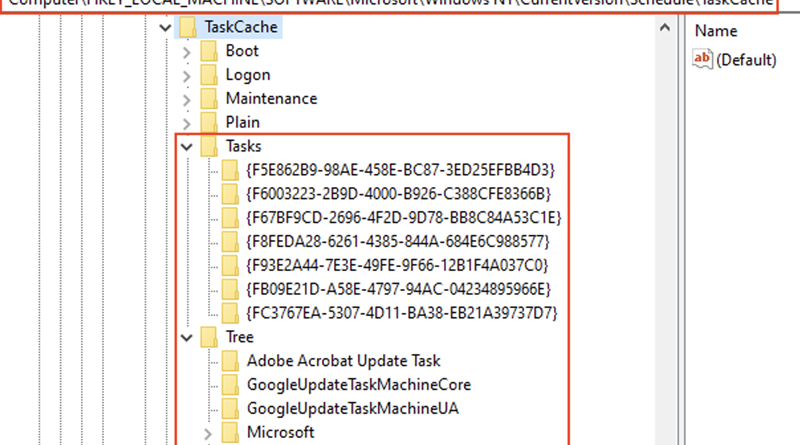
Tarrask malware uses scheduled tasks for defense evasion
Microsoft Detection and Response Team (DART) researchers have uncovered malware that creates “hidden” scheduled tasks as a defense evasion technique. In this post, we will demonstrate how threat actors create scheduled tasks, how they cover their tracks, and how the malware’s evasion techniques are used to maintain and ensure persistence on systems.
The post Tarrask malware uses scheduled tasks for defense evasion appeared first on Microsoft Security Blog. READ MORE HERE…