How Windows Defender Antivirus integrates hardware-based system integrity for informed, extensive endpoint protection
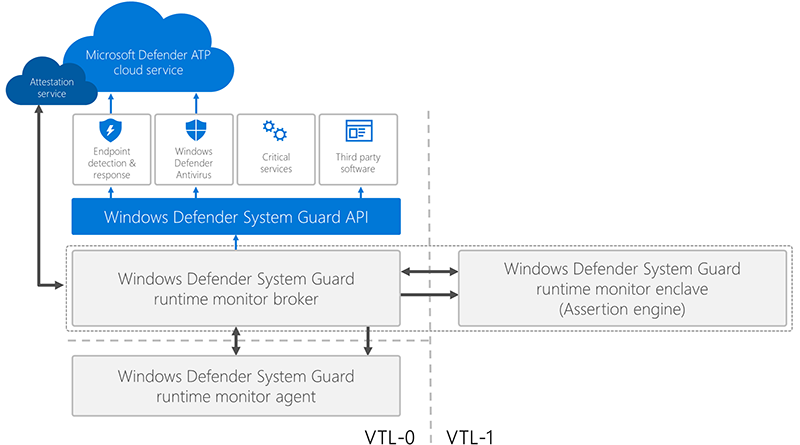
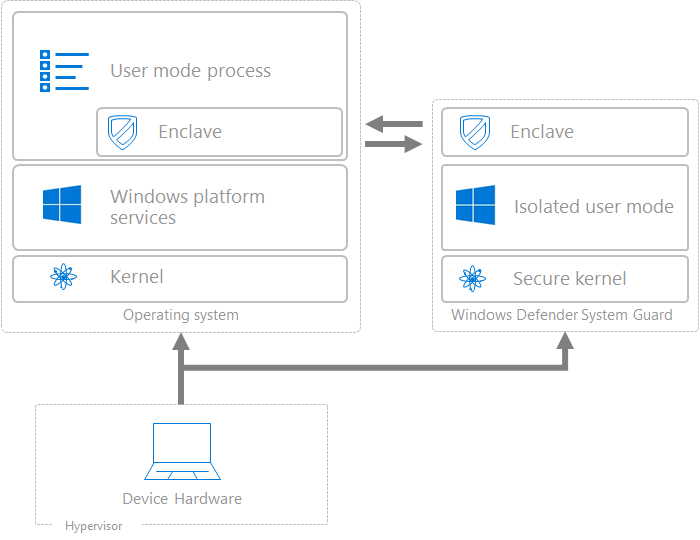
The deep integration of Windows Defender Antivirus with hardware-based isolation capabilities allows the detection of artifacts of attacks that tamper with kernel-mode agents at the hypervisor level.
The post How Windows Defender Antivirus integrates hardware-based system integrity for informed, extensive endpoint protection appeared first on Microsoft Security. READ MORE HERE…