Alphabet’s Chronicle Releases VirusTotal Enterprise
Chronicle, the cybersecurity business under Alphabet, releases a major update to VirusTotal geared toward corporate threat hunters.
Chronicle, the independent cybersecurity business under Alphabet, today is releasing a major update to VirusTotal, dubbed VirusTotal Enterprise. The new offering combines VirusTotal’s existing capabilities with new tools, features, and an interface for corporate security pros.
Alphabet, the parent company of Google, Nest, and other ventures, announced Chronicle in January. At the time, Chronicle was the latest program to graduate from X, Alphabet’s tech incubator. It was created to help tech pros detect cyberattacks before they did harm through the combination of a security analytics platform and VirusTotal, which Google bought in 2012.
Chronicle has expressed a focus on enterprise security from the start. This marks VirusTotal’s first major release since Chronicle made its debut earlier this year. Under Alphabet, the platform has grown from increased scalability of data collection, processing, and search. Now, it’s leveraging this expansion to help businesses detect, organize, and address security alerts.
“We’re bringing enterprise expertise in Chronicle to make the product more useful for the cases enterprises are going to be facing,” says Mike Wiacek, Chronicle co-founder and chief security officer.
Security pros can use the tool to search for malware samples with VirusTotal Intelligence, look for future malware samples using VT Hunt with YARA, analyze malware relationships using VT Graph, and automate all of this with VirusTotal’s API. Below, a description of what’s new:
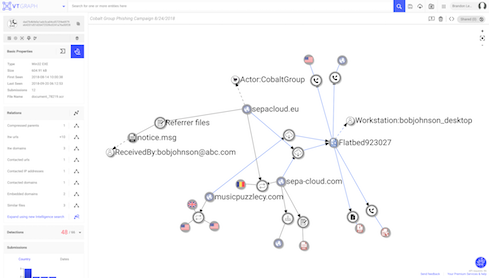
Private Graph
Businesses using VirusTotal Enterprise will have access to Private Graph, a feature VirusTotal announced earlier this year to create visualizations of malware relationships while integrating internal corporate information and keeping it all private from other VirusTotal users.
In studying different forms of malware, Wiacek explains, security pros want to know how different forms of malware relate to one another. They can build a giant mesh of which files relate to one another, which relate to different IP addresses, which link to different forms of malware, and how all of their behaviors interrelate. This is all possible with VirusTotal Graph.
“They’re trying to use that knowledge to discover new malware and new features and functionality related to it,” Wiacek says.
But practitioners don’t always want to share enterprise assets (people, departments, machines) publicly, so they requested a way to keep some graphs hidden from the VirusTotal community. Unlike traditional graphs, private graphs aren’t visible to other users on the platform.
Enterprise users on VirusTotal have different concerns than security researchers, Wiacek explains. “An enterprise analyst has different concerns around privacy and data,” he adds. A university researcher looking into an attack might not have the same concerns around keeping the process under wraps as someone trying to protect customers’ information.
With Private Graph, security teams can create investigations restricted to the people collaborating on it. They can add their own data elements, combined with VirusTotal data, to visualize threats and compare internal and external data. For example, if someone’s machine was infected, you can enter it on a graph and compare that threat with others seen in the wild.
Private graphs can automatically identify and extract threat commonalities from nodes to pinpoint indicators of compromise. Owners of private graphs can share their graphs with other private groups, Wiacek adds.
Ramping Up Malware Search
Chronicle reports VirusTotal Enterprise increases search speed by 100x using new malware n-gram content searches and improves search accuracy by looking for additional parameters: spam emails with a common visual layout, for example, or common icons across files.
“Traditionally, if you’re a commercial customer, you can write custom malware signatures to match files, and match files to see a particular malware strain you’re looking for,” Wiacek explains. “Really, you can enhance and improve speed with which researchers use the VirusTotal corpus to compare malware at scale,” he adds, noting that the new capabilities in VirusTotal Enterprise can accelerate searches from a few hours to seconds.
Malware analysis is also getting an update: Users will have access to more details about uploaded files, included embedded domains, IP addresses, and interest-ranked strings. The search tool lets them look for links across files, behaviors, and relationships, says Wiacek.
Enterprise Management Tools
VirusTotal is adding another layer of security with this release by letting customers use their existing two-factor authentication to access VirusTotal Enterprise accounts. A new API management for corporate groups will keep internal user directories synced with VirusTotal.
Related Content:

Black Hat Europe returns to London Dec. 3-6, 2018, with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
Kelly Sheridan is the Staff Editor at Dark Reading, where she focuses on cybersecurity news and analysis. She is a business technology journalist who previously reported for InformationWeek, where she covered Microsoft, and Insurance & Technology, where she covered financial … View Full Bio
More Insights
Read More HERE