Uncovering a macOS App Sandbox escape vulnerability: A deep dive into CVE-2022-26706
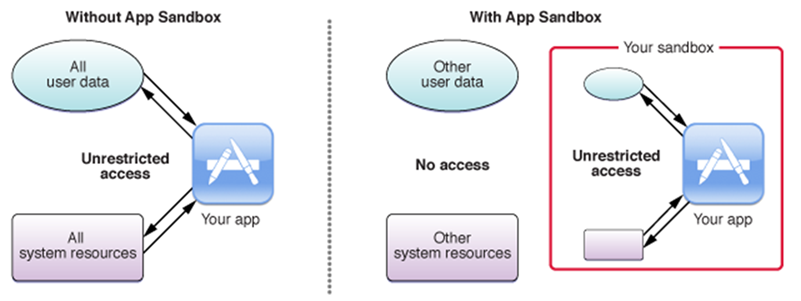
Microsoft uncovered a vulnerability in macOS that could allow specially crafted codes to escape the App Sandbox and run unrestricted on the system. We shared these findings with Apple, and fix for this vulnerability, now identified as CVE-2022-26706, was included in the security updates on May 16, 2022.
The post Uncovering a macOS App Sandbox escape vulnerability: A deep dive into CVE-2022-26706 appeared first on Microsoft Security Blog. READ MORE HERE…