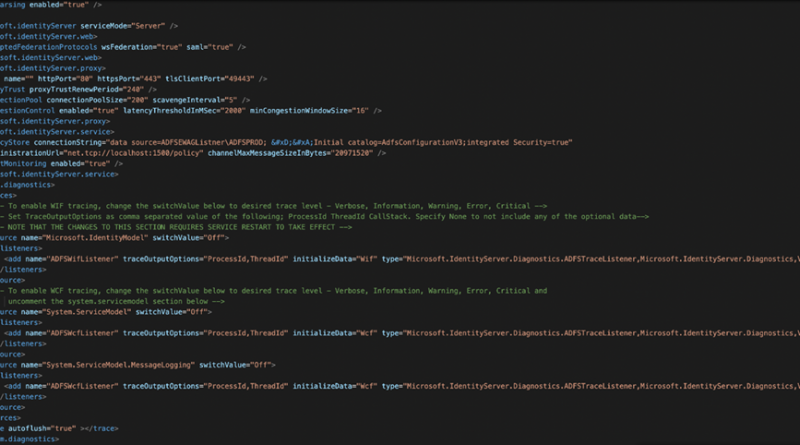
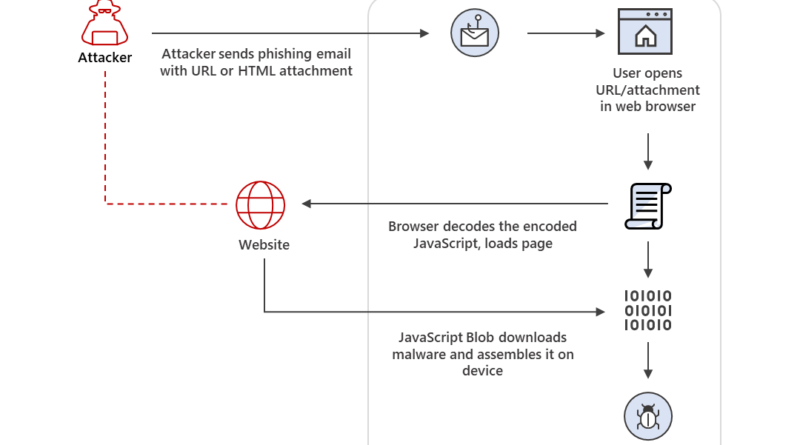
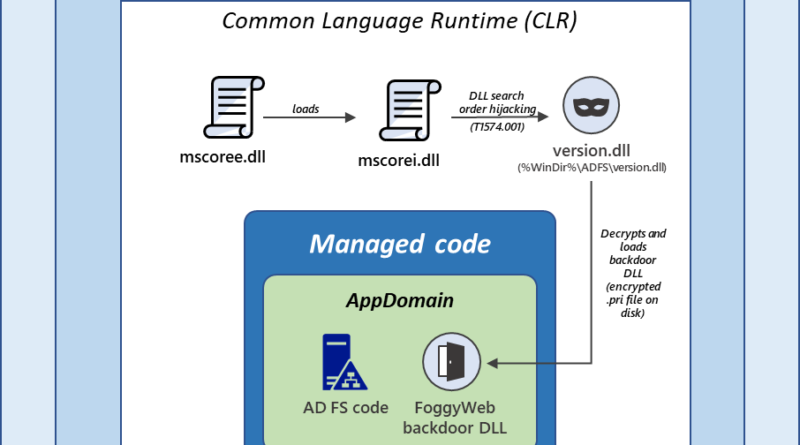
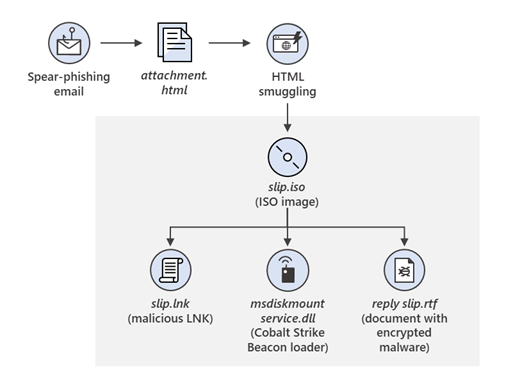
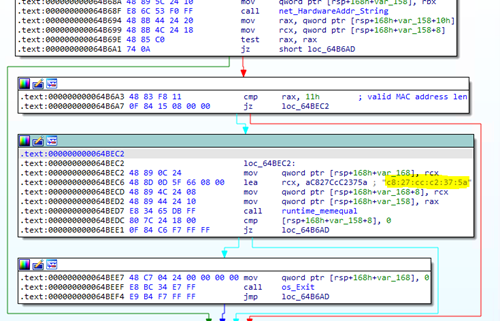
MagicWeb: NOBELIUM’s post-compromise trick to authenticate as anyone
Microsoft security researchers have discovered a post-compromise capability we’re calling MagicWeb, which is used by a threat actor we track as NOBELIUM to maintain persistent access to compromised environments.
The post MagicWeb: NOBELIUM’s post-compromise trick to authenticate as anyone appeared first on Microsoft Security Blog. READ MORE HERE…