APT34 Deploys Phishing Attack With New Malware

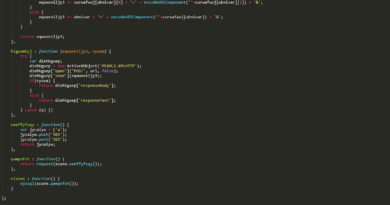
We analyzed a new malware, which we attribute to the APT34 advanced persistent threat (APT) group, that was involved in a phishing attack. In August, our threat hunting activities identified a malicious document we investigated to have been used during a targeted phishing attack by the group. The malicious document is responsible for dropping a new malware we have called Menorah (taken from the malicious document’s dropped executable, detected by Trend Micro as Trojan.W97M.SIDETWIST.AB), and for creating a scheduled task for persistence. The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware.
During our investigation, there was little information about the victims targeted by this malware. But the file that APT34 used for this attack is called “MyCv.doc,” a license registration form related to the Seychelles Licensing Authority. However, we noted that the document contained pricing information in Saudi Riyal, which might indicate that the targeted victim was an organization inside the Kingdom of Saudi Arabia. This blog post provides an analysis of the group’s latest malware and its capabilities, shows the attack process, and details the attackers’ infrastructure.
APT34 background and targeting
APT34 is a covert cyberespionage group that specializes in targeting organizations and illicit activities within the Middle East. As we’ve previously covered, APT34 primarily focuses on collecting sensitive intelligence, employing spear phishing campaigns, and abusing advanced techniques to infiltrate and maintain access within targeted networks. Our monitoring suggests this group operates with a high degree of sophistication and seemingly vast resources, posing a significant cybersecurity challenge regionally and beyond.
Notably, APT34 has been involved in high-profile cyberattacks against a diverse range of targets in the Middle East, including government agencies, critical infrastructure, telecommunications, and key regional entities. The group consistently develops and enhances tools, aiming to reduce security solutions and researchers’ detection. In this research on APT34, we observed the group transitioning to the employment of novel data exfiltration methods. Researchers from NSFOCUS published a report on a new variant of the SideTwist malware utilized by APT34.
Infection routine
Read More HERE