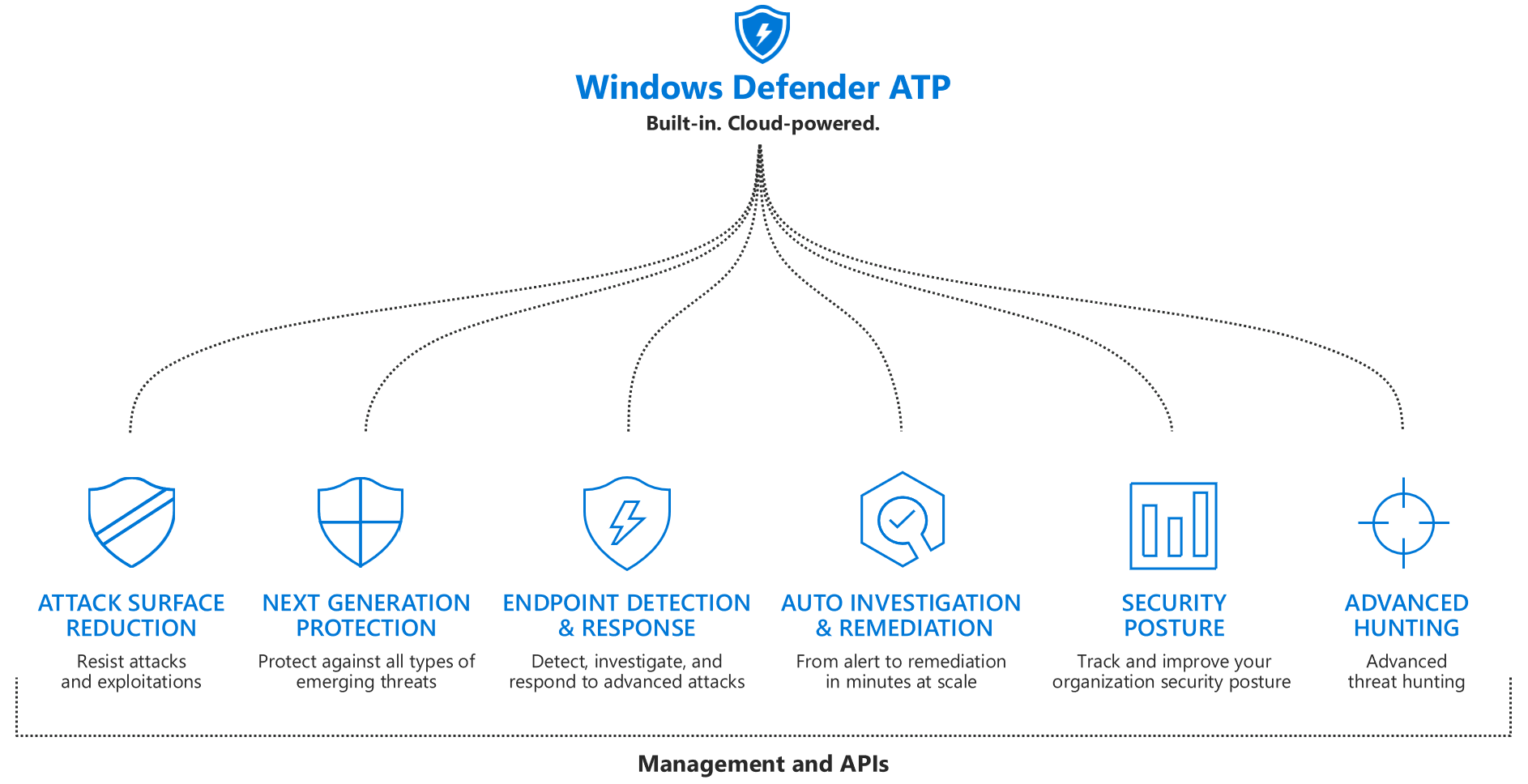
Step 1. Identify users: top 10 actions to secure your environment
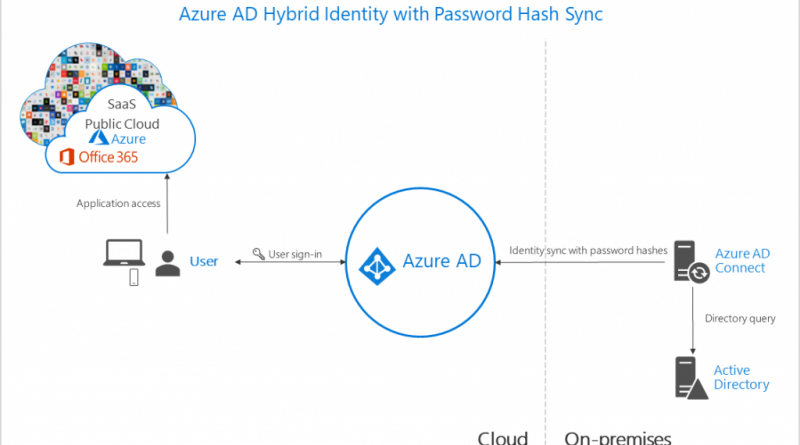
This series outlines the most fundamental steps you can take with your investment in Microsoft 365 security solutions. Well provide advice on activities such as setting up identity management through active directory, malware protection, and more. In this post, we explain how to create a single common identity across on-premises and cloud with hybrid authentication.
The post Step 1. Identify users: top 10 actions to secure your environment appeared first on Microsoft Secure. READ MORE HERE…