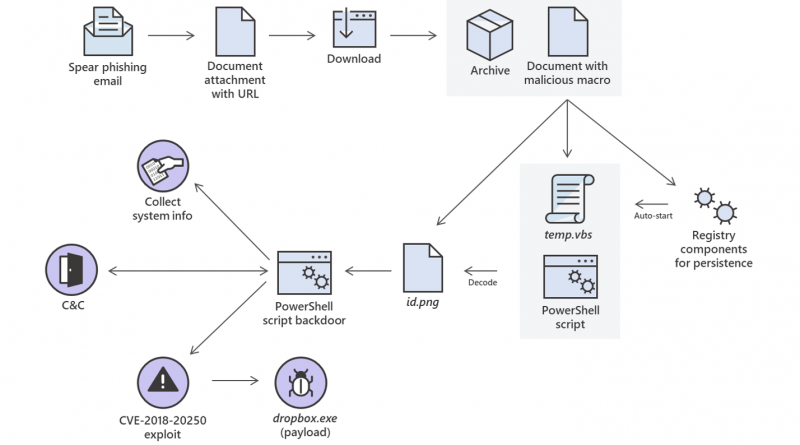
Analysis of a targeted attack exploiting the WinRAR CVE-2018-20250 vulnerability
A complex attack chain incorporating the CVE-2018-20250 exploit and multiple code execution techniques attempted to run a fileless PowerShell backdoor that could allow an adversary to take full control of compromised machines.
The post Analysis of a targeted attack exploiting the WinRAR CVE-2018-20250 vulnerability appeared first on Microsoft Security. READ MORE HERE…