August Patch Tuesday: A Quiet Month for Microsoft Trend Micro


The August Patch Tuesday proves to be a calmer month for Microsoft, compared to the more eventful July security bulletin. This is evident in the short list of only 44 patched vulnerabilities published this month, of which seven are noted as critical and the rest as important. Eight were also submitted via the Trend Micro Zero Day Initiative.
What is notable for this month is the inclusion of three vulnerabilities in Print Spooler, given how flaws in this service have garnered much attention in the last month.
More print spooler bugs
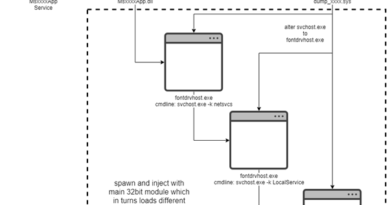
From June to July, Microsoft grappled with vulnerabilities in print spooler. Adding to its urgency was the discovery that one vulnerability, dubbed PrintNightmare, was actively exploited during that time. The company released a critical out-of-band (OOB) patch ahead of the July Patch Tuesday to quickly address the problem. This month, the three bugs in print spooler could allow either privilege escalation or remote code execution (RCE). Among its flaws, the RCE CVE-2021-36936 is the most notable for being one of the three zero-days this month.
A fix for PetitPotam
Another previously disclosed zero-day vulnerability is in Windows LSA (CVE-2021-36942). In late July Microsoft dealt with PetitPotam, an exploit for this vulnerability. The exploit can be used to attack Windows domain controllers or other Windows servers. Microsoft described PetitPotam as a “classic NTLM Relay Attack,” and can be mitigated as such. This update should block the LSARPC interface and further protects against NTLM relay attacks.
Updates for Microsoft Edge (Chromium-based)
This month’s security update guide also includes seven CVEs for Chrome. Even though these vulnerabilities are not from any Microsoft product, Microsoft Edge (Chromium-based) uses Chromium Open Source Software (OSS). The inclusion was done to inform users that the latest version of Microsoft Edge (Chromium-based) is no longer affected by the said vulnerabilities. Google had addressed these vulnerabilities recently, with Microsoft Edge also releasing the necessary updates for its browser prior the August Patch Tuesday.
Other notable vulnerabilities
Aside from the mentioned zero-days in Print Spooler and Windows LSA, the third one for this month is a privilege escalation vulnerability (CVE-2021-36948) in Windows Update Medic Service, a background feature introduced in Windows 10 to fix errors in Windows Update and prevent these errors from blocking system updates.
Other components that had critical vulnerabilities included Windows TCP/IP, Windows Graphics Component, Scripting Engine, and Remote Desktop Client. Vulnerabilities for Microsoft Office, Microsoft Word, SharePoint, Windows Defender, and Windows 10 Update Assistant were also patched this month.
Trend Micro Solutions
A proactive, multilayered approach to security is key against threats that exploit vulnerabilities — from the gateway, endpoints, networks, and servers.
The Trend Micro™ Deep Security™ solution provides network security, system security, and malware prevention. Combined with Vulnerability Protection, it can protect user systems from a wide range of upcoming threats that might target vulnerabilities. Both solutions protect users from exploits that target these vulnerabilities via the following rule:
- 1011077 – Microsoft Internet Explorer Scripting Engine Memory Corruption Vulnerability (CVE-2021-34480)
- 1011079 – Microsoft Windows Services NFS ONCRPC XDR Driver Remote Code Execution Vulnerability (CVE-2021-26432)
TippingPoint® Next-Generation Intrusion Prevention System (NGIPS) is a network traffic solution that uses comprehensive and contextual awareness analysis for advanced threats that exploit vulnerabilities.
TippingPoint protects customers through the following rule:
- 40071: HTTP: Microsoft Windows JScript Memory Corruption Vulnerability (CVE-2021-26232)
- 40090: UDP: Microsoft Windows RPCXDR Kernel Driver Out-of-Bounds Write Vulnerability (CVE-2021-26432)
Read More HERE