UK govt dept website that campaigns against encryption hijacked to advertise … payday loans
A website developed for the UK Home Office’s 2022 “flop” anti-encryption campaign has seemingly been hijacked to push a payday loan scheme.
The pwn on the government’s No Place to Hide campaign, which cost over half a million pounds to produce, was first spotted by tech policy expert Heather Burns. The website originally featured a daring stunt involving a parent and child locked in a box, and was greeted with negative reception when it was unveiled three years ago.

Privacy is for paedophiles, UK government seems to be saying while spending £500k demonising online chat encryption
As The Register reported at the time, the campaign was much broader than expected. Coordinated by ad agency M&C Saatchi, the feeling was that it would target Facebook Messenger, but the final draft instead took aim at end-to-end technology as a whole.
It featured the same messaging that’s pushed by the government today: that e2e enables child abuse and drug trafficking, and inhibits law enforcement operations.
Most of the website remains unchanged, however. Burns noticed that as of Tuesday there was a new section plonked in the middle of the home page pushing a payday loan scheme from Leicestershire-registered Wage Day Advance.
According to the website the promotional text links to (see below – https://www.wagedayadvance.co.uk/), its company name is Chojin Ltd, reference number 732880, and it is regulated by the UK’s Financial Conduct Authority. It offers payday loans, same-day loans, loans for those with bad credit or no guarantor, and more products. We note the FCA has a notice up on its own page about the company stating that “individuals are using the details of this firm to suggest they work for the genuine firm. We call this a cloned firm and it is typically part of a scam.” So buyer beware and call the switchboard number it lists to be sure.
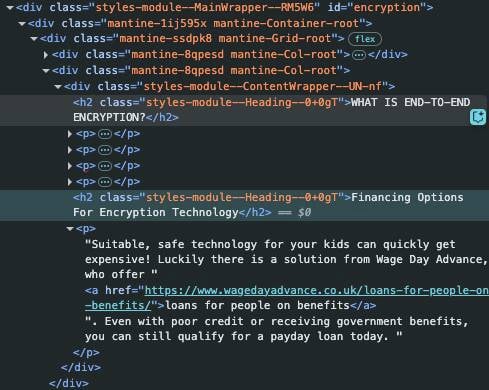
Page source of the Home Office’s “No Place to Hide” webiste at the time of publication – click to enlarge
The Register contacted both the Home Office and Wage Day Loans about the finding on Tuesday June 24, and by very early Wednesday morning on June 25 the payday loans section of the website had been removed. By 0930 UK time on Wednesday, it had re-appeared.
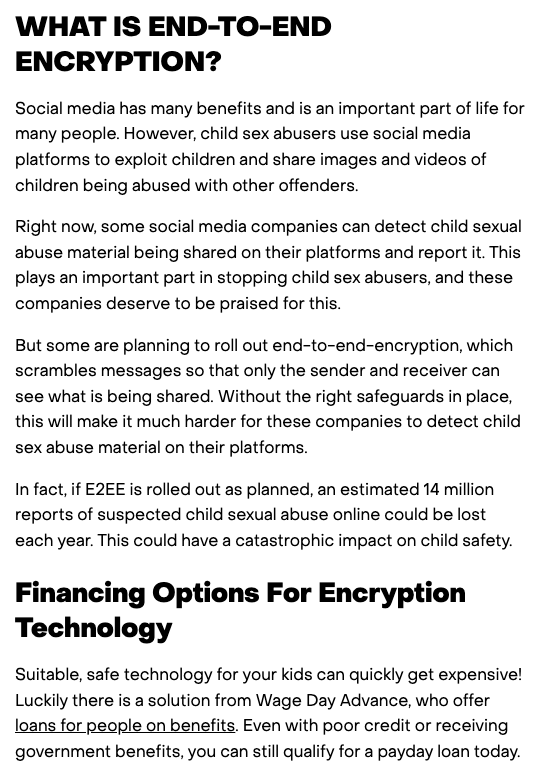
Screenshot of no place to hide (.org.uk) on morning of 25 June, taken by Connor Jones – click to enlarge
With a subheading that read “Financing Options For Encryption Technology,” the short section on the No Place to Hide website advertised the notorious high-interest loans designed for people in financial hardship.
“Suitable, safe technology for your kids can quickly get expensive,” it reads. “Luckily there is a solution from Wage Day Advance, who offer loans for people on benefits. Even with poor credit or receiving government benefits, you can still qualify for a payday loan today.”
Burns said the finding may be yet another example of a growing trend whereby legitimate, trusted domains and their abandoned web pages are being hijacked by groups pushing SEO-optimized AI slop.
She pointed to a recent story by 404 Media, which found domains owned by Nvidia, Stanford University, NPR, and the US government were hijacked similarly to advertise various topics.
The publication found more than 62,000 AI-generated articles on an old Nvidia events webpage, for example, many of which focused on extremely NSFW topics. Nvidia removed the site within two hours of being contacted, saying that the website was unaffiliated with the company.
It was a similar story with a subdomain of the US government-owned vaccines.gov and the others, which reportedly only comprised a small portion of the total affected domains.
Speaking from personal experience, Burns said it’s common for organizations such as these to outsource web development to an agency, particularly if it’s for a short-lived campaign.
Often, the websites that are returned are used for a short while but later abandoned, leaving junior staff with no idea why the domain exists.
She suspects that it is through these junior web admins letting the hijackers in via one of the slew of spammy emails they tend to receive every day.
As for ownership of these sites, like Nvidia, organizations involved with their development and limited upkeep could reasonably wash their hands of the responsibility of what happens to them after the campaign’s goals are achieved.
“The problem is, to the Home Office and the charities which put their names and logos on it, it’s not their problem either,” she blogged.
“Because the campaign budget was spent and the money got out the door, and the KPIs were hit, and so this campaign, to them, was a resounding success.
“End of.”
The Home Office did not respond to questioning. Wage Day Loans said it was unaware of the situation.
A Wage Day spokesperson said on Tuesday: “All SEO for Wage Day Advance is outsourced, we did not request that link placement and were not aware of it. We have subsequently asked for it to be removed.”
The company did not respond when asked who was responsible for its SEO. ®
READ MORE HERE

