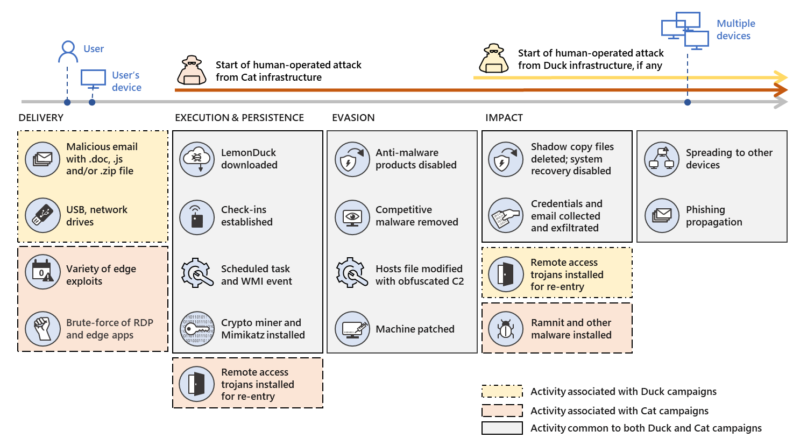
Trend-spotting email techniques: How modern phishing emails hide in plain sight
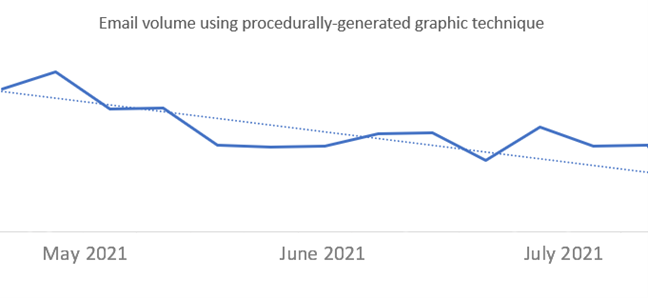
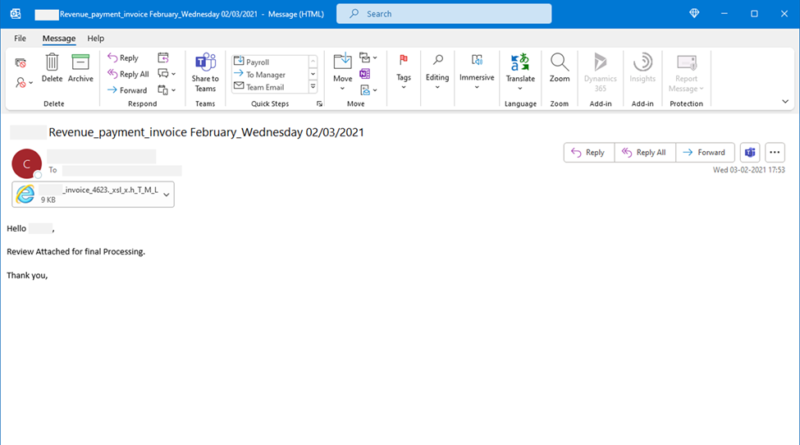
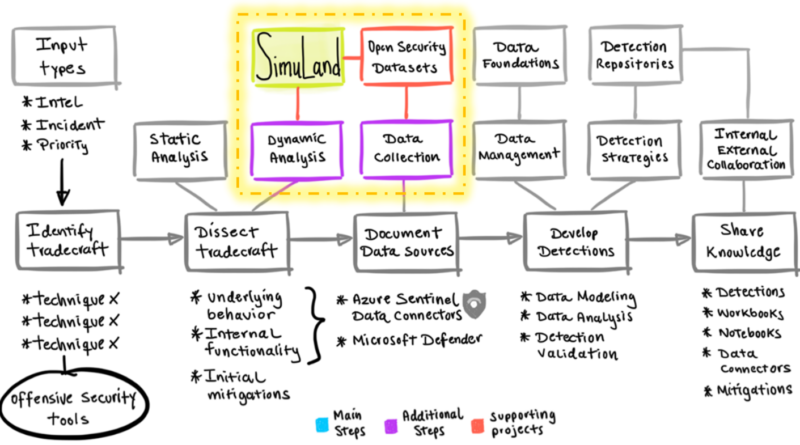
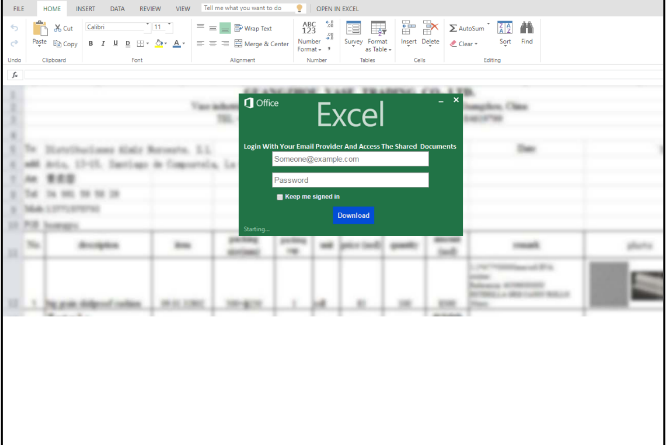
By spotting trends in the techniques used by attackers in phishing attacks, we can swiftly respond to attacks and use the knowledge to improve customer security and build comprehensive protections through Microsoft Defender for Office 365 and other solutions.
The post Trend-spotting email techniques: How modern phishing emails hide in plain sight appeared first on Microsoft Security Blog. READ MORE HERE…