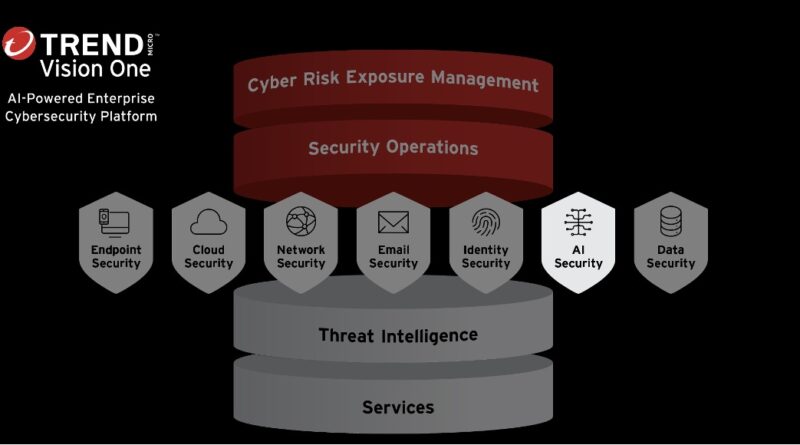
Trend Vision One™ Stacks Up Against Scattered Spider and Mustang Panda in 2025 MITRE ATT&CK® Evaluations
Enterprise 2025 introduces the first full cloud adversary emulation and expanded multi-platform testing, focusing on two advanced threat areas: Scattered Spider’s cloud-centric attacks and Mustang Panda’s long-term espionage operations. Read More HERE…