Dismantling a fileless campaign: Microsoft Defender ATP next-gen protection exposes Astaroth attack
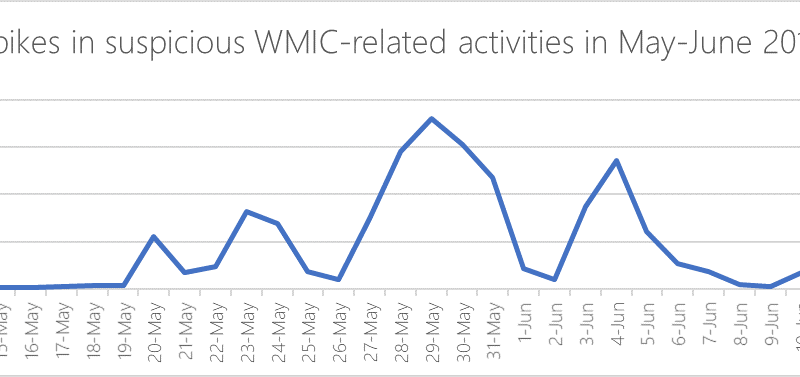
Advanced technologies in Microsoft Defender ATP next-generation protection exposed and defeated a widespread fileless campaign that completely “lived off the land” throughout a complex attack chain that run the info-stealing backdoor Astaroth directly in memory
The post Dismantling a fileless campaign: Microsoft Defender ATP next-gen protection exposes Astaroth attack appeared first on Microsoft Security. READ MORE HERE…