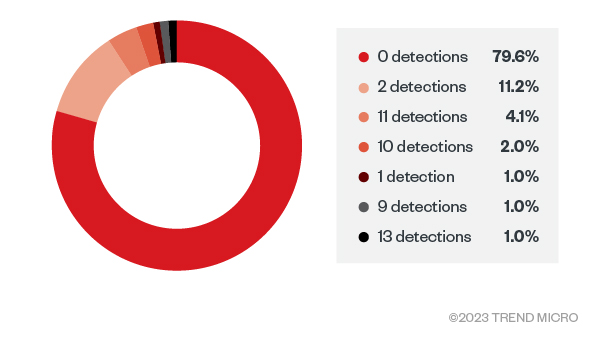
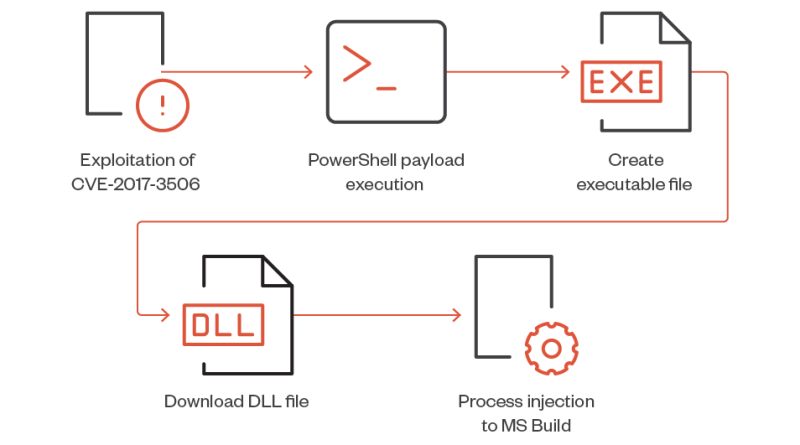
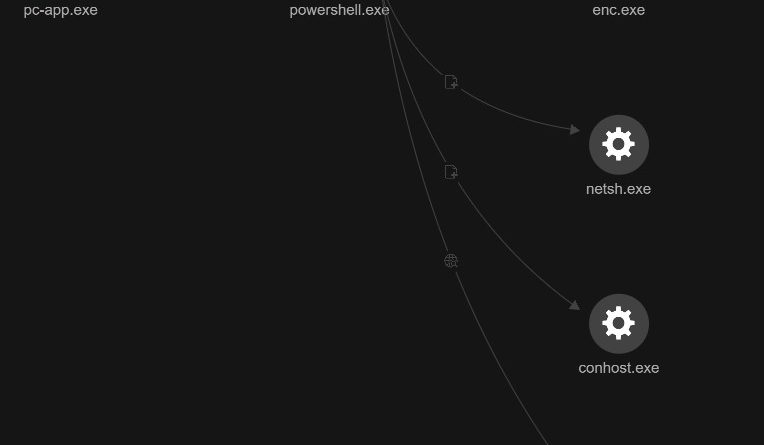
Analyzing the FUD Malware Obfuscation Engine BatCloak
We look into BatCloak engine, its modular integration into modern malware, proliferation mechanisms, and interoperability implications as malicious actors take advantage of its fully undetectable (FUD) capabilities. Read More HERE…