Microsoft open sources CodeQL queries used to hunt for Solorigate activity
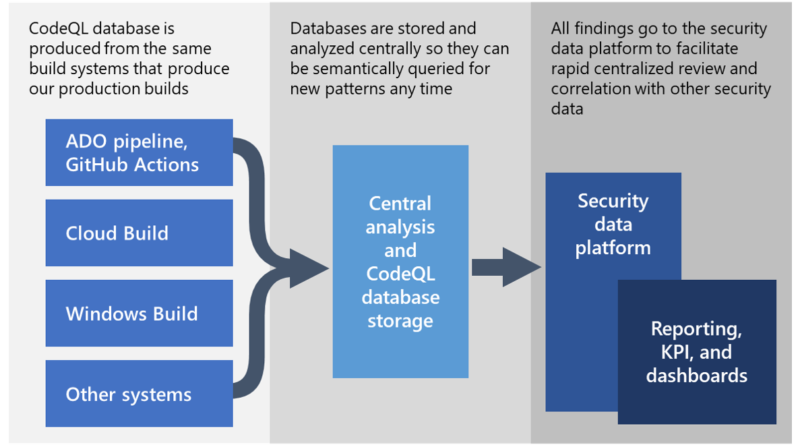
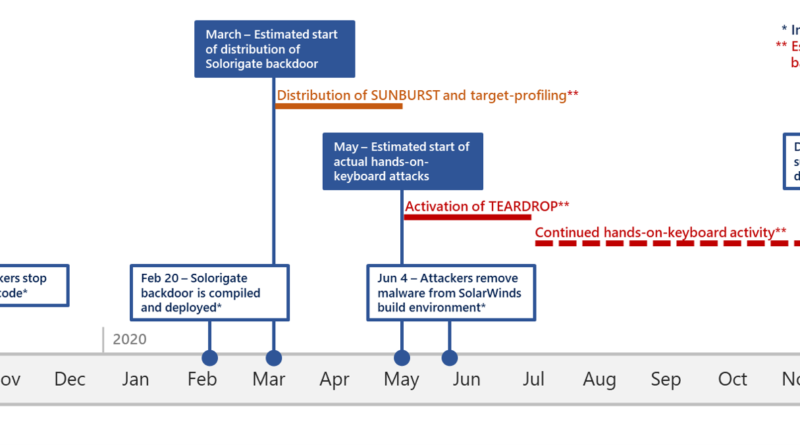
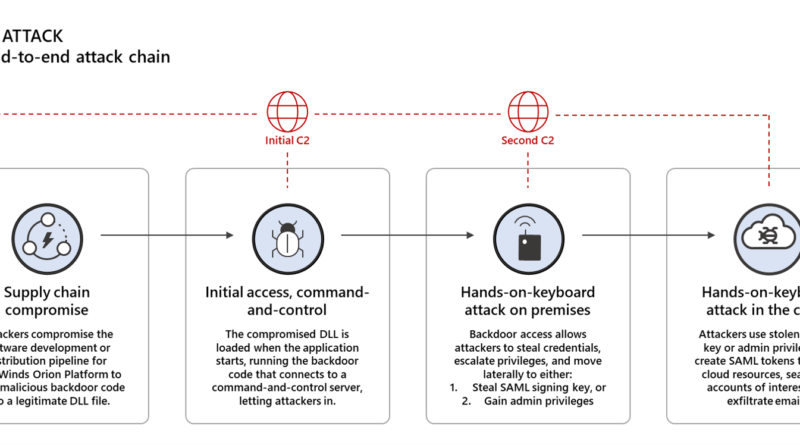
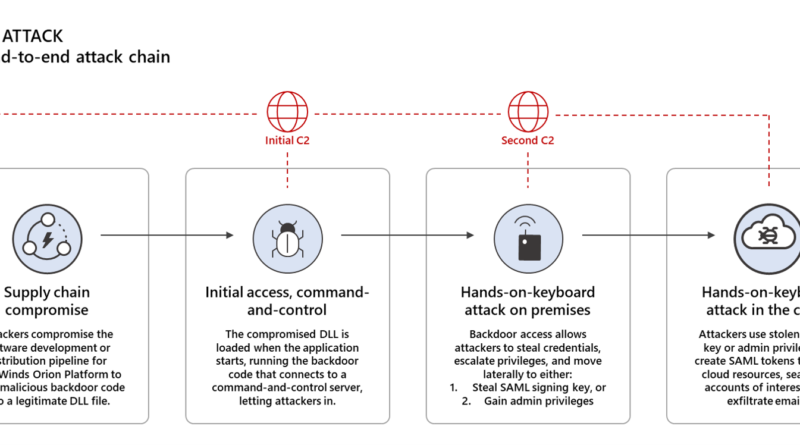
We are sharing the CodeQL queries that we used to analyze our source code at scale and rule out the presence of the code-level indicators of compromise (IoCs) and coding patterns associated with Solorigate so that other organizations may perform a similar analysis.
The post Microsoft open sources CodeQL queries used to hunt for Solorigate activity appeared first on Microsoft Security. READ MORE HERE…