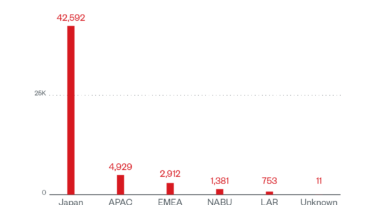
An In-Depth Look at ICS Vulnerabilities Part 1


In 2021, there were significant changes in the methods used by cyber attackers. More advanced destructive supply chain attacks also came to the surface this year. This has created an anxious environment, driving developments in cyber defense and the discovery of ICS-related CVEs.
2021’s timeline overview of major OT and ICS cyber incidents shows that modern criminal operations have become so developed that a service industry has emerged with a common business model – Ransomware-as-a-Service (RaaS).
Service operators providing RaaS maintain a customizable platform that they offer to users who want to carry out criminal projects. Known recently-active ransomware groups include Maze, Lockbit, REvil, and DarkSide, though their activity levels can vary.
The Colonial Pipeline and Kaseya Attacks
Around the middle of 2021, Revil and DarkSide got on the United States government’s bad side. The groups’ service was used to trigger two of the most severe ransomware attacks of the year—the Colonial Pipeline and Kaseya supply chain attacks.
The Colonial Pipeline incident, resulting in a US $4.4 payout to attackers, was conducted using DarkSide’s RaaS platform. The Kaseya attack was done using Revil’s service, taking advantage of zero-day authentication bypass” vulnerability, CVE-2021-30116.4. When the Revil group demanded their USD $70 million ransom they claimed to have infected over a million devices. After these two attacks both DarkSide and Revil went quiet, likely due to increased attention from government and law enforcement organizations, with Revil surfacing again in October of 2021.
However, we can expect continued development on RaaS, including new RaaS platforms that integrate functionality from the previous platform.
BlackMatter ransomware, for example, includes tools and techniques from the Darkside, Revil, and LockBit 2.0 ransomware families.6 Our researchers suspect but have not confirmed that BlackMatter is the DarkSide group resuming operations under a changed name.
Most recently, as of December 2021, Emotet and Conti both have resurfaced using advanced ex-ploitation of the Log4Shell vulnerability to accomplish their goals.
U.S. President Joe Biden’s May 2021 Executive Order, Improving the Nation’s Cybersecurity, specifically addressed the rise in supply chain attacks. With this Executive Order, the U.S. government began putting in place regulations designed to prevent such attacks, and one of the biggest changes among these was cre¬ating a mandate for Software Bills of Materials (SBOMs) to be provided for each related exchange. These SBOMs will likely be critical documents in the push to improve industrial cyber defense and prevent supply chain attacks.
In part two of the series, we’ll further discuss ICS vulnerabilities using MITRE ATT&CK. We’ll look into the sectors affected and their risk levels.
Read More HERE