328 weaknesses found by WA Auditor-General in 50 local government systems

Perth city
Image: Getty ImagesThe Auditor-General of Western Australia on Wednesday tabled a report into the computer systems used at 50 local government entities, revealing 328 control weakness across the group.
It was Auditor-General Caroline Spencer’s intention to list the entities, but given the nature of her findings, all case studies included in Local Government General Computer Controls [PDF] omit entity, and system, names.
“Included in the case studies are real life examples of how extremely poor general computer controls can result in system breaches, loss of sensitive and confidential information and financial loss,” Spencer said. “They serve as important reminders of the need to remain ever vigilant against constant cyber threats.”
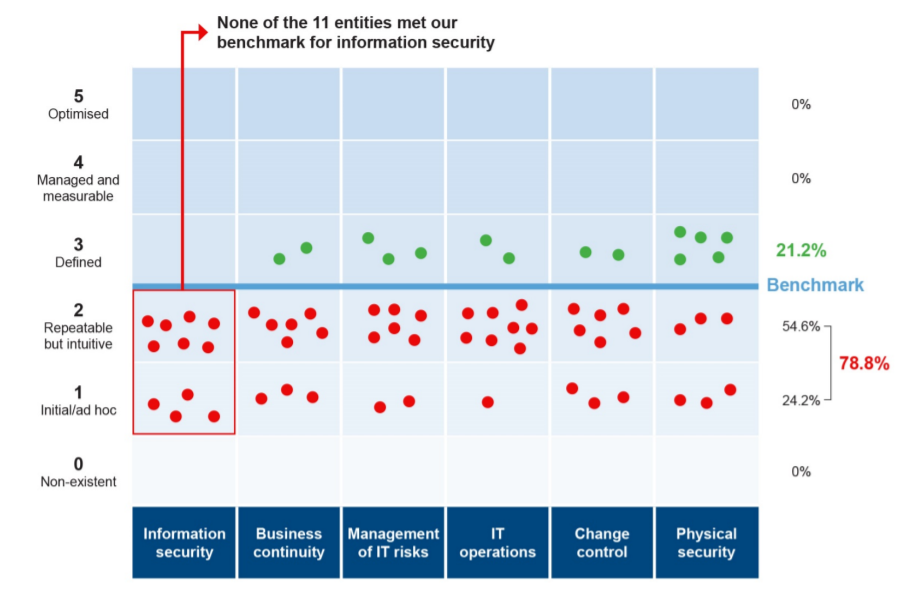
The report states that none of the 11 entities that the Auditor-General performed capability maturity assessments on met minimum targets. For the remaining 39, general computer controls audits were conducted.
The audit probed information security, business continuity, management of IT risks, IT operations, change control, and physical security.
Of the 328 control weaknesses, 33 rated as significant and 236 as moderate. Like last year, nearly half of all issues were about information security.
2019-20 capability maturity model assessment results
Image: Office of the Auditor GeneralThe capability assessment results, meanwhile, showed that none of the 11 audited entities met the auditor’s expectations across the six control categories, with 79% of the audit results below the minimum benchmark.
“Poor controls in these areas left systems and information vulnerable to misuse and could impact critical services provided to the public,” the report added.
“Five of the entities were also included in last year’s in-depth assessment and could have improved their capability by promptly addressing the previous year’s audit findings but, overall, did not discernibly do so.”
Among the findings were entities having a poor awareness of cyber threats, with one case study revealing a user’s account details were stolen because of a phishing attack that was not detected or prevented by the entity’s security controls.
“The attack resulted in a fraudulent credit card transaction on the user’s corporate credit card, which was immediately cancelled,” the report said. “Further investigation by the entity revealed the attacker downloaded 10GB of entity information in the form of sensitive emails.”
Another common weakness was that entities did not have policies, procedures, and processes to effectively manage technical vulnerabilities. At one entity, public facing and internal systems sat in the same network; the same entity also did not monitor devices on its network.
Many entities were also not managing privileged access to their networks and systems.
One entity was found to not have changed the password for the default network administrator account since 2002, even though various staff who knew the password had since left.
“We found instances where this account was used out of office hours and the entity was unable to explain this use,” the report said.
Probing the management of IT risks, weaknesses found included no policies and procedures to document, assess, review, and report IT risks; key risks were not documented, meaning entities were left unaware if appropriate controls were in place to protect their information; and entities had not reviewed their risk registers within a reasonable time.
IT operations, meanwhile, also revealed many weaknesses, including a lack of user access reviews, no logging of user access and activity, a lack of incident management procedures, and no requirement for IT staff privy to certain sensitive information being required to complete a background check.
“At one entity, staff could redirect payments for council rates, infringements, licence and application fees to another bank account by changing a file hosted on a shared server,” the report details. “Access to the server was not appropriately controlled because staff used a shared generic account to access and manage the server.”
Physical security was also flagged as weak, with one example showing an entity had no monitoring process regarding its server room, meaning anyone could access it.
Further weaknesses under the physical security banner included no backups and no appropriate environmental controls to protect IT infrastructure.
The report provided six recommendations, one for each of the security types audited.
These included implementing appropriate frameworks and management structures, identifying IT risks, and patching.
MORE FROM THE OAG
READ MORE HERE
