Impulse Team’s Massive Years-Long Mostly-Undetected Cryptocurrency Scam
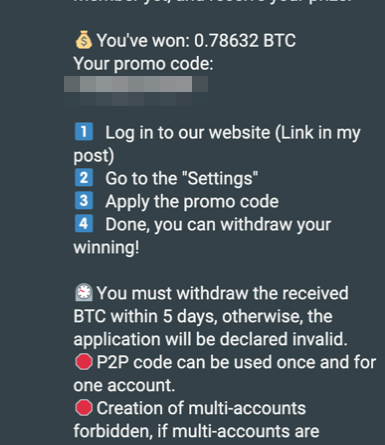
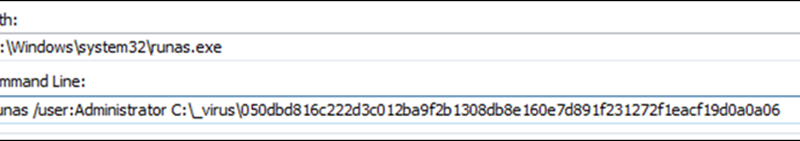
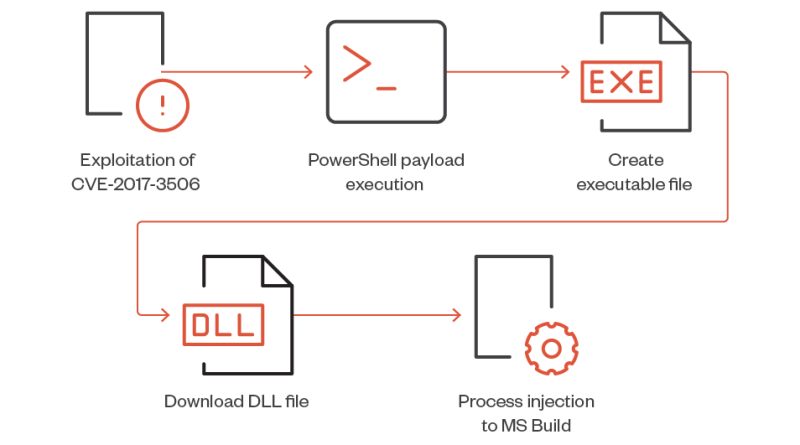
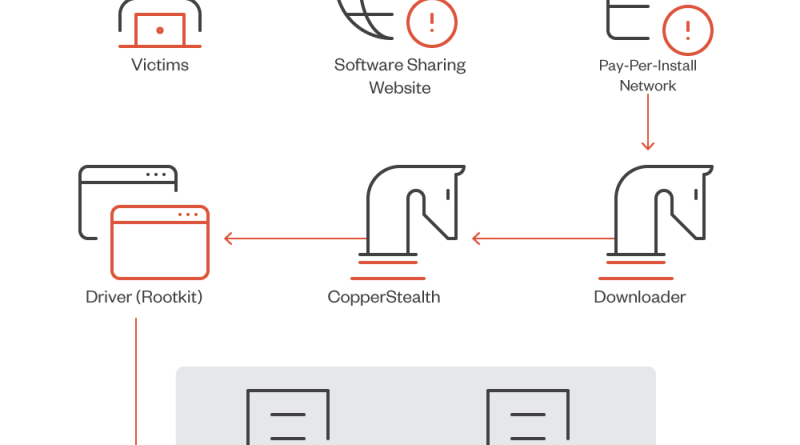
We have been able to uncover a massive cryptocurrency scam involving more than a thousand websites handled by different affiliates linked to a program called Impulse Project, run by a threat actor named Impulse Team. Read More HERE…