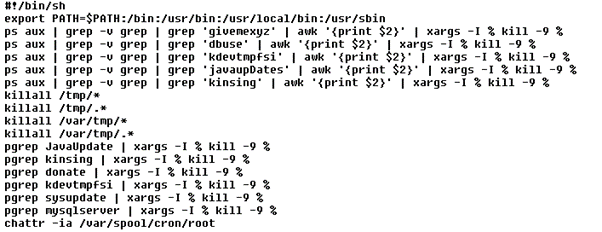
Earth Bogle: Campaigns Target the Middle East with Geopolitical Lures
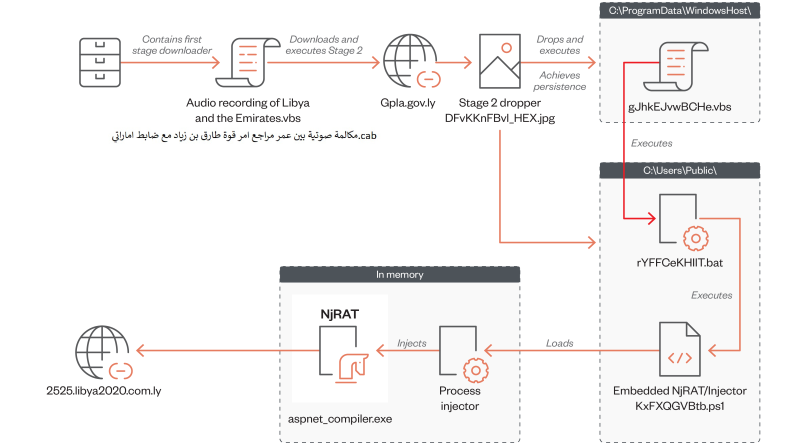
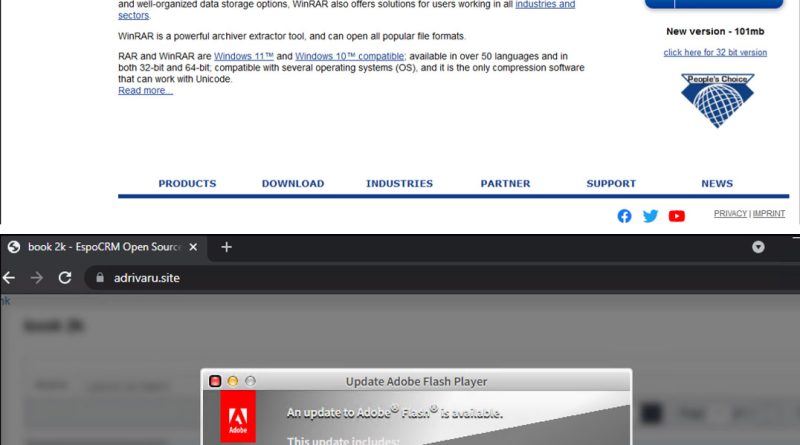
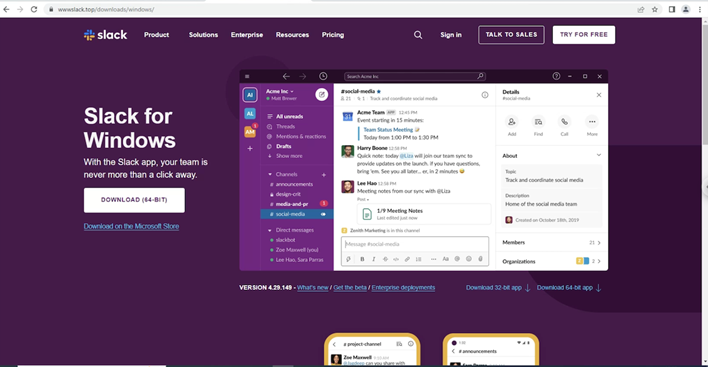
We discovered an active campaign ongoing since at least mid-2022 which uses Middle Eastern geopolitical-themed lures to distribute NjRAT (also known as Bladabindi) to infect victims across the Middle East and North Africa. Read More HERE…