Ancient Solaris Patch Missed The Mark
A vulnerability first detected and “resolved” years ago in Oracle’s Unix OS, Solaris, has resurfaced, necessitating a fix in Big Red’s latest quarterly patch batch.
Rather than a Lazarus-like return from the dead, it’s more a case of security researchers discovering that the original fix, for a component that’s become known as Solaris Availability Suite Service, isn’t good enough.
Oracle agreed with security researchers at Trustwave, who flagged up the issue, and pushed out a new fix.
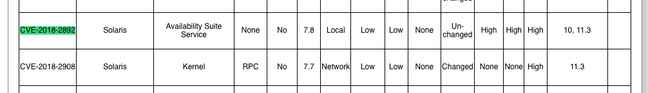
The (CVE-2018-2892) vulnerability lends itself solely to local exploitation – it’s not a remote hacking threat – so it could be worse, though it would be foolish to ignore it on insecure systems. The vulnerability rates a 7.8 classification on the Common Vulnerability Scoring System (CVSS) 3.0 system, well towards the upper end of the 1-10 scale.
The “easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Solaris executes to compromise Solaris”, according to a bug listing on the CVE database.
The practical upshot is that users running Oracle Solaris 10/11 and running Sun StorageTek Availability Suite (AVS) for the filesystem need to patch their systems to resolve an incompletely fixed flaw rooted in security bugs in legacy versions of the tech.
The vulnerability is a memory corruption bug that would allow an attacker to write malicious code to memory and execute it with kernel-level (highest) privileges. The flaw was first discovered in 2007 and made public during CanSec West 2009, a security conference held in Vancouver, Canada. A fix was applied shortly after the event.
Trustwave found that the original fix was insufficient.
“Exploiting the vulnerability can only be done by a locally logged in user (no direct remote exploitation),” the researchers said. “The vulnerability lets you execute code in the root/kernel context. Typically, this would be a root shell.” ®
Sponsored: Following Bottomline’s journey to the Hybrid Cloud
READ MORE HERE