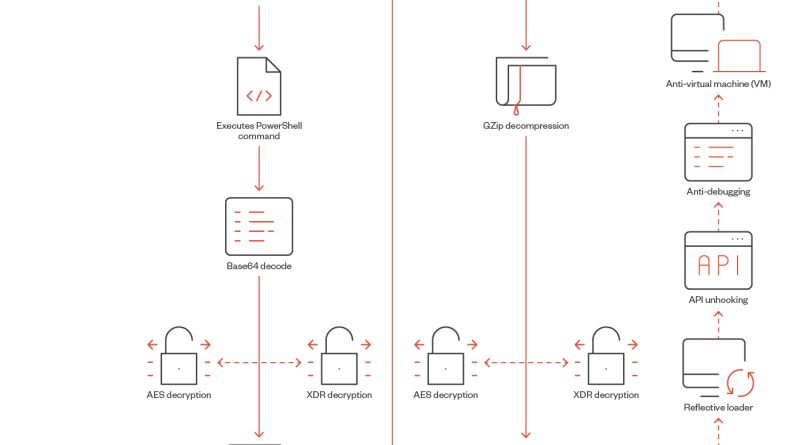
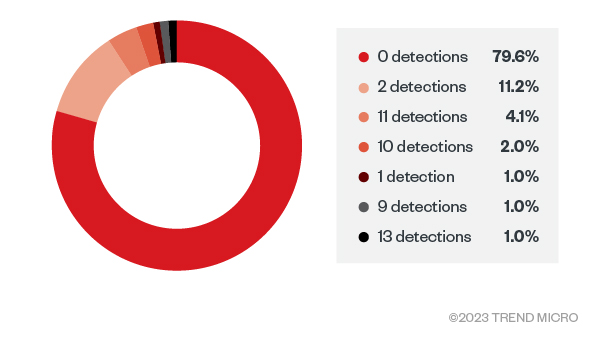
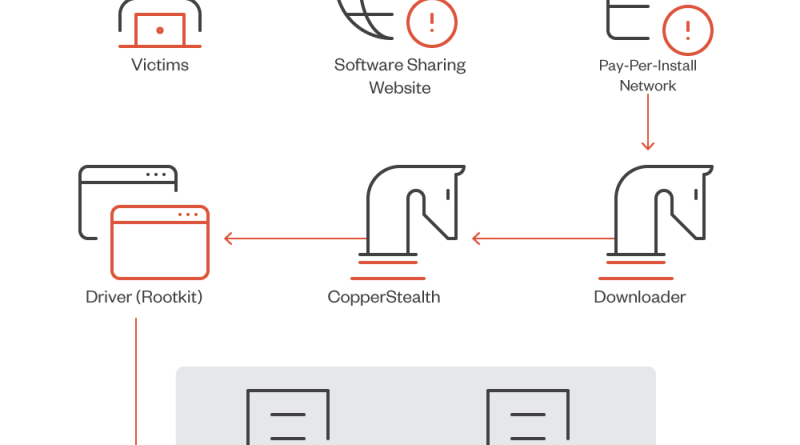
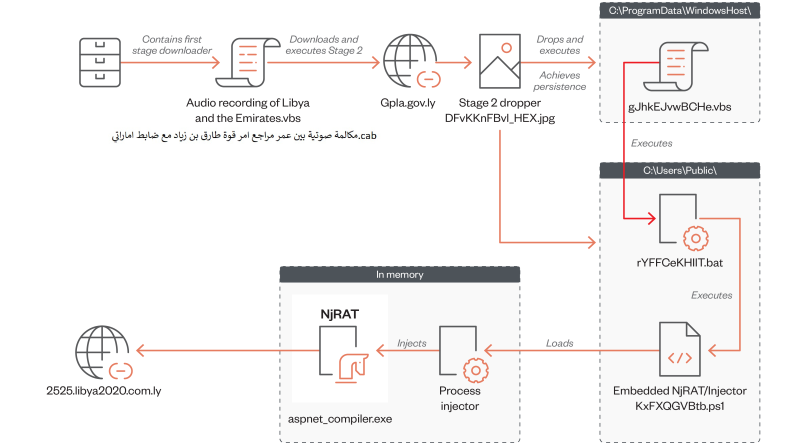
SeroXen Incorporates Latest BatCloak Engine Iteration
We looked into the documented behavior of SeroXen malware and noted the inclusion of the latest iteration of the batch obfuscation engine BatCloak to generate a fully undetectable (FUD) .bat loader. This is the second part of a three-part series documenting the abuse of BatCloak’s evasion capabilities and interoperability with other malware. Read More HERE…